Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas mayo 2024
Resumen y highlights del Mes
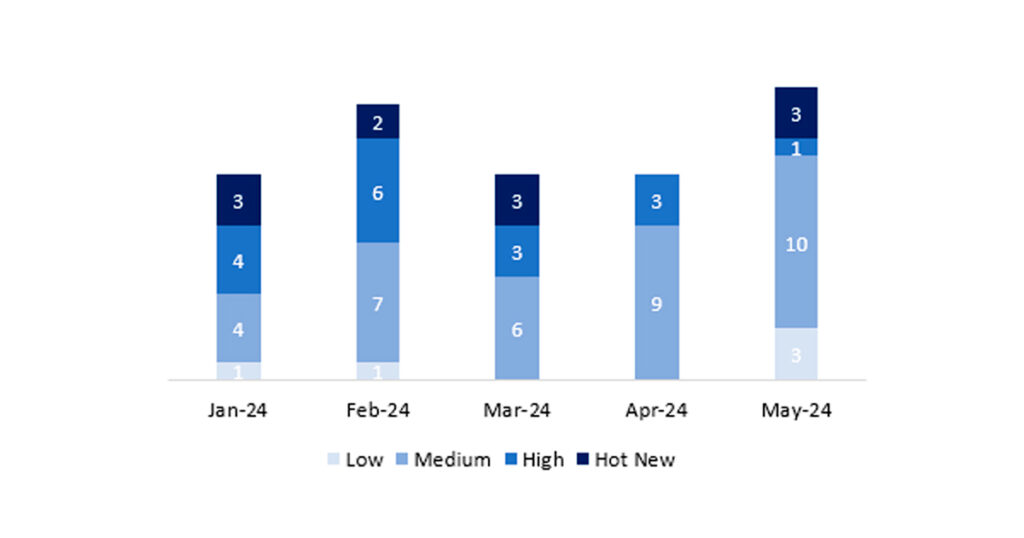
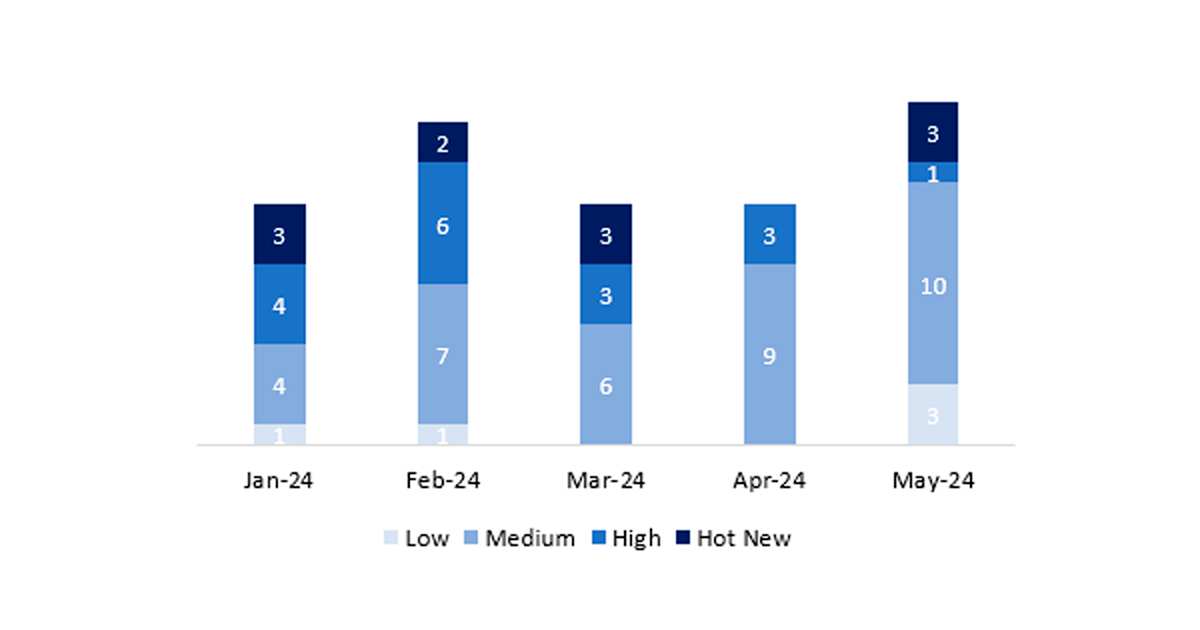
El número total de notas/parches ha sido de 17, 5 más que el mes pasado. El número de Hot News ha sido de 3, 3 más que el mes pasado, puesto que en abril no hubo ninguna. Por otro lado, cabe destacar que el número de notas de criticidad alta ha disminuido con respecto al mes pasado: 1 en este mes. Como siempre dejaremos las notas medias y bajas sin revisar, pero daremos detalle de un total de 4 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 17 notas para todo el mes (las 17 del patch Tuesday, 14 nuevas y 3 actualizaciones).
Revisaremos en detalle un total de 4 notas, las 3 HotNews de este mes: 2 nuevas y 1 actualización y la nota alta, la cual es nueva (aquellas de CVSS mayor o igual a 7)
- La nota más crítica del mes (con CVSS 10) es una actualización de una Hot News relacionada con “Security updates for the browser control Google Chromium delivered with SAP Business Client”.
- La siguiente en criticidad (CVSS 9,8) es una Hot News relacionada con “Multiple vulnerabilities in SAP CX Commerce”.
- La siguiente en criticidad (CVSS 9,6) es una Hot News relacionada con “File upload vulnerability in SAP NetWeaver Application Server ABAP and ABAP Platform”.
- La siguiente en criticidad (CVSS 8,1) es una nota alta relacionada con “Cross site scripting vulnerability in SAP BusinessObjects Business Intelligence Platform”.
- Este mes el tipo más predominante es relacionado con “Missing Authorization check in SAP: in different modules” (4/17 en patch day).
En la gráfica podemos ver la clasificación de las notas de mayo, además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the Chromium web browser control used within SAP Business Client. The Chromium web browser version will be updated periodically to address emerging security threats. Security fixes are provided along with SAP Business Client patches, and the priority of these updates is determined by the severity of the vulnerabilities patched. If SAP Business Client is not updated with the latest patches, viewing web pages through this Chromium browser could expose the system to a variety of threats, such as memory corruption or disclosure of sensitive information. These vulnerabilities could affect the confidentiality, integrity and availability of the system, and could even lead to system crashes or the collection of information for more serious attacks in the future. The proposed solution implies that each new SAP Business Client patch includes the latest stable version of the Chromium browser control, previously validated by SAP. Furthermore, it is recommended to apply additional security measures according to the official SAP Business Client documentation, specifically in the security settings section for the Chromium browser control. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Multiple vulnerabilities in SAP CX Commerce (1455438): This security note identifies two vulnerabilities in CX Commerce: In Swagger UI, which allows CSS injection, making it possible for attackers to use the Relative Path Overwrite (RPO) technique on CSS-based input fields, which can compromise the security and availability of the application and in remote code execution in SAP CX Commerce: Due to incorrect initialization in Apache Calcite Avatica 1. 18.0, HTTP client instances can be created based on class names provided through a connection property (httpclient_impl) without checking if the class implements the expected interface. This can allow malicious code to be executed on the system. As a solution, SAP removed a vulnerable test extension and released an update to address these vulnerabilities in CX Commerce. CVSS v3 Base Score: 9,8 / 10 [CVE-2019-17495].
- File upload vulnerability in SAP NetWeaver Application Server ABAP and ABAP Platform (3448171): An unauthenticated attacker can upload a malicious file to the server. When a victim accesses this file, the attacker can completely compromise the system. This flaw is due to the insecure configuration of the “FILESYSTEM” and “SOMU_DB” content repositories, which are configured with the “No signature” option enabled. To solve this problem, a new secure default configuration is implemented to prevent this type of attacks. CVSS v3 Base Score: 9,6/ 10 [CVE-2024-33006].
- Cross site scripting vulnerability in SAP BusinessObjects Business Intelligence Platform (3431794): SAP Business Objects Business Intelligence Platform has a stored XSS vulnerability. This allows an attacker to manipulate a parameter in the Opendocument URL, which could compromise the confidentiality and integrity of the application. The recommended solution is to sanitize the user input parameter in the Opendocument URL. In addition, the support packages and patches mentioned in this SAP security note are urged to be implemented to mitigate this security risk. CVSS v3 Base Score: 8,1/ 10 [CVE-2024-28165].
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (mayo):
SAP Patch Day: May 2024 – Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP Business Client, Versions – 6.5, 7.0, 7.70
- SAP Commerce, Version – HY_COM 2205
- SAP NetWeaver Application Server ABAP and ABAP Platform, Versions – SAP_BASIS 700, SAP_BASIS 701, SAP_BASIS 702, SAP_BASIS 731, SAP_BASIS 740, SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758
- SAP BusinessObjects (Business Intelligence Platform), Versions – 430, 440
- SAP Enable Now, Version – 1704
- SAP NetWeaver Application server for ABAP and ABAP Platform, Versions – SAP_BASIS 700, SAP_BASIS 701, SAP_BASIS 702, SAP_BASIS 731, SAP_BASIS 740, SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758, SAP_BASIS 795, SAP_BASIS 796
- SAP NetWeaver Application Server ABAP and ABAP Platform, Versions – SAP_BASIS 740, SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758
- SAP S/4HANA (Document Service Handler for DPS), Versions – SAP_BASIS 740, SAP_BASIS 750
- My Travel Requests, Version – 600
- SAP Process Integration, Versions – MESSAGING 7.31, MESSAGING 7.40, MESSAGING 7.50, NWCEIDE 7.31, SAP_XIESR 7.31, SAP_XIESR 7.40, SAP_XIESR 7.50, SAP_XITOOL 7.31, SAP_XITOOL 7.40, SAP_XITOOL 7.50, SAP_XIAF 7.31, SAP_XIAF 7.40, SAP_XIAF 7.50, SAP_XIGUILIB 7.31, SAP_XIGUILIB 7.40, SAP_XIGUILIB 7.50
- SAP Replication Server, Versions – 16.0, 16.0.3, 16.0.4
- SAP S/4 HANA (Manage Bank Statement Reprocessing Rules), Versions – SAPSCORE 131, S4CORE 105, S4CORE 106, S4CORE107, S4CORE 108
- SAP BusinessObjects Business Intelligence Platform (Webservices), Versions – 430, 440
- SAP Process Integration, Versions – MESSAGING 7.10, MESSAGING 7.11, MESSAGING 7.30, MESSAGING 7.31, MESSAGING 7.40, MESSAGING 7.50, NWCEIDE 7.31, SAP_XITOOL 7.00, SAP_XITOOL 7.01, SAP_XITOOL 7.02, SAP_XITOOL 7.10, SAP_XITOOL 7.11, SAP_XITOOL 7.30, SAP_XITOOL 7.31, SAP_XITOOL 7.40, SAP_XITOOL 7.50, SAP_XIAF 7.31, SAP_XIAF 7.40, SAP_XIAF 7.50, SAP_XIPCK 7.00, SAP_XIPCK 7.01, SAP_XIPCK 7.02, SAP_XIPCK 7.10, SAP_XIPCK 7.11, SAP_XIPCK 7.30
- SAP Global Label Management (GLM), Versions – 605, 606, 616, 617
- SAP Bank Account Management, Versions – 100, 101, 102, 103, 104, 105, 106, 107, 108
- SAPUI5, Versions – 754, 755, 756, 757, 758