Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Agosto 2023
Resumen y highlights del Mes
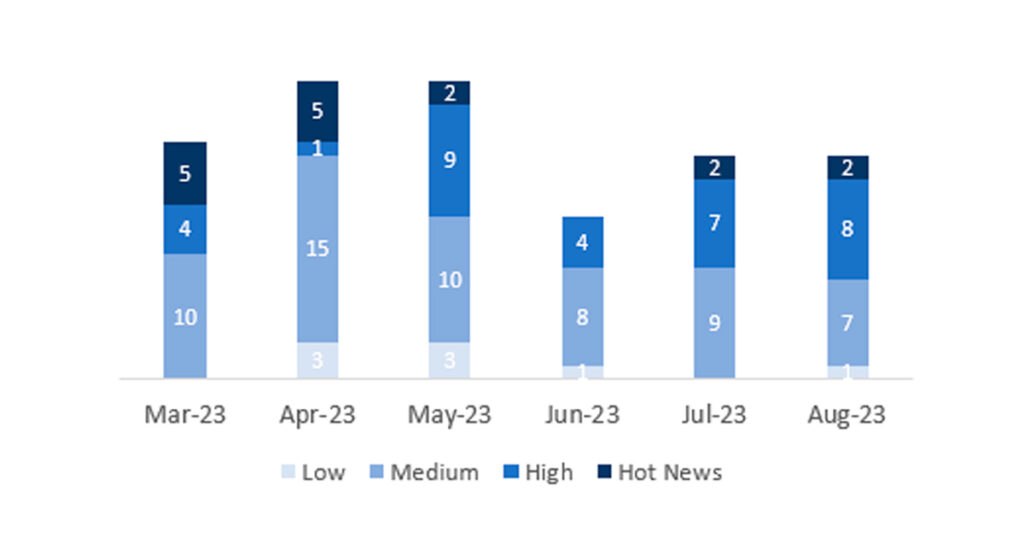
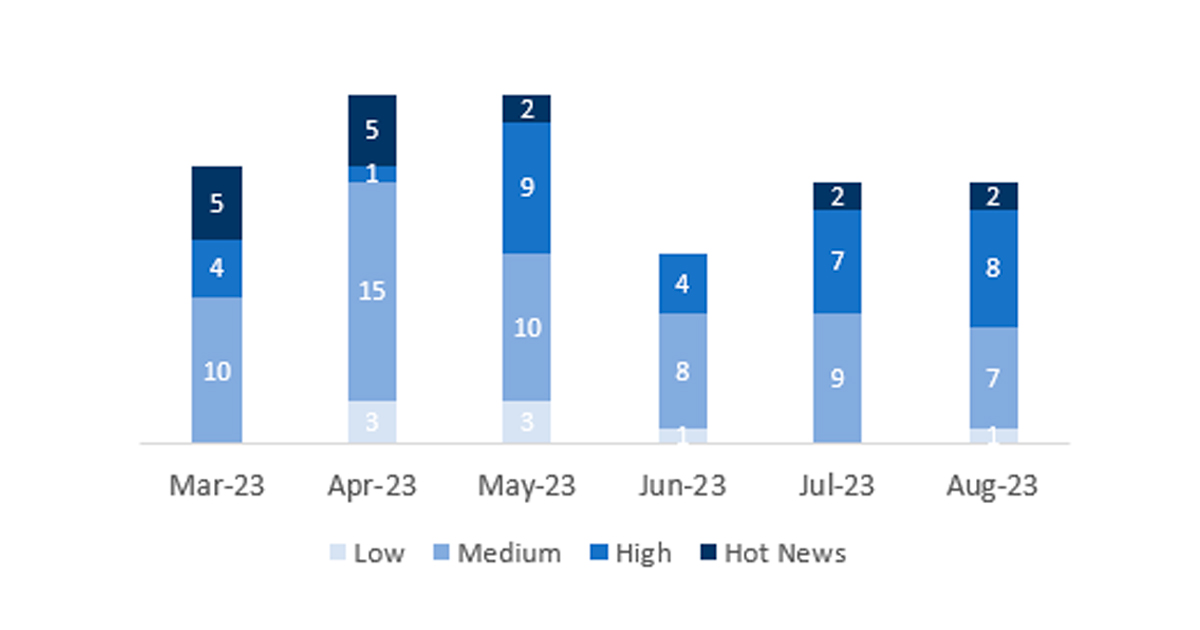
El número total de notas/parches ha sido de 18, las mismas que el mes pasado. El número de Hot News ha sido de 2, las mismas que el mes pasado. Por otro lado, cabe destacar que el número de notas de criticidad alta aumenta, pasando 7 a 8. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 10 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 18 notas para todo el mes (las 18 del patch Tuesday, 15 nuevas y 3 actualizaciones, son el mismo número de notas que el pasado patch Tuesday).
Revisaremos en detalle 10 del total de 10 notas altas y HotNews, 1 de las 2 HotNews es nueva y 7 de 8 notas altas serían nuevas (aquellas de CVSS mayor o igual a 7).
- La nota más crítica del mes (con CVSS 9,8), es una HotNew relacionada con “Multiple Vulnerabilities in SAP PowerDesigner”.
- La siguiente nota en criticidad (con CVSS 9,1), es una HotNew, se trata de una actualización de una nota publicada el pasado mes de julio, relacionada con “OS command injection vulnerability in SAP ECC and SAP S/4HANA”
- La siguiente nota en criticidad (con CVSS 8,8), está relacionada con “Improper authentication in SAP Commerce Cloud”
- La siguiente nota en criticidad (con CVSS 8,7), se trata de una actualización de una nota publicada el pasado mes de julio, relacionada con “Directory Traversal vulnerability in SAP NetWeaver (BI CONT ADD ON)”
- La siguiente nota en criticidad (con CVSS 7,8), se trata de una nota alta relacionada con “Code Injection vulnerability in SAP PowerDesigner”
- Las siguientes notas en criticidad (con CVSS 7,6), se trata de dos notas altas, una relacionada con “Cross-Site Scripting (XSS) vulnerability in SAP Business One” y la otra con “Binary hijack in SAP BusinessObjects Business Intelligence Suite (installer)”
- Las siguientes notas en criticidad (con CVSS 7,5), se trata de dos notas altas, una relacionada con “Denial of Service (DoS) vulnerability due to the usage of vulnerable version of Commons FileUpload in SAP BusinessObjects Business Intelligence Platform (CMC)” y la otra con “Improper Authorization check vulnerability in SAP Message Server”
- La siguiente nota en criticidad (con CVSS 7,1), se trata de una nota alta relacionada con “SQL Injection vulnerability in SAP Business One (B1i Layer)”
- Este mes el tipo más predominante es “Information Disclosure vulnerability” (4/18 en patch day).
En la gráfica (post agosto 2023 de SAP) podemos ver la clasificación de las notas de agosto además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas SAP más relevantes es el siguiente (en inglés):
- Multiple Vulnerabilities in SAP PowerDesigner (3341460): SAP PowerDesigner queries all password hashes in the backend database and compares it with the user provided one during login attempt, which might allow an attacker to access password hashes from the client’s memory. solution is to upgrade both the client and the proxy. CVSS v3 Base Score: 9,8 / 10 [CVE-2023-37483].
- Update – OS command injection vulnerability in SAP ECC and SAP S/4HANA (IS-OIL) (3350297): Due to programming error in function module and report, IS-OIL component in SAP ECC and SAP S/4HANA allows an authenticated attacker to inject an arbitrary operating system command into an unprotected parameter in a common (default) extension. On successful exploitation, the attacker can read or modify the system data as well as shut down the system This note has been re-released with updated ‘Symptom and Reason and Prerequisites’ information. CVSS v3 Base Score: 9,1 / 10 [CVE-2023-36922].
- Improper authentication in SAP Commerce Cloud (3346500): Certain configurations of SAP Commerce Cloud may accept an empty passphrase for user ID and passphrase authentication, allowing users to log into the system without a passphrase. This vulnerability only affects active user accounts that have an empty passphrase. Other user accounts that have a valid passphrase set are not affected. Note contains a workaround. CVSS v3 Base Score: : 8,8 / 10 [CVE-2023-39439].
- Update – Directory Traversal vulnerability in SAP NetWeaver (BI CONT ADD ON) (3331376): An attacker with non-administrative authorizations can exploit a directory traversal flaw to over-write system files. Data from confidential files cannot be read but potentially some OS files can be over-written leading to system compromise. This note has been re-released with updated ‘Correction instruction’ information. CVSS v3 Base Score: 8,7 / 10 [CVE-2023-33989].
- Code Injection vulnerability in SAP PowerDesignerProduct (3341599): SAP SQLA for PowerDesigner 17 bundled with SAP PowerDesigner 16.7 SP06 PL03, allows an attacker with local access to the system, to place a malicious library, that can be executed by the application. An attacker could thereby control the behavior of the application. There are two reasons for this vulnerability, SAP PowerDesigner Client connecting to bundled “SQL Anywhere for PowerDesigner” through ODBC could lead to command injection and SAP PowerDesigner Proxy connecting to bundled “SQL Anywhere for PowerDesigner” through ODBC could lead to command injection with priviledge escalation. Note contains a workaround. CVSS v3 Base Score: 7,8 / 10 [CVE-2023-36923].
- Cross-Site Scripting (XSS) vulnerability in SAP Business One (3358300): Cross-site scripting (XSS) in SAP business One allows an attacker to insert malicious code into the content of a web page or application and gets it delivered to the client. This could lead to harmful action affecting the Confidentiality, Integrity and Availability of the application. CVSS v3 Base Score: 7,6 / 10 [CVE-2023-39437].
- Binary hijack in SAP BusinessObjects Business Intelligence Suite (installer)(3317710): SAP Business Objects Installers allows an authenticated attacker within the network to overwrite an executable file created in a temporary directory during the installation process. On replacing this executable with a malicious file, an attacker can completely compromise the confidentiality, integrity, and availability of the system. CVSS v3 Base Score: 7,6 / 10 [CVE-2023-37490].
- Denial of Service (DoS) vulnerability due to the usage of vulnerable version of Commons FileUpload in SAP BusinessObjects Business Intelligence Platform (CMC)(3312047): SAP BusinessObjects Business Intelligence Platform (CMC) is using a vulnerable version of commons-fileupload which is vulnerable to Denial of Service due to CVE-2023-24998. . CVSS v3 Base Score: 7,5 / 10
- Improper Authorization check vulnerability in SAP Message Server (3344295): The ACL (Access Control List) of SAP Message Server can be bypassed in certain conditions, which may enable an authenticated malicious user to enter the network of the SAP systems served by the attacked SAP Message server. This may lead to unauthorized read and write of data as well as rendering the system unavailable. Affected versions of SAP Message Server are 7.22 to 7.77 and certain preconditions have to be met to exploit,
SAP Message Server is only protected by an ACL; the profile parameter system/secure_communication is set to OFF; the internal port of the SAP Message Server is not protected; the trace level of the SAP Message Server is of value 2 or higher and The ACL file contains an IP address. Note contains a workaround. CVSS v3 Base Score: 7,5 / 10 [CVE-2023-37491].
- SQL Injection vulnerability in SAP Business One (B1i Layer) (3337797): B1i module of SAP Business One application allows an authenticated user with deep knowledge to send crafted queries over the network to read or modify the SQL data. On successful exploitation, the attacker can cause low impact on confidentiality, high impact on the integrity and availability of the application. CVSS v3 Base Score: 7,1 / 10 [CVE-2023-33993]
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (agosto):
SAP Security Patch Day for August 2023 | Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP Business One (B1i Layer), Version –10.0
- SAP Business One, Version –10.0
- SAP BusinessObjects Business Intelligence (installer), Versions –420, 430
- SAP BusinessObjects Business Intelligence Platform, Versions–420
- SAP Commerce, Versions –HY_COM 2105, HY_COM 2205, COM_CLOUD 2211
- SAP ECC and SAP S/4HANA (IS-OIL), Versions -600, 602, 603, 604, 605, 606, 617, 618, 800, 802, 803, 804, 805, 806, 807
- SAP Message Server, Versions–KERNEL 7.22, KERNEL 7.53, KERNEL 7.54, KERNEL 7.77, RNL64UC 7.22, RNL64UC 7.22EXT, RNL64UC 7.53, KRNL64NUC 7.22, KRNL64NUC 7.22EX
- SAP NetWeaver (BI CONT ADD ON), Versions –707, 737, 747, 757
- SAP PowerDesigner, Version –16.7