Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Junio 2022
Resumen y highlights del Mes
El número total de notas/parches se ha mantenido con respecto al último mes. Además de esta igualdad en el número de notas totales, el número de Hot News disminuyen, siendo 4 las que encontrábamos el mes pasado con respecto a la única existente en junio. Por otro lado, cabe destacar, que aumentan el número de notas de criticidad alta pasando de 2 a 3 en este mes. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 4 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 17 notas para todo el mes, exactamente las mismas que el pasado Mayo (12 del patch Tuesday, 10 nuevas y 2 actualizaciones, siendo las mismas que el pasado mes).
Tenemos únicamente una nota crítica (Hot News), siendo ésta una actualización, en este mes, que destaca por su alto CVVS. Además revisaremos en detalle 3 del total de 3 notas altas nuevas (aquellas de CVSS mayor o igual a 7).
- Las nota más crítica del mes (con CVSS 10) es la habitual nota relacionada con “Google Chromium”.
- La siguientes en criticidad (CVSS 8,6, 8,2 y 7,8) son tres notas altas, una de “Improper Access Control of SAProuter for SAP NetWeaver and ABAP Platform”, otra relacionada con “Improper Access Control check in SAP Netweaver AS JAVA”, y la última que estaría relacionado con “Potential privilege escalation in SAP PowerDesigner Proxy 16.7”.
- El resto (9) son de nivel medio y bajo, y no las veremos en detalle, aunque cabe destacar que hay más de una que afecta a SAP NetWeaver.
- Este mes los tipos más predominantes son “Privilege Escalation vulnerability” (4/17 y 4/12 en patch day) y “Missing Authorization Check” (3/17 y 1/12 en patch day).
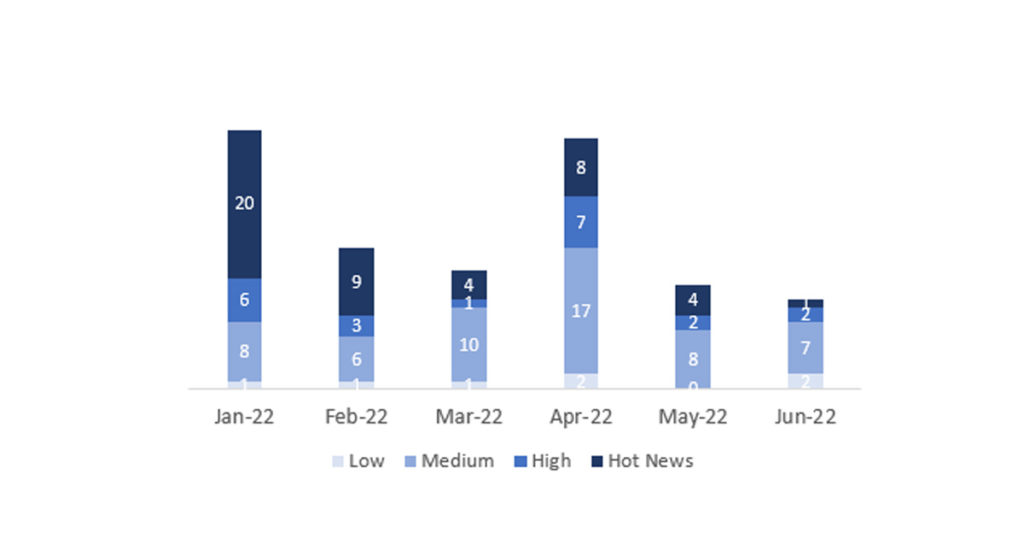
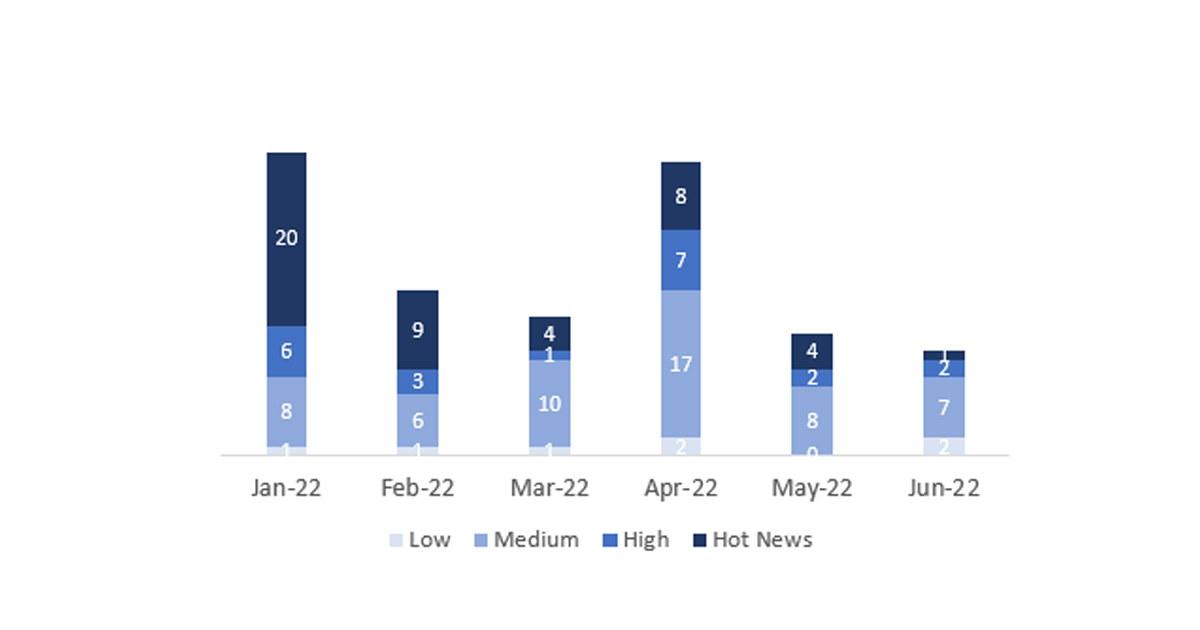
En la gráfica (post Junio 2022 de SAP) podemos ver la clasificación de las notas de Junio además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Improper Access Control of SAProuter for SAP NetWeaver and ABAP Platform (3158375): Depending on the configuration of the route permission table in file “saprouttab”, it is possible for an unauthenticated attacker to execute SAProuter administration commands in SAP NetWeaver and ABAP Platform, from a remote client, for example stopping the SAProuter, that could highly impact systems availability. SAProuter is designed to restrict administration commands to clients that run on the same host as SAProuter. Administration commands should not be allowed from remote clients. The correction is contained in SAProuter, it is delivered in the following components on SAP Service Marketplace: SAPROUTER versions 7.53 and 7.22, and in the Package saprouter.sar in the SAP KERNEL versions 7.85, 7.81 and 7.77. Nevertheless, it is recommended to use SAPROUTER version 7.53. Keep in mind that the correction will be delivered in future versions of SP stack kernel SAPEXE.SAR, but it will not be available in SAPEXE.SAR in all versions when this SAP note is published. CVSS v3 Base Score: 8,6 / 10 (CVE-2022-27668).
- Improper Access Control check in SAP NetWeaver basicadmin and adminadapter services (3147498): Improper Access Control is detected in SAP NetWeaver AS Java, basicadmin and adminadapter services remote objects are not properly protected. As a result, some administrative functionalities are exposed to public access, which means the Availability could be impacted. This correction discontinues public access to basicadmin and adminadapter services remote objects by introducing required authentication and authorization protection. To solve the issue, please apply the corrective measure according to the “Support Packages & Patches” section of the note.. CVSS v3 Base Score: 8,2 / 10.
- Potential privilege escalation in SAP PowerDesigner Proxy 16.7 (3197005): SAP PowerDesigner Proxy, allows an attacker with low privileges and has local access, with the ability to work around system’s root disk access restrictions to Write/Create a program file on system disk root path, which could then be executed with elevated privileges of the application during application start up or reboot, potentially compromising Confidentiality, Integrity and Availability of the system. This issue when “SAP PowerDesigner Proxy 16.7” SP05 up to including PL2 is installed. To solve the issue, the action would be to upgrade the “SAP PowerDesigner Proxy 16.7” to version SP05 PL03 or higher. CVSS v3 Base Score: 7.8 / 10 (CVE-2022-31590).
Enlaces de referencia
Enlaces de referencia del CERT del INCIBE en relación a la publicación de las notas para el mes de Junio:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-junio-2022
Otras referencias, en inglés de SAP y Onapsis (junio):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP 3D Visual Enterprise Viewer, versión 9.0;
- SAP Adaptive Server Enterprise (ASE), versiones -KERNEL 7.22, 7.49, 7.53, KRNL64NUC 7.22, 7.22EXT, 7.49, KRNL64UC 7.22, 7.22EXT, 7.49, 7.53;
- SAP Business Client, versión 6.5;
- SAP ERP, localization for CEEcountries, versiones -C-CEE110_600, 110_602, 110_603, 110_604, 110_700;
- SAP Financials, versiones -SAP_FIN 618, 720;
- SAP Host Agent, versión – 7.22;
- SAP NetWeaver Application Server for ABAP and ABAP Platform, versiones -700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755, 756, 787, 788;
- SAP NetWeaver AS ABAP, AS Java, and HANA Database, versiones -KERNEL 7.22, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87, 7.88, KRNL64NUC 7.22, 7.22EXT, 7.49, KRNL64UC 7.22, 7.22EXT, 7.49, 7.53;
- SAP NetWeaver and ABAP Platform, versiones -KERNEL 7.22, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87, 7.88, 8.04, KRNL64NUC .22, 7.22EXT, 7.49, KRNL64UC 7.22, 7.22EXT, 7.49, 7.53, 8.04, SAP_ROUTER 7.53, 7.22;
- SAP NetWeaver Developer Studio (NWDS), versión -7.50;
- SAP NetWeaver Development Infrastructure (Design Time Repository), versiones -7.30, 7.31, 7.40, 7.50;
- SAP PowerDesigner Proxy 16.7;
- SAP S/4Hana Core, versiones -S4CORE 100, 101, 102, 103, 104, 105, 106, 107, 108;