Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas marzo 2024
Resumen y highlights del Mes
El número total de notas/parches ha sido de 12, 4 menos que el mes pasado. El número de Hot News ha sido de 3, 1 más que el mes pasado. Por otro lado, cabe destacar que el número de notas de criticidad alta ha disminuido con respecto al mes pasado: 3 en este mes. Como siempre dejaremos las notas medias y bajas sin revisar, pero daremos detalle de un total de 6 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 12 notas para todo el mes (las 12 del patch Tuesday, 10 nuevas y 2 actualizaciones, son 4 notas menos que el pasado patch Tuesday).
Revisaremos en detalle un total de 6 notas, las 3 HotNews de este mes: 2 nuevas y 1 actualización y las 3 notas altas: 2 de ellas nuevas y 1 actualización (aquellas de CVSS mayor o igual a 7).
- La nota más crítica del mes (con CVSS 10) es una actualización de un HotNews habitual relacionado con “Google Chromium”.
- La siguiente en criticidad (CVSS 9,4) es un HotNews relacionado con “Code Injection vulnerability in applications built with SAP Build Apps”.
- La siguiente en criticidad (con CVSS 9,1), es un HotNews relacionado con “Code Injection vulnerability in SAP NetWeaver AS Java”
- Las siguiente en criticidad (con CVSS 8,8) se trata de una actualización de una nota relacionada con “Improper authentication in SAP Commerce Cloud”.
- Las siguientes en criticidad (con CVSS 7,5 y 7,2 respectivamente) están relacionadas con “Denial of service (DOS) in SAP HANA XS Classic and HANA XS Advanced” y “Path Traversal Vulnerability in SAP BusinessObjects Business Intelligence Platform (Central Management Console)”.
- Este mes el tipo más predominante es relacionado con “Information Disclosure vulnerability” (3/12 en patch day).
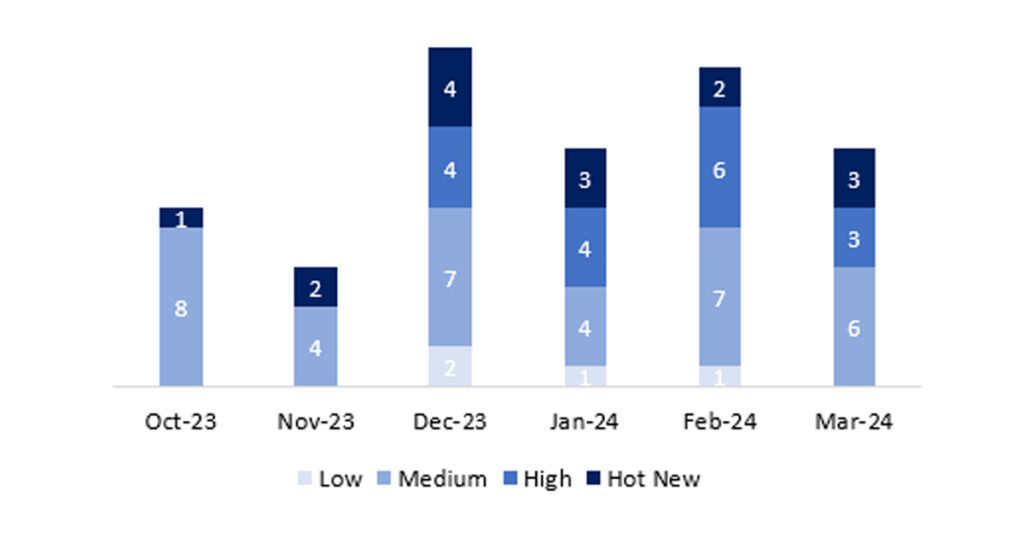
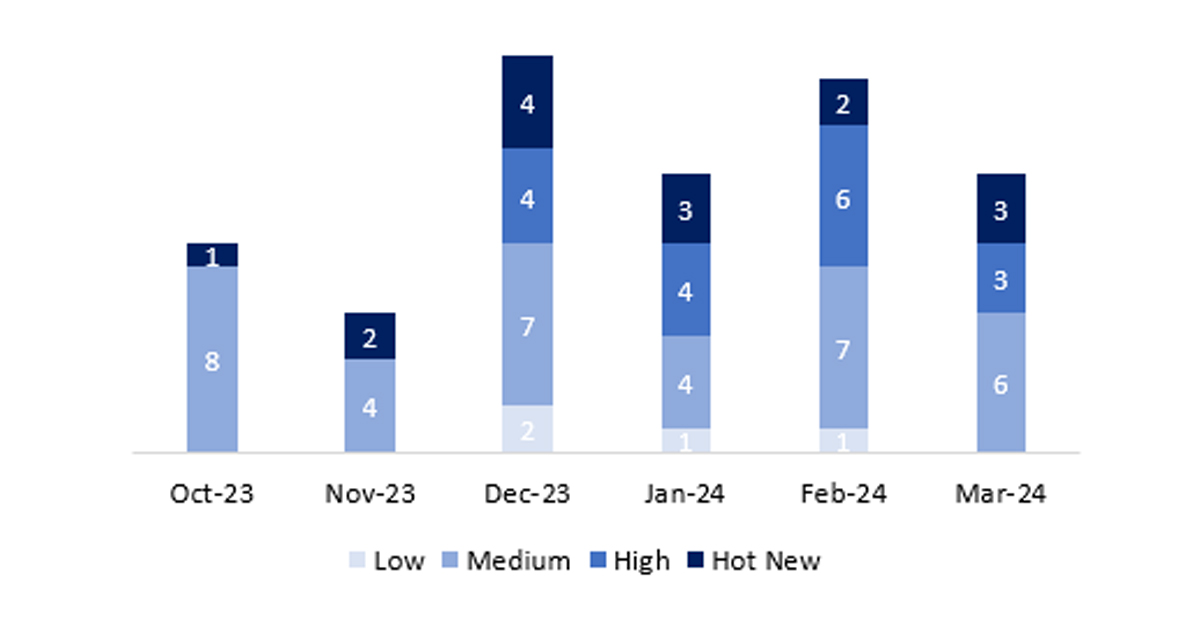
En la gráfica podemos ver la clasificación de las notas de marzo, además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Update -Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open-source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. The note has been re-released with updated ‘Solution’ and ‘Support Packages & Patches’ information. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Code Injection vulnerability in applications built with SAP Build Apps (3425274): SAP Build Apps applications have a code injection vulnerability, allowing attackers to execute unauthorized commands. This can affect the confidentiality (low impact) and the integrity and availability (high impact) of the application. The solution is to rebuild the application in SAP Build Apps with version 4.9.145 or later. CVSS v3 Base Score: 9,4 / 10 [CVE-2019-10744].
- Code Injection vulnerability in SAP NetWeaver AS Java (Administrator Log Viewer plug-in) (3433192): The SAP NetWeaver Administrator AS Java Log Viewer add-on has a vulnerability that allows an attacker with elevated privileges to load potentially dangerous files, which can result in a command injection, leading to data compromise and impacting system availability. The solution involves restricting the types of files that can be uploaded after applying the Note. It is recommended to scan each file for threats and upgrade NW Application Server Java to a version or SP that addresses this issue.CVSS v3 Base Score: 9,1 / 10 [CVE-2024-22127].
- Update – Improper authentication in SAP Commerce Cloud (3346500): Certain configurations of SAP Commerce Cloud may accept an empty passphrase for user ID and passphrase authentication, allowing users to log into the system without a passphrase. This vulnerability only affects active user accounts that have an empty passphrase. Other user accounts that have a valid passphrase set are not affected. Note contains a workaround.CVSS v3 Base Score: 8,8 / 10 [CVE-2023-39439].
- Denial of service (DOS) in SAP HANA XS Classic and HANA XS Advanced (3410615): SAP HANA XS Classic and HANA XS Advanced are vulnerable to a denial of service (DOS) attack through a flood of HTTP/2 requests by an unauthenticated user. This attack can cause a significant impact on application availability, without affecting the confidentiality or integrity of the application. The solution for SAP HANA Database 2.0 is to implement revision 2.00.59.12 or newer, while for SAP HANA Extended Application Services Advanced (XS Advanced), it is recommended to implement version 1.1.8 or newer. CVSS v3 Base Score: 7,5 / 10 [CVE-2023-44487].
- Code Injection vulnerability in SAP IDES Systems (3414195):SAP BusinessObjects Business Intelligence Platform CMC employs a vulnerable version of Apache Struts, susceptible to CVE-2023-50164. A user with elevated privileges could exploit this vulnerability, causing a high impact on the confidentiality, integrity and availability of the application. The solution involves upgrading the affected open-source library to a non-vulnerable version. CVSS v3 Base Score: 7,2 / 10 [CVE-2023-50164].
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (marzo):
SAP Patch Day: March 2024 – Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP Business Client, Versions – 6.5, 7.0, 7.70
- SAP Build Apps, Versions < 4.9.145
- SAP NetWeaver AS Java (Administrator Log Viewer plug-in), Version – 7.50
- SAP Commerce, Versions – HY_COM 2105, HY_COM 2205, COM_CLOUD 2211
- SAP HANA Database, Version – 2.0
- SAP HANA Extended Application Services Advanced (XS Advanced), Version – 1.0
- SAP BusinessObjects Business Intelligence Platform (Central Management Console), Versions – 4.3
- SAP NetWeaver AS ABAP applications based on SAPGUI for HTML (WebGUI), Versions – 7.89, 7.93
- NetWeaver (WSRM), Versions – 7.50
- SAP NetWeaver (Enterprise Portal), Version – 7.50
- SAP NetWeaver Process Integration (Support Web Pages), Versions – 7.50
- SAP Fiori Front End Server, Version – 605
- SAP ABAP Platform, Versions – 758, 795