Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas abril 2025
Resumen y highlights del Mes
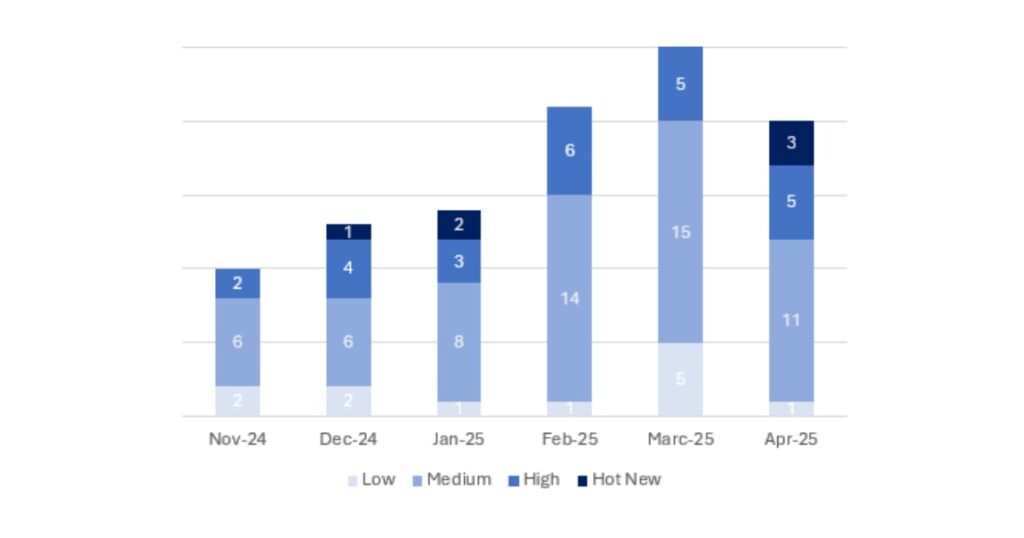
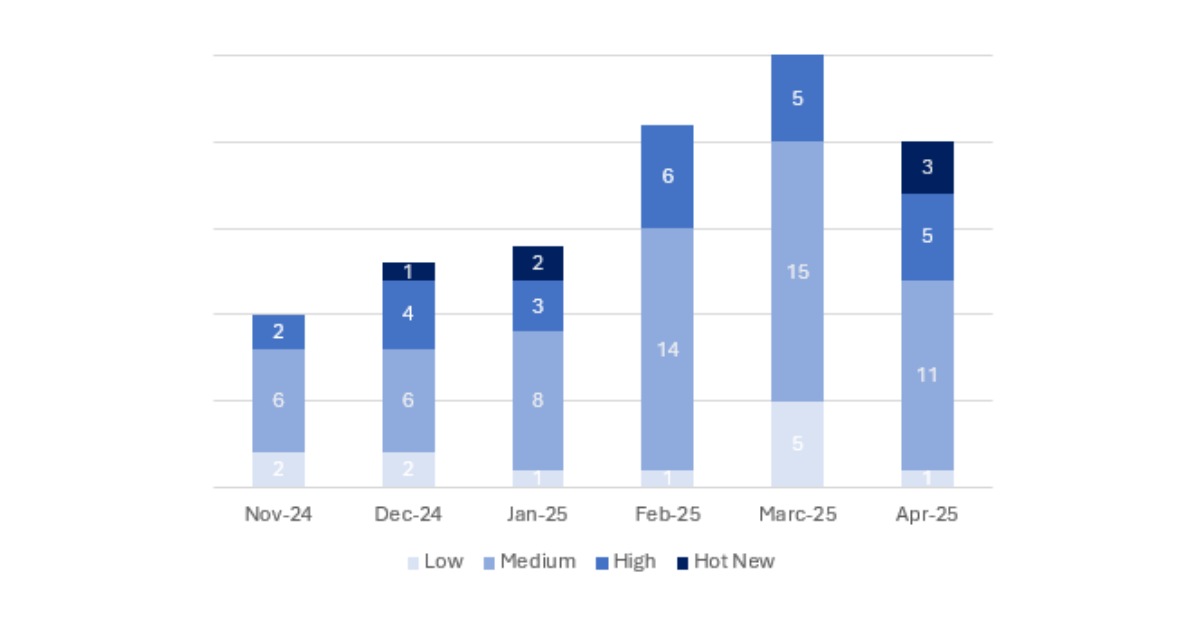
Este mes el número total ha sido de 20, 5 menos que en el periodo anterior. Este mes se han publicado 3 Hot News, 3 más que en el periodo anterior. En cuanto a notas de criticidad alta, se han publicado 5 notas, el mismo número que en el periodo anterior. Las notas medias y bajas no serán revisadas, por lo que daremos detalle de un total de 8 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 20 notas para todo el mes (18 nuevas y 2 actualizaciones de notas publicadas en meses anteriores).
Revisaremos en detalle un total de 8 notas, todas de criticidad alta y Hot News:
-
Las notas más críticas del mes (CVSS 9,9) son 2 Hot News, ambas relacionadas con “Code Injection Vulnerability “, una para SAP S/4 HANA “Code Injection Vulnerability in SAP S/4HANA (Private Cloud)” y la otra para SLT “Code Injection Vulnerability in SAP Landscape Transformation (Analysis Platform)”
-
La siguiente en criticidad (CVSS 9,8) se trata de una Hot New relacionada con “Authentication Bypass Vulnerability in SAP Financial Consolidation”
-
La siguiente en criticidad (CVSS 8,8) se trata de una actualización de una nota publicada en febrero de este año, relacionada con “Improper Authorization in SAP BusinessObjects Business Intelligence platform”
- La siguientes en criticidad (CVSS 8,5) se trata de una nota relacionada con “Mixed Dynamic RFC Destination vulnerability through Remote Function Call (RFC) in SAP NetWeaver Application Server ABAP”
- La siguiente en criticidad (CVSS 8,1) se trata de una nota relacionada con “Time-of-check Time-of-use (TOCTOU) Race Condition vulnerability in Apache Tomcat within SAP Commerce Cloud”
-
Por último tenemos 2 notas altas (CVSS 7,7), una nota relacionada con “Directory Traversal vulnerability in SAP Capital Yield Tax Management” y otra con “Directory Traversal vulnerability in SAP NetWeaver and ABAP Platform (Service Data Collection)”
-
Este mes el tipo más predominante es “Code Injection Vulnerability “ (3/20 en el patch day)
En la gráfica podemos ver la clasificación de las notas de abril, además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
-
Code Injection Vulnerability in SAP S/4HANA (Private Cloud) (3581961): SAP S/4HANA has a vulnerability that allows a privileged attacker to inject arbitrary ABAP code through a function module exposed via RFC. This bypasses authorization checks and acts as a backdoor, compromising the system’s confidentiality, integrity, and availability, potentially leading to a full system takeover. CVSS v3 Base Score 9,9/ 10 [CVE-2025-27429]
-
Code Injection Vulnerability in SAP Landscape Transformation (Analysis Platform) (3587115): SAP Landscape Transformation (SLT) has a vulnerability that allows an attacker with user privileges to inject arbitrary ABAP code through a function module exposed via RFC. This bypasses authorization checks and acts as a backdoor, compromising the system’s confidentiality, integrity, and availability, potentially leading to a full system takeover. CVSS v3 Base Score 9,9/ 10 [CVE-2025-31330]
-
Authentication Bypass Vulnerability in SAP Financial Consolidation (3572688) SAP Financial Consolidation has a vulnerability that allows an unauthenticated attacker to gain unauthorized access to the Admin account. This issue stems from improper authentication mechanisms, which significantly impact the Confidentiality, Integrity, and Availability of the application. CVSS v3 Base Score 9,8/ 10 [CVE-2025-30016]
-
Update – Improper Authorization in SAP BusinessObjects Business Intelligence platform (3525794): Under specific conditions, SAP BusinessObjects Business Intelligence platform allows an attacker with user rights to generate or retrieve a secret passphrase, enabling them to impersonate any user in the system by accessing the target system locally. This vulnerability has a high impact on the confidentiality, integrity, and availability of the application. Additionally, it requires manual activities. CVSS v3 Base Score 8,8/ 10 [CVE-2025-0064]
-
Mixed Dynamic RFC Destination vulnerability through Remote Function Call (RFC) in SAP NetWeaver Application Server ABAP (3554667): Under certain conditions, SAP NetWeaver Application Server ABAP allows an authenticated attacker to craft a Remote Function Call (RFC) request to restricted destinations, potentially exposing credentials for a remote service. These credentials can then be exploited to completely compromise the remote service, which can significantly impact the confidentiality, integrity, and availability of the application. The note also includes a workaround.CVSS v3 Base Score 8,5/ 10 [CVE-2025-23186]
-
Time-of-check Time-of-use (TOCTOU) Race Condition vulnerability in Apache Tomcat within SAP Commerce Cloud (3590984): If successfully exploited, the vulnerability could fully compromise the system’s confidentiality, integrity, and availability. However, the success of this exploitation depends on a server setting that remains beyond the attacker’s control, and SAP Commerce is not exploitable out of the box. To resolve this, it is recommended to apply the recommended patches, as no workaround is available.( CVE-2024-56337 ).CVSS v3 Base Score 8,1/ 10 [CVE-2024-56337]
-
Directory Traversal vulnerability in SAP Capital Yield Tax Management (2927164): SAP Capital Yield Tax Management has a directory traversal vulnerability due to insufficient path validation. This allows an attacker with low privileges to read files from directories they don’t have access to, resulting in a high impact on confidentiality. Integrity and availability are not affected. CVSS v3 Base Score 7,7/ 10 [CVE-2025-30014]
-
Directory Traversal vulnerability in SAP NetWeaver and ABAP Platform (Service Data Collection) (3581811):Due to a directory traversal vulnerability, an authorized attacker could gain access to critical information by using an RFC-enabled function module. If successfully exploited, the attacker could read files from any managed system connected to SAP Solution Manager, resulting in a high impact on confidentiality. There is no impact on integrity or availability. CVSS v3 Base Score 7,7/ 10 [CVE-2025-27428]
Enlaces de referencia
Referencias, en inglés de SAP y Onapsis (abril):
SAP Security Patch Day – April 2025
SAP Patch Day: April 2025 – Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente
- SAP S/4HANA (Private Cloud), Versions – S4CORE 102, 103, 104, 105, 106, 107, 108
- SAP Landscape Transformation (Analysis Platform), Versions – DMIS 2011_1_700, 2011_1_710, 2011_1_730, 2011_1_731
- SAP BusinessObjects Business Intelligence platform (Central Management Console), Versions – ENTERPRISE 430, 2025
- SAP NetWeaver Application Server ABAP, Versions – KRNL64NUC 7.22, 7.22EXT, KRNL64UC 7.22, 7.22EXT, 7.53, KERNEL 7.22, 7.53, 7.54, 7.77, 7.89, 7.93
- SAP Commerce Cloud, Versions – HY_COM 2205, COM_CLOUD 2211
- SAP Capital Yield Tax Management, Versions – CYTERP 420_700, CYT 800, IBS 7.0, CYT4HANA 100
- SAP NetWeaver and ABAP Platform (Service Data Collection), Versions – ST-PI 2008_1_700, 2008_1_710, 740
- SAP Commerce Cloud (Public Cloud), Version – COM_CLOUD 2211
- SAP ERP BW Business Content, Versions – BI_CONT 707, 737, 747, 757
- SAP BusinessObjects Business Intelligence Platform, Version – ENTERPRISE 430
- SAP KMC WPC, Version – KMC-WPC 7.50
- SAP NetWeaver Application Server ABAP (applications based on SAP GUI for HTML), Versions – KRNL64NUC 7.22, 7.22EXT, KRNL64UC 7.22, 7.22EXT, 7.53, KERNEL 7.22, 7.53, 7.54, 7.77, 7.89, 7.93, 9.14
- SAP Solution Manager, Versions – ST 720, SAP_BASIS 700, SAP_BASIS 701, SAP_BASIS 702, SAP_BASIS 731, SAP_BASIS 740, SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758, SAP_BASIS 914
- SAP S4CORE entity, Versions – S4CORE 107, 108
- SAP NetWeaver Application Server ABAP (Virus Scan Interface), Versions – SAP_BASIS 700, SAP_BASIS 701, SAP_BASIS 702, SAP_BASIS 731, SAP_BASIS 740, SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758
- SAP NetWeaver, Versions – SAP_ABA 700, 701, 702, 731, 740, 750, 751, 752, 75C, 75D, 75E, 75F, 75G, 75H, 75I
- SAP NetWeaver and ABAP Platform (Application Server ABAP), Versions – KRNL64UC 7.53, KERNEL 7.53, 7.54
- SAP CRM and SAP S/4HANA (Interaction Center), Versions – S4CRM 100, 200, 204, 205, 206, S4FND 102, 103, 104, 105, 106, 107, 108, S4CEXT 107, 108, BBPCRM 701, 702, 712, 713, 714, WEBCUIF 701, 731, 746, 747, 748, 800, 801