Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Febrero 2022
Resumen y highlights del Mes
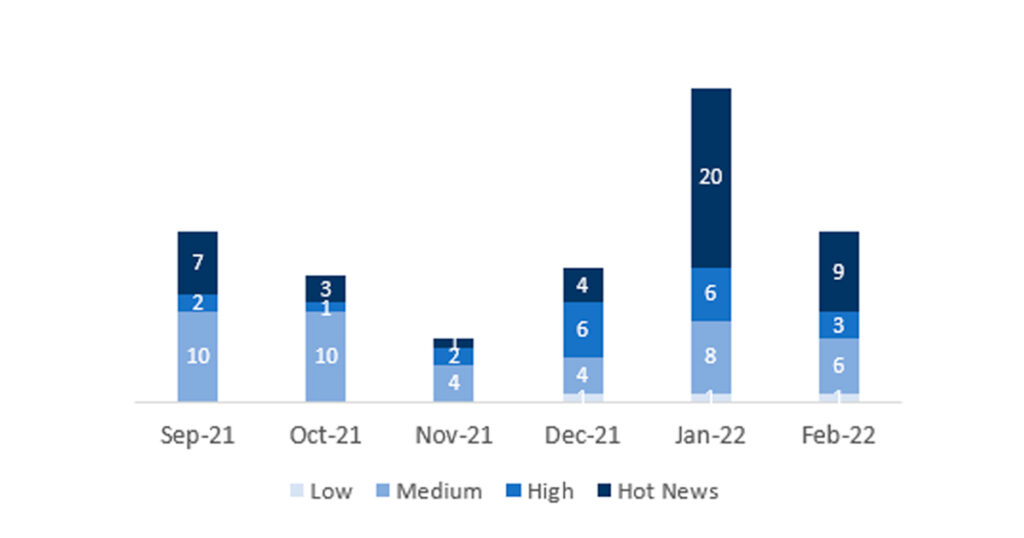
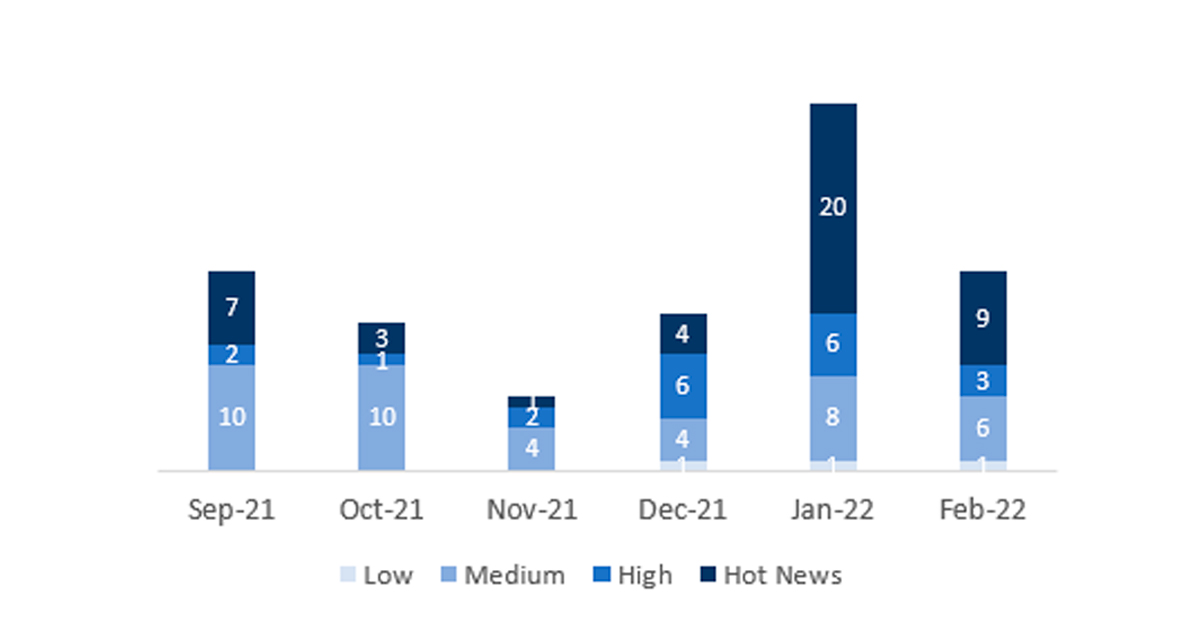
El número total de notas/parches ha disminuido con respecto al último mes. Además de esta reducción en el número de notas totales, el número de Hot News también se ve reducido, siendo 20 las que encontrábamos el mes pasado con respecto a las 9 existentes en Febrero. Por otro lado, cabe destacar, que se reduce el número de notas de criticidad alta pasando de 6 a 3 en este mes. Como siempre, dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 12 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 22 notas para todo el mes, 13 menos que el pasado Enero. (19 del patch Tuesday, 14 nuevas y 5 actualizaciones, siendo 16 menos que el pasado mes).
Tenemos 9 notas críticas (Hot News), 5 nuevas y 4 actualizaciones, en este mes, que destacan por su gran relevancia y por su alto CVVS. Además, revisaremos en detalle 3 del total de 3 notas altas (aquellas de CVSS mayor o igual a 7) donde este mes localizamos 2 nuevas y 1 actualización.
- Las notas más críticas del mes (con CVSS 10) serían un total de 8 con este CVSS que estarían afectando a SAP NetWeaver, SAP Content Server, SAP Web Dispatcher, SAP Commerce, SAP Data Intelligence 3, SAP Dynamic Authorization Management, Internet of Things Edge Platform, SAP Customer Checkout, Apache Log4j 2 component y la habitual nota de actualización de Google Chromium.
- Las siguientes en criticidad (CVSS 9.1 y CVSS 8.7 ) son una nota crítica (Hot News) y una nota alta. La primera estaría afectando a SAP Solution Manager y la segunda sería una vulnerabilidad que estaría afectando a la aplicación F0743 (Create Single Payment) de SAP S/4HANA.
- Finalmente, tenemos dos notas altas (CVSS 8.1 y CVSS 7.1), relacionadas con SAP NetWeaver Application Server Java y SAP NetWeaver AS ABAP (Workplace Server), respectivamente.
- El resto (10) son de nivel medio y bajo, y no las veremos en detalle.
- Este mes el tipo más predominante es el de “Remote Code Execution” (5/22 y 5/19 en patch day), seguido de Information Disclosure (4/22 y 2/19 en patch day).
En la gráfica podemos ver la clasificación de las notas de Febrero además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
- Request smuggling and request concatenation in SAP NetWeaver, SAP Content Server and SAP Web Dispatcher (3123396): This security note will be related to the vulnerability of SAP NetWeaver Application Server ABAP, SAP NetWeaver Application Server Java, ABAP Platform, SAP Content Server 7.53 and SAP Web Dispatcher for request smuggling and request concatenation. Due to that, an unauthenticated attacker can prepend a victim’s request with arbitrary data. This way, the attacker can execute functions impersonating the victim or poison intermediary Web caches. A successful attack could result in complete compromise of Confidentiality, Integrity and Availability of the system. The correction requires patching both SAP Web Dispatcher and SAP Kernel, where the patch solves the security issue completely. CVSS v3 Base Score: 10 / 10 (CVE-2022-22536).
- Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Commerce (3142773): This security note will be related to the vulnerability of SAP Commerce, as it uses a version of Open Source component Apache Log4j which has vulnerabilities. This vulnerability affects all installations of SAP Commerce, in particular SAP Commerce Cloud in Public Cloud, SAP Commerce Cloud in SAP Infrastructure, and SAP Commerce OnPrem. SAP Commerce addresses these vulnerabilities by upgrading the open-source log4j library that is shipped with SAP Commerce. The new library version, log4j 2.17.1 or later, does not have the listed vulnerabilities anymore. CVSS v3 Base Score: 10 / 10 (CVE-2021-44228).
- Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Data Intelligence 3 (on-premise) (3130920): This security note will be related to the vulnerability of SAP Data Intelligence 3 (on-premise), as it uses a version of Open Source component Apache Log4j which has vulnerabilities. The internal usage of a vulnerable log4j can be exploited to run arbitrary code as an unauthenticated user. There are two possible solutions, depending on the version of SAP Data Intelligence. For SAP Data Intelligence 3.1, the installation of patch 3.1.9 will remediate the risk and for SAP Data Intelligence 3.2, the installation of patch 3.2.2 will be the one to remediate the risk. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Dynamic Authorization Management (3139893): This security note will be related to the vulnerability of SAP Dynamic Authorization Management by Nextlabs, which uses a version of Open Source component Apache Log4j 2 which is vulnerable to remote code execution. The solution is different depending on the use of Windows or Linux. On the one hand, for windows, the solution will be to download and extract the utility package (log4j_vulnerability_fix_windows.zip), attached to the note. On the other hand, for Linux, download and extract the script files (log4j_vulnerability_fix_linux.zip), also attached to the note. CVSS v3 Base Score: 10 / 10 (CVE-2021-44228).
- Update – Remote Code Execution vulnerability associated with Apache Log4j 2 component used in Internet of Things Edge Platform (3132922): This security note will be related to the vulnerability of Internet of Things Edge Platform, which uses a version of Open Source component Apache Log4j 2 which is vulnerable to remote code execution. The solution is to upgrade the Edge Platform to the latest version (4.75.3), where Log4j is updated to v2.17.1. It is important to download the latest version from SAP Market Place. CVSS v3 Base Score: 10 / 10 (CVE-2021-44228).
- Update – Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Customer Checkout (3133772): This security note will be related to the vulnerability of SAP Customer Checkout, as it uses a version of Open Source component Apache Log4j which is vulnerable to remote code execution. SAP Customer Checkout – POS and manager – versions 2.0 FP11 PL06 (or lower) and 2.0 FP12 PL04 (or lower) and lower versions like FP09 and FP10 are using Apache Log4j which has Vulnerabilities. Therefore, the above mentioned security vulnerability applies for SAP Customer Checkout and SAP Customer Checkout manager. To prevent exploiting this vulnerability, update to one of the following versions mentioned below which uses a newer version of Apache Log4j (SAP Customer Checkout 2.0 FP11 PL08 or higher/ SAP Customer Checkout 2.0 FP12 PL06 or higher). Besides, customers on SAP Customer Checkout 2.0 FP09 and SAP Customer Checkout 2.0 FP10 can also update to SAP Customer Checkout 2.0 FP11 PL08 or higher, or SAP Customer Checkout 2.0 FP12 PL06 or higher. CVSS v3 Base Score: 10 / 10 (CVE-2021-44228).
- Central Security Note for Remote Code Execution vulnerability associated with Apache Log4j 2 component (3131047): This security note will be the central document to consolidate information on the Remote Code Execution vulnerability associated with Apache Log4j 2 component (CVE-2021-44228). Please refer to the solution section for the list of SAP Notes/KBAs with workaround and Security Notes released by SAP addressing this vulnerability. This security note will be a living document that will be updated regularly. CVSS v3 Base Score: 10 / 10 (CVE-2021-44228).
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Missing segregation of duties in SAP Solution Manager Diagnostics Root Cause Analysis Tools (3140940): Due to missing segregation of duty, SAP Solution Manager allows an attacker with admin privileges to browse files and execute code that can be executed on all connected Diagnostics Agents over the network. On successful exploitation, the attacker can completely compromise confidentiality, integrity and availability of the system. The solution to this vulnerability will be to apply the latest LM_SERVICE version containing the fix decribed in SAP Note 3145008, and also apply the SAP Note 3137764 to remove the links to the applications from the SAP Solution Manager Launchpad. CVSS v3 Base Score: 9.1 / 10 (CVE-2022-22544).
- Update – Multiple vulnerabilities in F0743 Create Single Payment application of SAP S/4HANA (3112928): It patches a Cross-Site Scripting and a Code Injection vulnerability in the Create Single Payment app of S/4HANA (app ID F0743). This app is used by accounts payable accountants through SAP Fiori (SAPUI5). It allows them to make a direct payment to a supplier when no invoice exists as well as pay open supplier line items. The two vulnerabilities existed because uploaded and downloaded files were not checked by the app. The first vulnerability allows an attacker with basic user rights to run arbitrary script code, resulting in sensitive information being disclosed or modified. The second one enables an attacker with basic user rights to inject dangerous content or malicious code which could result in critical information being modified or completely compromise the availability of the application. This SAP Security Note implements the Virus Scanner Interface (VSI) that checks a file during upload and download. This feature, however, relies on the antivirus software being installed, configured, and enabled on the server. The crucial part of the solution is proper configuration of the VSI via the definition of the default VSCANPROFILE (because the application uses the default VSCANPROFILE). To configure it, follow instructions described in the SAP Note “3052386 – FAQ | Virus Scan Interface (VSI)”. Configure the required components to enable the correct function of the VSI. CVSS v3 Base Score: 8.7 / 10 (CVE-2022-22531).
- HTTP Request Smuggling in SAP NetWeaver Application Server Java (3123427): SAP NetWeaver Application Server Java is vulnerable to HTTP request smuggling. Due to this vulnerability, an unauthenticated attacker could submit a crafted HTTP server request which triggers improper shared memory buffer handling, which could allow the malicious payload to be executed and hence execute functions that could be impersonating the victim or even steal the victim’s logon session. Besides, due to improper error handling, an attacker could submit multiple HTTP server requests resulting in errors, such that it consumes the memory buffer, which could result in system shutdown rendering the system unavailable. These vulnerabilities have been fixed by proper memory handling for HTTP pipeline requests. This correction is contained in all patch levels that are equal to or higher than the patch level listed in the “Support Package Patches” section of this SAP Note for the desired kernel release. CVSS v3 Base Score: 8.1 / 10 (CVE-2022-22532).
- SQL Injection vulnerability in SAP NetWeaver AS ABAP (Workplace Server) (3140587): SAP NetWeaver AS ABAP (Workplace Server) allows an attacker to execute crafted database queries, that could expose the backend database. Successful attack could result to disclosure of table of contents from the system, but no risk of modification possible. The problem is caused by an SQL injection vulnerability. The code composes a SQL statement that contains strings that can be altered by an attacker. The manipulated SQL statement can then be used to retrieve data from the database. The correction changes the SQL statement with dynamic WHERE clause into a SQL statement with static WHERE clause. This solution is contained in the Support Packages referenced by this note. In addition, correction instructions are available. CVSS v3 Base Score: 7.1 / 10 (CVE-2022-22540).
Enlaces de referencia
Enlaces de referencia del CERT del INCIBE en relación a la publicación de las notas para el mes de Febrero:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-febrero-2022
Otras referencias, en inglés de SAP y Onapsis (Febrero):
https://wiki.scn.sap.com/wiki/display/PSR/SAP+Security+Patch+Day+-+February+2022
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- Internet of Things Edge Platform, versión – 4.0;
- SAP 3D Visual Enterprise Viewer , versión – 9.0;
- SAP Adaptive Server Enterprise , versión – 16.0;
- SAP Business Client, versión – 6.5;
- SAP Business Objects Web Intelligence (BI Launchpad) , versión – 420;
- SAP Commerce: versiones – 1905, 2005, 2105 y 2011;
- SAP Content Server, versión – 7.53;
- SAP Customer Checkout, versión – 2;
- SAP Data Intelligence, versión – 3;
- SAP Dynamic Authorization Management, versión – 9.1.0.0, 2021.03;
- SAP ERP HCM (Portugal): versiones – 600, 604, y 608;
- SAP NetWeaver (ABAP y Java application Servers): versiones – 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755 y 756;
- SAP NetWeaver Application Server Java: versiones – KRNL64NUC 7.22, 7.22EXT, 7.49, KRNL64UC, 7.22, 7.22EXT, 7.49, 7.53, KERNEL 7.22, 7.49 y 7.53;
- SAP NetWeaver Application Server para ABAP (Kernel) y ABAP Platform (Kernel) : versiones – KERNEL 7.22, 8.04, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87, KRNL64UC 8.04, 7.22, 7.22EXT, 7.49, 7.53, KRNL64NUC 7.22, 7.22EXT y 7.49.
- SAP NetWeaver AS ABAP (Workplace Server): versiones – 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755, 756 y 787;
- SAP NetWeaver y ABAP Platform: versiones – KERNEL 7.22, 8.04, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87, KRNL64UC 8.04, 7.22, 7.22EXT, 7.49, 7.53, KRNL64NUC 7.22, 7.22EXT y 7.49;
- SAP S/4HANA (Supplier Factsheet y Enterprise Search para Business Partner, Supplier y Customer) : versiones – 104, 105 y 106;
- SAP S/4HANA: versiones – 100, 101, 102, 103, 104, 105 y 106;
- SAP Solution Manager (Diagnostics Root Cause Analysis Tools), versión – 720;
- SAP Web Dispatcher: versiones – 7.49, 7.53, 7.77, 7.81, 7.85, 7.22EXT, 7.86 y 7.87;