Today we bring you the update of Q4 2019 SAP security notes.
Q4 2019 Notes
Summary and Highlights of the Quarter
We continue with a trend of a lower number of notes/patches with a new decrease in the total number, and also a large number of critical notes (Hot News), being 4 that we have to pay more attention to and one of them recurrent (7 updates in this year 2019). It is worth noting that in this quarter the lack of Missing Authorization Checks is the most repeated vulnerability, being the case of 10 of the 39 notes in total.
On the one hand, it is important that the ABAP code (or other type of code in other languages) contains adequate controls or checks to filter access and permissions according to authorizations and on the other hand, to have a good system and model for assigning these authorizations (permissions/roles) to users to ensure that only legitimate and authorized users have access to information and operate with it in a clearly controlled manner.
We have 4 unique critical notes (Hot News), being the total of 7 in this quarter, one of them the recurrent update for the SAP Business Client with Chromium with 2 appearances and another one of the “SAP Diagnostics Agent” of Solution Manager with 3 notes that we highlight below. In addition 3 high level highlights for the detailed review of a total of 7 notes to be reviewed.
- The most critical note (CVSS 9. 8), is a usual “Browser Control Chromium Delivered with SAP Business Client (2622660)” which appears in two months (November and December) and for the 7th and last time in the year.
- We also highlight a note for Solution Manager that we had already highlighted in the last quarterly report with CVSS of 9. 1 was published in November with 3 different notes that are very relevant too.
- Finally, of the other 2 criticisms, both from the first month (October) affect in the first case the AS2 adapter of SAP PI and in the second case SAP Landscape Management.
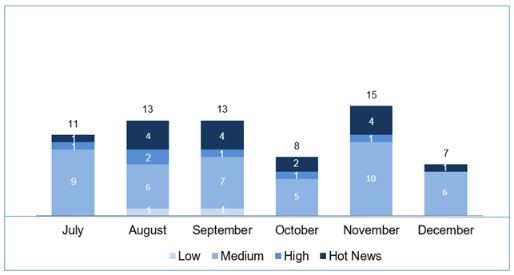
We have a total of 39 (10+16+13) notes for the entire quarter, 20 less than last quarter, (30 of the Tuesday patches, 7 less than last quarter):
- A total of 10 notes were released in October, 1 update and the remaining 9 new (8 in the Security Notes Tuesday – all 18 new).
- We have 2 “hot news” (critical), the highest being CVSS 9. 3 for SAP PI’s AS2 adapter and the other affecting SAP Landscape Management with a CVSS 9. 1.
- There is also 1 high priority note that affects a search algorithm used in several SAP products (SAP SQL Anywhere, SAP IQ and SAP Dynamic Tiering) that allows a variety of attack algorithms, but only with local access to the machine.
- This month the most predominant types are “Cross-Site Scripting (XSS)” (3/10 and 3/8 in patch day) and “Missing Authorization Check” (2/10 and 1/8 in patch day).
- A total of 16 notes were published in November (15 in the Security Notes Tuesday – 11 new and 4 updates to previous notes).
- Although we have a total of 4 “hot news” (critical), in reality we would be talking about only 2, since one of them (2839864) includes the other 2 being updates of notes from the previous quarter that affect the “SAP Diagnostics Agent” with CVSS of 9. 1. The other is the great classic “Browser Control Chromium Delivered with SAP Business Client (2622660)”, with its CVSS of 9. 8, with its 6th appearance so far this year.
- There are also 2 high priority notes, both with a CVSS of 7. 1, one for lack of XML validation in SAP BO BI and another for lack of Authorization Check affecting SAP Internet Princing Configurator (IPC).
- This month the most predominant types are “Missing Authorization Check” (4/16 and 3/15 in patch day) and “OS Command Injection” (3/16 and 3/15 in patch day).
- In December a total of 13 notes have been published (7 in the Security Notes Tuesday – 5 new and 2 updates of previous notes).
- The only “hot news” is the great classic “Browser Control Chromium Delivered with SAP Business Client (2622660)”, with its CVSS of 9. 8, with its 7th and last appearance in the year.
- There are no high level notes and all the others (12 notes) are all medium level. Although we do not highlight them here, it is always important to remember that we must have a process of reviewing all the notes, where we prioritize the installation of those with the greatest impact for us.
- This month the most predominant types are “Information Disclosure” (3/16 and 4/7 in patch day) and “Missing Authorization Check” (4/13 and 1/7 in patch day).
In the graph (post December 2019 of SAP) we can see the evolution and classification of the notes of the 3 months of the last quarter of the year (2019), in addition to the 3 months of the last quarter (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full detail
The full detail of the most relevant notes is as follows:
- Missing Authentication Check in AS2 Adapter of B2B Add-On for SAP NetWeaver Process Integration (2826015): The AS2 adapter is used in SAP PI for communicating with business partners. It allows the secure transmission of business documents via HTTP and S/MIME over the Internet. The adapter specifies a comprehensive set of data security features, specifically data confidentiality and data authenticity, which are aimed at the B2B commerce environment. The configuration of the AS2 adapter allows two different security providers. Depending on the selected provider, a Missing Authentication vulnerability exists that can lead to sensitive data theft or data manipulation as well as to access to administrative and other privileged functionalities. For more information on the affected security provider, check the corresponding Security Note. CVSS v3 Base Score: 9.3 / 10 (CVE-2019-0379).
- Information Disclosure vulnerability in SAP Landscape Management Enterprise (2828682): SAP Landscape Management Enterprise allows the definition of custom operations, such as database refreshes. There is a provider assigned to each custom operation that contains information about the used script and other properties. You can also add further custom parameters to such a provider. SAP Security Note #2828682 talks about a risk of information disclosure if these custom parameters fulfill specific conditions. SAP describes the overall conditions for the existence of the vulnerability as “uncommon”. Nevertheless, it is rated with a CVSS score of 9.1 as the possible impact with regard to confidentiality, integrity, and availability is high. CVSS v3 Base Score: 9.1 / 10 (CVE-2019-0380).
- Binary Planting vulnerability in SAP SQL Anywhere, SAP IQ and SAP Dynamic Tiering (2792430): Describes a common vulnerability in the file search algorithm of these products. The algorithm searches too many directories, even if they are out of the application scope. Possible impacts are path traversals and directory climbings, enabling an attacker to read, overwrite, delete, and expose arbitrary files of the system. This can also lead to DLL hijacking as well as to privilege elevation. The only reason for not being a CVSS 9+ candidate is the fact that an attacker must have access to the local system in order to exploit the vulnerability. CVSS v3 Base Score: 7.8 / 10 (CVE-2019-0381).
- SAP Business Client has a security vulnerability (2622660): This note bundles multiple vulnerabilities. The bugs concern vulnerabilities in web browser controls that are used to display pages in SAP Business Client 6.5 PL5. Web browser controls are programmable building blocks that software developers use to embed web pages in their applications. Depending on the vulnerability, attackers can exploit a Memory corruption vulnerability for injecting specially crafted code into a working memory which will be executed by the vulnerable application. This can lead to taking complete control of an application, denial of service, command execution and other attacks. This fact has a negative influence on business processes and business reputation as a result. Install this SAP Security Note to prevent the risks. Updated in November & December 2019 (“If this note has been already implemented, then there is no action required.” Manual steps only have usability impact and no security implications). CVSS v3 Base Score: 9.8 / 10
- OS Command Injection vulnerability in SAP Diagnostics Agent (2839864 – updates to 2823733and 2808158): New multiple bypasses have been found for SAP Diagnostics Agent over the defined whitelist for Linux/Unix systems, taking advantage of other pre-crafted commands allowed, with several payloads and ways to exploit this vulnerability. This could also allow an attacker to delete, modify or even execute arbitrary commands on the agent. Based on this, SAP has released this month a new note covering all reported scenarios and allowing customers that didn’t patch before only to apply this last released note (#2839864). SAP has published new patches for Support Packages 6 to 9, and also provides manual steps for patching for older versions. With the latest patch, it is now the customer’s responsibility to maintain commands whitelist, and after applying the patch some diagnostic tasks may stop working since SAP is now replacing the file with a limited amount of commands allowed. It is also the customer’s responsibility to decide which OS commands should be allowed, and you may need to add some of them manually if you have been using it. CVSS v3 Base Score: 9.1 / 10 (CVE-2019-0330).
- Missing XML Validation vulnerability in SAP BusinessObjects Business Intelligence Platform (Web Intelligence HTML interface) (2814007): Describes the introduction of additional XML validation in SAP Business Objects Business Intelligence Platform as XML documents from untrusted sources were not correctly filtered for malicious content in some specific workflows. Among others, insufficient XML validation can lead to information disclosure as well as to complete system outages due to denial-of-service attacks. Fix for eCatt Service in SAP NW AS JAVA. CVSS v3 Base Score: 7.1 / 10 (CVE-2019-0396).
- VMC Authority Check (2393937): addresses a vulnerability in SAP Internet Pricing Configurator (IPC) that can also often be found in customer code. Some RFC enabled function modules were only protected by authority checks on object S_RFC. Due to the complex nature of SAP installations, there usually exists a significant number of users with S_RFC * privileges and thus they automatically have access to all remote enabled function modules, that do not contain explicit authorization checks related to the business context of the function module. SAP has fixed this issue for a set of important IPC-function modules through the introduction of a new switchable authorization scenario, thus allowing customers a smooth transition to more detailed and context related authorization checks. CVSS v3 Base Score: 7.1 / 10
Reference Links:
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=528123050
https://www.onapsis.com/blog/sap-security-notes-october-19-only-nine-new-notes-two-hotnews
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=528880390
https://www.onapsis.com/SAP-patch-day-nov-2019
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=533660397
https://www.onapsis.com/blog/sap-security-notes-dec-2019-chromium
Resources affected
- S4HANA Sales (S4CORE), versiones 1.0, 1.01, 1.02, 1.03 y 1.04;
- SAP Adaptive Server Enterprise, versiones 15.7 y 16.0;
- SAP BusinessObjects Business Intelligence Platform (Fiori BI Launchpad), versión 4.2;
- SAP BusinessObjects Business Intelligence Platform (Monitoring Application), versiones 4.1, 4.2 y 4.3.
- SAP BusinessObjects Business Intelligence Platform (Web Intelligence HTML interface), versiones 4.1, 4.2 y 4.3;
- SAP Business Client, versión 6.5;
- SAP Customer Relationship Management (Email Management):
- S4CRM, versiones 100 y 200;
- BBPCRM, versiones 700, 701, 702, 712, 713 y 714.
- SAP Diagnostic Agent (LM-Service), versión 7.20;
- SAP Dynamic Tiering, versiones 1.0 y 2.0;
- SAP Enable Now, versiones anteriores a la 1908 y versión 1911;
- SAP ERP HCM (SAP_HRCES), versión 3;
- SAP Financial Consolidation, versiones 10.0 y 10.1;
- SAP IQ, versión 16.1;
- SAP Kernel (RFC):
- KRNL32NUC, KRNL32UC y KRNL64NUC, versiones 7.21, 7.21EXT, 7.22 y 7.22EXT;
- KRNL64UC, versiones 7.21, 7.21EXT, 7.22, 7.22EXT, 7.49 y 7.73;
- KERNEL, versiones 7.21, 7.49, 7.53, 7.73 y 7.76.
- SAP Landscape Management enterprise edition, versión 3.0;
- SAP NetWeaver Application Server Java (J2EE-Framework), versiones – 7.1, 7.2, 7.3, 7.31, 7.4 y 7.5;
- SAP NetWeaver AS Java, versiones 7.10, 7.20, 7.30, 7.31, 7.4 y 7.5;
- SAP NetWeaver Process Integration:
- AS2 Adapter, versiones 1.0 y 2.0;
- B2B Toolkit, versiones 1.0 y 2.0.
- SAP Portfolio and Project Management, versiones S4CORE 102, 103, EPPM 100, CPRXRPM 500_702, 600_740 y 610_740;
- SAP Quality Management (S4CORE), versiones 1.0, 1.01, 1.02 y 1.03;
- SAP SQL Anywhere, versión 17.0;
- SAP Treasury and Risk Management (EA-FINSERV), versiones 6.0, 6.03, 6.04, 6.05, 6.06, 6.16, 6.17, 6.18 y 8.0;
- SAP Treasury and Risk Management (S4CORE), versiones 1.01, 1.02, 1.03 y 1.04;
- SAP UI 700, versión 2.0
Q4 2019 Notes
Summary and Highlights of the Quarter
We continue with a trend of a lower number of notes/patches with a new decrease in the total number, and also a large number of critical notes (Hot News), being 4 that we have to pay more attention to and one of them recurrent (7 updates in this year 2019). It is worth noting that in this quarter the lack of Missing Authorization Checks is the most repeated vulnerability, being the case of 10 of the 39 notes in total.
On the one hand, it is important that the ABAP code (or other type of code in other languages) contains adequate controls or checks to filter access and permissions according to authorizations and on the other hand, to have a good system and model for assigning these authorizations (permissions/roles) to users to ensure that only legitimate and authorized users have access to information and operate with it in a clearly controlled manner. We have 4 unique critical notes (Hot News), being the total of 7 in this quarter, one of them the recurrent update for the SAP Business Client with Chromium with 2 appearances and another one of the “SAP Diagnostics Agent” of Solution Manager with 3 notes that we highlight below. In addition 3 high level highlights for the detailed review of a total of 7 notes to be reviewed.
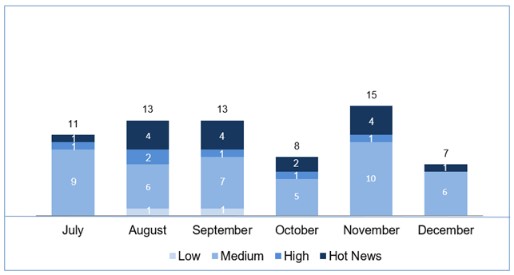
The most critical note (CVSS 9. 8), is a usual “Browser Control Chromium Delivered with SAP Business Client (2622660)” which appears in two months (November and December) and for the 7th and last time in the year. We also highlight a note for Solution Manager that we had already highlighted in the last quarterly report with CVSS of 9. 1 was published in November with 3 different notes that are very relevant too. Finally, of the other 2 criticisms, both from the first month (October) affect in the first case the AS2 adapter of SAP PI and in the second case SAP Landscape Management. We have a total of 39 (10+16+13) notes for the entire quarter, 20 less than last quarter, (30 of the Tuesday patches, 7 less than last quarter): A total of 10 notes were released in October, 1 update and the remaining 9 new (8 in the Security Notes Tuesday – all 18 new).
We have 2 “hot news” (critical), the highest being CVSS 9. 3 for SAP PI’s AS2 adapter and the other affecting SAP Landscape Management with a CVSS 9. 1. There is also 1 high priority note that affects a search algorithm used in several SAP products (SAP SQL Anywhere, SAP IQ and SAP Dynamic Tiering) that allows a variety of attack algorithms, but only with local access to the machine. This month the most predominant types are “Cross-Site Scripting (XSS)” (3/10 and 3/8 in patch day) and “Missing Authorization Check” (2/10 and 1/8 in patch day). A total of 16 notes were published in November (15 in the Security Notes Tuesday – 11 new and 4 updates to previous notes). Although we have a total of 4 “hot news” (critical), in reality we would be talking about only 2, since one of them (2839864) includes the other 2 being updates of notes from the previous quarter that affect the “SAP Diagnostics Agent” with CVSS of 9. 1. The other is the great classic “Browser Control Chromium Delivered with SAP Business Client (2622660)”, with its CVSS of 9. 8, with its 6th appearance so far this year. There are also 2 high priority notes, both with a CVSS of 7. 1, one for lack of XML validation in SAP BO BI and another for lack of Authorization Check affecting SAP Internet Princing Configurator (IPC). This month the most predominant types are “Missing Authorization Check” (4/16 and 3/15 in patch day) and “OS Command Injection” (3/16 and 3/15 in patch day). In December a total of 13 notes have been published (7 in the Security Notes Tuesday – 5 new and 2 updates of previous notes). The only “hot news” is the great classic “Browser Control Chromium Delivered with SAP Business Client (2622660)”, with its CVSS of 9. 8, with its 7th and last appearance in the year. There are no high level notes and all the others (12 notes) are all medium level. Although we do not highlight them here, it is always important to remember that we must have a process of reviewing all the notes, where we prioritize the installation of those with the greatest impact for us. This month the most predominant types are “Information Disclosure” (3/16 and 4/7 in patch day) and “Missing Authorization Check” (4/13 and 1/7 in patch day). In the graph (post December 2019 of SAP) we can see the evolution and classification of the notes of the 3 months of the last quarter of the year (2019), in addition to the 3 months of the last quarter (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full detail
The full detail of the most relevant notes is as follows:
- Missing Authentication Check in AS2 Adapter of B2B Add-On for SAP NetWeaver Process Integration (2826015): The AS2 adapter is used in SAP PI for communicating with business partners. It allows the secure transmission of business documents via HTTP and S/MIME over the Internet. The adapter specifies a comprehensive set of data security features, specifically data confidentiality and data authenticity, which are aimed at the B2B commerce environment. The configuration of the AS2 adapter allows two different security providers. Depending on the selected provider, a Missing Authentication vulnerability exists that can lead to sensitive data theft or data manipulation as well as to access to administrative and other privileged functionalities. For more information on the affected security provider, check the corresponding Security Note. CVSS v3 Base Score: 9.3 / 10 (CVE-2019-0379).
- Information Disclosure vulnerability in SAP Landscape Management Enterprise (2828682): SAP Landscape Management Enterprise allows the definition of custom operations, such as database refreshes. There is a provider assigned to each custom operation that contains information about the used script and other properties. You can also add further custom parameters to such a provider. SAP Security Note #2828682 talks about a risk of information disclosure if these custom parameters fulfill specific conditions. SAP describes the overall conditions for the existence of the vulnerability as “uncommon”. Nevertheless, it is rated with a CVSS score of 9.1 as the possible impact with regard to confidentiality, integrity, and availability is high. CVSS v3 Base Score: 9.1 / 10 (CVE-2019-0380).
- Binary Planting vulnerability in SAP SQL Anywhere, SAP IQ and SAP Dynamic Tiering (2792430): Describes a common vulnerability in the file search algorithm of these products. The algorithm searches too many directories, even if they are out of the application scope. Possible impacts are path traversals and directory climbings, enabling an attacker to read, overwrite, delete, and expose arbitrary files of the system. This can also lead to DLL hijacking as well as to privilege elevation. The only reason for not being a CVSS 9+ candidate is the fact that an attacker must have access to the local system in order to exploit the vulnerability. CVSS v3 Base Score: 7.8 / 10 (CVE-2019-0381).
- SAP Business Client has a security vulnerability (2622660): This note bundles multiple vulnerabilities. The bugs concern vulnerabilities in web browser controls that are used to display pages in SAP Business Client 6.5 PL5. Web browser controls are programmable building blocks that software developers use to embed web pages in their applications. Depending on the vulnerability, attackers can exploit a Memory corruption vulnerability for injecting specially crafted code into a working memory which will be executed by the vulnerable application. This can lead to taking complete control of an application, denial of service, command execution and other attacks. This fact has a negative influence on business processes and business reputation as a result. Install this SAP Security Note to prevent the risks. Updated in November & December 2019 (“If this note has been already implemented, then there is no action required.” Manual steps only have usability impact and no security implications). CVSS v3 Base Score: 9.8 / 10
- OS Command Injection vulnerability in SAP Diagnostics Agent (2839864 – updates to 2823733and 2808158): New multiple bypasses have been found for SAP Diagnostics Agent over the defined whitelist for Linux/Unix systems, taking advantage of other pre-crafted commands allowed, with several payloads and ways to exploit this vulnerability. This could also allow an attacker to delete, modify or even execute arbitrary commands on the agent. Based on this, SAP has released this month a new note covering all reported scenarios and allowing customers that didn’t patch before only to apply this last released note (#2839864). SAP has published new patches for Support Packages 6 to 9, and also provides manual steps for patching for older versions. With the latest patch, it is now the customer’s responsibility to maintain commands whitelist, and after applying the patch some diagnostic tasks may stop working since SAP is now replacing the file with a limited amount of commands allowed. It is also the customer’s responsibility to decide which OS commands should be allowed, and you may need to add some of them manually if you have been using it. CVSS v3 Base Score: 9.1 / 10 (CVE-2019-0330).
- Missing XML Validation vulnerability in SAP BusinessObjects Business Intelligence Platform (Web Intelligence HTML interface) (2814007): Describes the introduction of additional XML validation in SAP Business Objects Business Intelligence Platform as XML documents from untrusted sources were not correctly filtered for malicious content in some specific workflows. Among others, insufficient XML validation can lead to information disclosure as well as to complete system outages due to denial-of-service attacks. Fix for eCatt Service in SAP NW AS JAVA. CVSS v3 Base Score: 7.1 / 10 (CVE-2019-0396).
- VMC Authority Check (2393937): addresses a vulnerability in SAP Internet Pricing Configurator (IPC) that can also often be found in customer code. Some RFC enabled function modules were only protected by authority checks on object S_RFC. Due to the complex nature of SAP installations, there usually exists a significant number of users with S_RFC * privileges and thus they automatically have access to all remote enabled function modules, that do not contain explicit authorization checks related to the business context of the function module. SAP has fixed this issue for a set of important IPC-function modules through the introduction of a new switchable authorization scenario, thus allowing customers a smooth transition to more detailed and context related authorization checks. CVSS v3 Base Score: 7.1 / 10
Reference Links:
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=528123050
https://www.onapsis.com/blog/sap-security-notes-october-19-only-nine-new-notes-two-hotnews
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=528880390
https://www.onapsis.com/SAP-patch-day-nov-2019
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=533660397
https://www.onapsis.com/blog/sap-security-notes-dec-2019-chromium
Resources affected
- S4HANA Sales (S4CORE), versiones 1.0, 1.01, 1.02, 1.03 y 1.04;
- SAP Adaptive Server Enterprise, versiones 15.7 y 16.0;
- SAP BusinessObjects Business Intelligence Platform (Fiori BI Launchpad), versión 4.2;
- SAP BusinessObjects Business Intelligence Platform (Monitoring Application), versiones 4.1, 4.2 y 4.3.
- SAP BusinessObjects Business Intelligence Platform (Web Intelligence HTML interface), versiones 4.1, 4.2 y 4.3;
- SAP Business Client, versión 6.5;
- SAP Customer Relationship Management (Email Management):
- S4CRM, versiones 100 y 200;
- BBPCRM, versiones 700, 701, 702, 712, 713 y 714.
- SAP Diagnostic Agent (LM-Service), versión 7.20;
- SAP Dynamic Tiering, versiones 1.0 y 2.0;
- SAP Enable Now, versiones anteriores a la 1908 y versión 1911;
- SAP ERP HCM (SAP_HRCES), versión 3;
- SAP Financial Consolidation, versiones 10.0 y 10.1;
- SAP IQ, versión 16.1;
- SAP Kernel (RFC):
- KRNL32NUC, KRNL32UC y KRNL64NUC, versiones 7.21, 7.21EXT, 7.22 y 7.22EXT;
- KRNL64UC, versiones 7.21, 7.21EXT, 7.22, 7.22EXT, 7.49 y 7.73;
- KERNEL, versiones 7.21, 7.49, 7.53, 7.73 y 7.76.
- SAP Landscape Management enterprise edition, versión 3.0;
- SAP NetWeaver Application Server Java (J2EE-Framework), versiones – 7.1, 7.2, 7.3, 7.31, 7.4 y 7.5;
- SAP NetWeaver AS Java, versiones 7.10, 7.20, 7.30, 7.31, 7.4 y 7.5;
- SAP NetWeaver Process Integration:
- AS2 Adapter, versiones 1.0 y 2.0;
- B2B Toolkit, versiones 1.0 y 2.0.
- SAP Portfolio and Project Management, versiones S4CORE 102, 103, EPPM 100, CPRXRPM 500_702, 600_740 y 610_740;
- SAP Quality Management (S4CORE), versiones 1.0, 1.01, 1.02 y 1.03;
- SAP SQL Anywhere, versión 17.0;
- SAP Treasury and Risk Management (EA-FINSERV), versiones 6.0, 6.03, 6.04, 6.05, 6.06, 6.16, 6.17, 6.18 y 8.0;
- SAP Treasury and Risk Management (S4CORE), versiones 1.01, 1.02, 1.03 y 1.04;
- SAP UI 700, versión 2.0