Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas febrero 2024
Resumen y highlights del Mes
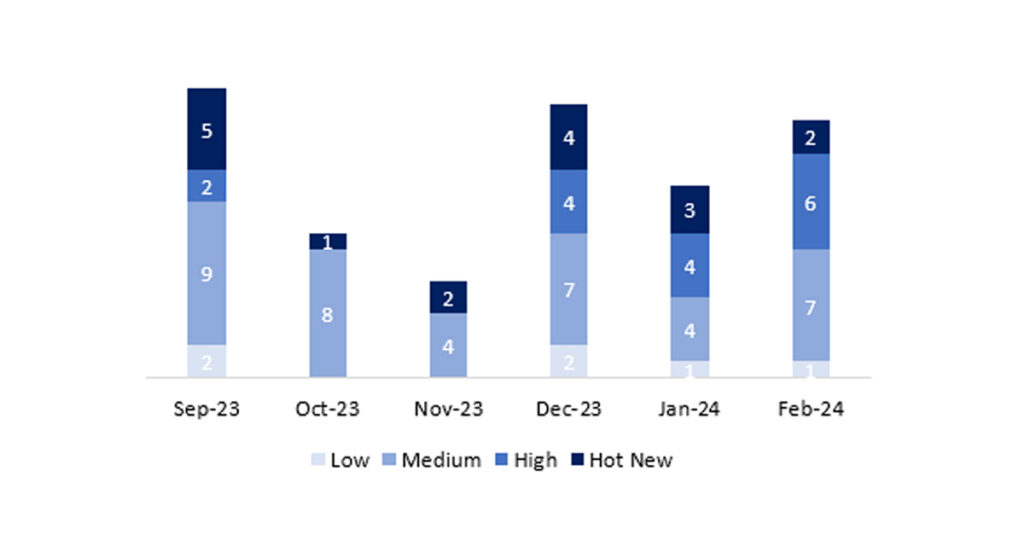
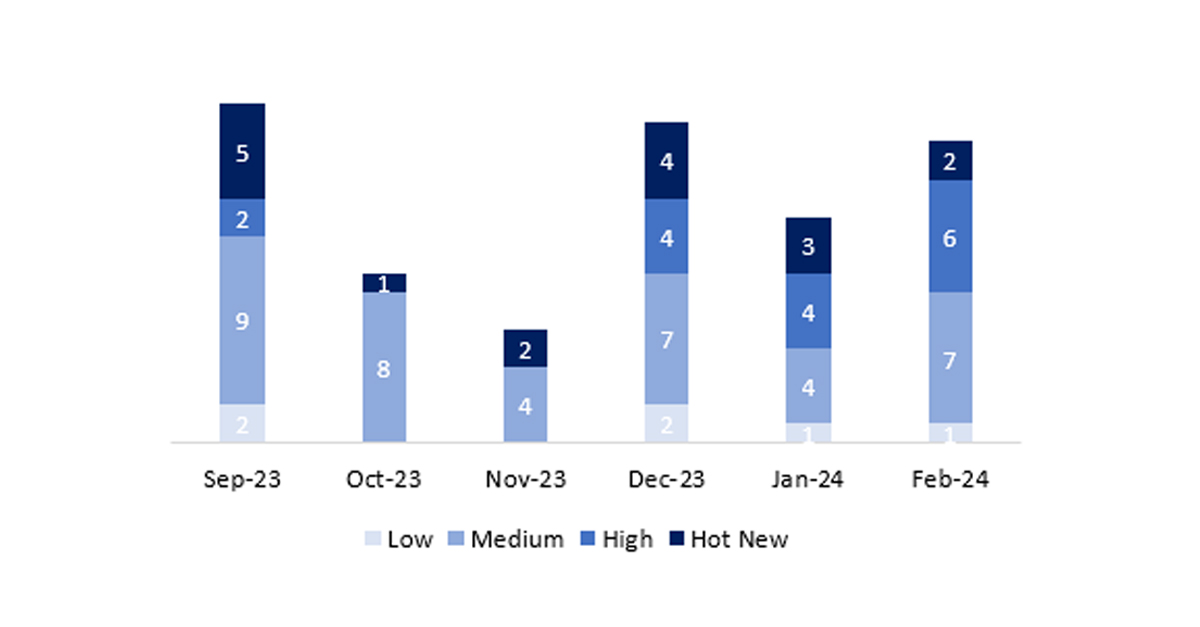
El número total de notas/parches ha sido de 16, 4 más que el mes pasado. El número de Hot News ha sido de 2, 1 menos que el mes pasado. Por otro lado, cabe destacar que el número de notas de criticidad alta ha aumentado con respecto al mes pasado: 6 en este mes. Como siempre dejaremos las notas medias y bajas sin revisar, pero daremos detalle de un total de 8 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 16 notas para todo el mes (las 16 del patch Tuesday, 13 nuevas y 3 actualizaciones, son 4 notas más que el pasado patch Tuesday).
Revisaremos en detalle un total de 8 notas, las 2 HotNews de este mes: 1 nueva y 1 actualización y las 6 notas altas: 5 de ellas nuevas y 1 actualización (aquellas de CVSS mayor o igual a 7).
- La nota más crítica del mes (con CVSS 10) es una actualización de la nota habitual relacionada con “Google Chromium”.
- La siguiente en criticidad (CVSS 9,1) es un HotNews relacionada con “Code Injection vulnerability in SAP ABA (Application Basis)”.
- La siguiente en criticidad (con CVSS 8,8), es una nota alta relacionada con “Cross Site Scripting vulnerability in NetWeaver AS Java (User Admin Application)”
- Las siguiente en criticidad (con CVSS 8,6) se trata de una nota alta relacionada con “XXE vulnerability in SAP NetWeaver AS Java (Guided Procedures)”.
- Las siguientes en criticidad (con CVSS 7,6, 7,3 y 7,3 respectivamente) están relacionadas con “Cross-Site Scripting (XSS) vulnerability in SAP CRM (WebClient UI)”, “Code Injection vulnerability in SAP IDES Systems“, “Improper Certificate Validation in SAP Cloud Connector” y “ Information disclosure vulnerability in SAP GUI for WIndows and SAP GUI for Java”.
- Este mes el tipo más predominante es relacionado con “Cross-Site Scripting (XSS)” (5/16 en patch day).
En la gráfica podemos ver la clasificación de las notas de febrero, además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Update -Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open-source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. The note has been re-released with updated ‘Solution’ and ‘Support Packages & Patches’ information. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Code Injection vulnerability in SAP ABA (Application Basis) (3420923): An authenticated attacker can exploit a vulnerable interface to perform unauthorized actions, which could compromise data and affect system availability; it is recommended to implement additional measures besides securing the S_RFC authorization object to mitigate this risk in CA-SUR. The solution is to implement support package or remediation instructions. CVSS v3 Base Score: 9,1 / 10 [CVE-2024-22131].
- Cross Site Scripting vulnerability in NetWeaver AS Java (User Admin Application) (3417627): SAP NetWeaver AS for Java User Admin application has an XSS vulnerability due to insufficient validation and encoding of URL parameters, with high impact on confidentiality and low impact on integrity and availability. CVSS v3 Base Score: 8,8 / 10 [CVE-2024-22126].
- XXE vulnerability in SAP NetWeaver AS Java (Guided Procedures) (3426111): SAP NetWeaver AS Java (CAF – Guided Procedures) has a vulnerability that allows an unauthenticated attacker to access sensitive files and data through a malicious XML request, but cannot modify them. CVSS v3 Base Score: 8,6 / 10 [CVE-2024-24743].
- Cross-Site Scripting (XSS) vulnerability in SAP CRM (WebClient UI) (3410875): The print preview option in SAP CRM WebClient has a Cross-Site Scripting vulnerability due to insufficient encryption of user input, which could be exploited by a low-privileged attacker to impact data confidentiality and integrity. CVSS v3 Base Score: 7,6 / 10 [CVE-2024-22130].
- Code Injection vulnerability in SAP IDES Systems (3421659): SAP IDES ECC systems have a vulnerability that allows the execution of arbitrary program code by the user, which could be exploited by an attacker. The solution involves removing the vulnerable code through changes to the transport and it is recommended not to install the IDES demo system on the same network as the productive environment and to always separate the demo environments from the productive ones, as well as to avoid installing real master data on the IDES system. CVSS v3 Base Score: 7,4 / 10 [CVE-2024-22132].
- Improper Certificate Validation in SAP Cloud Connector (3424610): Incorrect certificate validation in SAP Cloud Connector allows an attacker to spoof authentic servers, breaking mutual authentication and possibly intercepting requests to view or modify sensitive information. The fix is available as of SAP Cloud Connector 2.16.2, with no impact on system availability. 7,4 / 10 [CVE-2024-22642].
- Update – Information disclosure vulnerability in SAP GUI for WIndows and SAP GUI for Java (3385711): SAP GUI for Windows and SAP GUI for Java allow an unauthenticated attacker to access information which would otherwise be restricted and confidential. In addition, this vulnerability allows the unauthenticated attacker to create Layout configurations of the ABAP List Viewer and with this causing a mild impact on integrity and availability. 7,3 / 10 [CVE-2023-49580].
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (febrero):
SAP Patch Day: February 2024 – Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP Business Client, Versions – 6.5, 7.0, 7.70
- SAP ABA (Application Basis), Versions – 700, 701, 702, 731, 740, 750, 751, 752, 75C, 75I
- SAP NetWeaver AS Java (User Admin Application), Version – 7.50
- SAP NetWeaver AS Java (Guided Procedures), Version – 7.50
- AP CRM WebClient UI, Versions – S4FND 102, S4FND 103, S4FND 104, S4FND 105, S4FND 106, S4FND 107, S4FND 108, WEBCUIF 700, WEBCUIF 701, WEBCUIF 730, WEBCUIF 731, WEBCUIF 746, WEBCUIF 747, WEBCUIF 748, WEBCUIF 800, WEBCUIF 801
- IDES Systems, Versions – All version
- SAP Cloud Connector, Version – 2.0
- SAP GUI for Windows and SAP GUI for Java, Versions – SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758