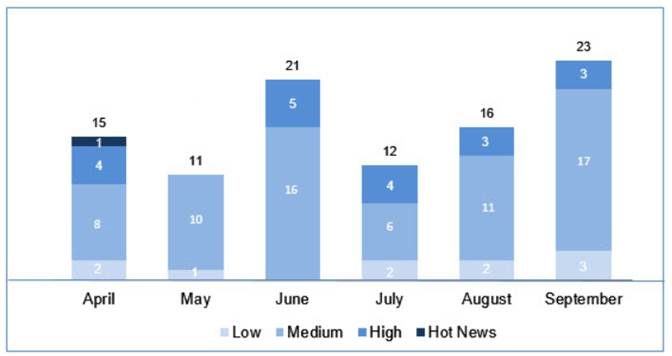
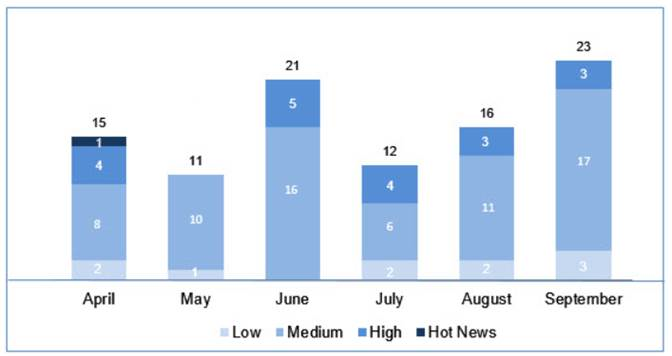
SAP has issued a total of 74 notes (Security Updates) in the third quarter of 2017 (51 from patches),
We would like to highlight that September was the fifth month in a row without Critical Priority (Hot News) notes, we certainly hope that is due to the fact that there are none, not because they have not been discovered yet.
- There were 23 notes issued in July. Two of the new notes have high priority, in addition to 2 update upgrades. The highest-value note (8.1) is “Lost authentication checks” that affect an SAP Retail Point of Sale (POS) Retail Xpress Server. The most prevalent type is “Lack of Authorization Verification” (including “Switchable Authorization Check” (7/23 and 2/12 in patch Tuesday), followed by leakage of information (“Information Revealed”).
- There were 20 notes issued in August . Three of the new notes have high priority. Two notes are low priority while the rest are medium priority (11 of Patch day). The most prevalent type is “Cross-Site Scripting – XSS” (5/20 and 3/16 in patch tuesday). 16 of the 20 notes are of automatic application.
- There were 32 notes issued in September. Three of the new notes have high priority. Three notes are low priority while the rest are medium priority (17 of Patch day). Of the total notes (23 patch Tuesday) we have the same number of “Cross-Site-Scripting – XSS” (8/32) than “Missing Authorization Check” (8/32), which would be 2 more if we include ” Switchable Authorization Check “.
The more relevant security updates in this quarter were:
- Malicious SAP Host Agent Shutdown without Authentication (2442993): SAP Host Agent is an agent that performs several management tasks, such as operating system and database monitoring, SAP instance discovery, inventory and provisioning, and several others. This patched vulnerability, could allow an attacker to remotely restart SAP Host Agent without authentication, having direct and high impact on availability. CVSS v3 Base Score: 7.5 / 10
- Missing Authentication checks in SAP Point of Sale (POS) Retail Xpress Server (2476601): The absence of a check for authentication leaves your SAP Xpress Server exposed to a possible attacker being able to reach it through the network, which could be the Internet. This note concerns a complex attack at its core. However, a smart attacker can operate silently and independently. Putting the confidentiality, availability and integrity of your data at the highest risk. The patch of the note is manual, although its web page might indicate differently. CVSS v3 Base Score: 8.1 / 10
- Improved security for outgoing HTTPS connections in SAP NetWeaver (2416119): This note was initially published in March and has received multiple cosmetic updates to its web page since. Due to the high severity of this note we recommend to use this update as a reminder to patch the note as soon as possible, if not yet performed. Manual steps are involved after patch installation, so be aware of usability issues if the certificates are not properly configured before implementation. CVSS v3 Base Score: 7.4 / 10
- Missing authorization-check in BC-SRV-ALV (1854252): This note also concerns an update, although not cosmetic like the previous note discussed. The patching of this note, together with automatic steps, requires a manual pre-implementation step. The note update for this month has added an additional software component release version to the list of releases requiring the pre-implementation step. Although this vulnerability has the lowest CVSS score in the list, exploiting it is easier than the others. Patching therefore is still recommended. Don’t forget to check if the updated release version applies to you. CVSS v3 Base Score: 6.0 / 10
- Code Injection vulnerability in Visual Composer (2376081): This specific vulnerability applies to iViews created in 04s versions. The vulnerability allows attackers to inject malicious code into the back end application. By simply having end users access a specially crafted URL, unwanted applications can be started on the client machine by an attacker. Depending on who makes use of your Enterprise Portal, clients in this sense could be employees, customers, partners or suppliers. The vulnerability is not intricate to exploit and affects additional systems beyond only the vulnerable one. CVSS v3 Base Score: 7.4 / 10
- Directory Traversal vulnerability in SAP NetWeaver AS Java Web Container (2486657): These types of attacks always affect the confidentiality of information, since it allows an attacker to read arbitrary files that shouldn’t be accessed. It’s high impact on confidentiality makes its CVSS score the highest of August. It is not critical however, since there is no impact on availability or integrity and an attack should be performed with privileges. AS Java Web Container without proper validation of path information could have impact due to an attacker reading content of arbitrary files on the remote server, exposing sensitive data. CVSS v3 Base Score: 7.7 / 10
- Cross-Site AJAX Requests vulnerability in SAP BusinessObjects (2381071): As has happened in the past, this vulnerability is not present in SAP itself but in a third-party Java library that is being used within BusinessObjects. The library has been updated to the fixed version in the latest Service Package. As with any Cross-Site attack, it could lead to client side attacks potentially affecting (with low impact) all confidentiality, availability and integrity of the information. CVSS v3 Base Score: 7.3 / 10
- Missing Authentication checks in SAP Point of Sale (POS) Retail Xpress Server (2476601): This is an update to a previous note already in this list. CVSS v3 Base Score: 8.1 / 10
- Missing Authentication checks in SAP Point of Sale (POS) Retail Xpress Server (2520064): This note is related to the previous (2476601), but it has more corrections than the original one, including not only added authentication but also added encryption of the communication channel. This note includes the bug described before (#2476601) so you will only need to install this last one. CVSS v3 Base Score: 8.1 / 10
- Cross-Site Request Forgery (CSRF) vulnerability in Electronic Ledger Management for Turkey 1.0 (2367269): In September there are two notes that each only affect a single country. As odd as it may seem, it makes complete sense: specific components and applications that only fit within regional or local invoicing/tax requirements can also have vulnerabilities. CVSS v3 Base Score: 7.6 / 10
For more information about the notes of each month, we strongly recommend to check the following links.
- SAP Security Patch July 2017
- Onapsis -SAP Security July 2017
- Incibe (CERT) – Seguridad Julio 2017
- SAP Security Patch August 2017
- Onapsis -SAP Security August 2017
- Incibe (CERT) – Seguridad Agosto 2017
- SAP Security Patch September 2017
- Onapsis -SAP Security September 2017
- Incibe (CERT) – Seguridad Septiembre 2017