Inprosec a través de sus servicios, como el SAP Security Assessment, ayuda a sus clientes a mejorar los niveles de seguridad de sus sistemas SAP.
Notas Abril 2021
Resumen y highlights del Mes
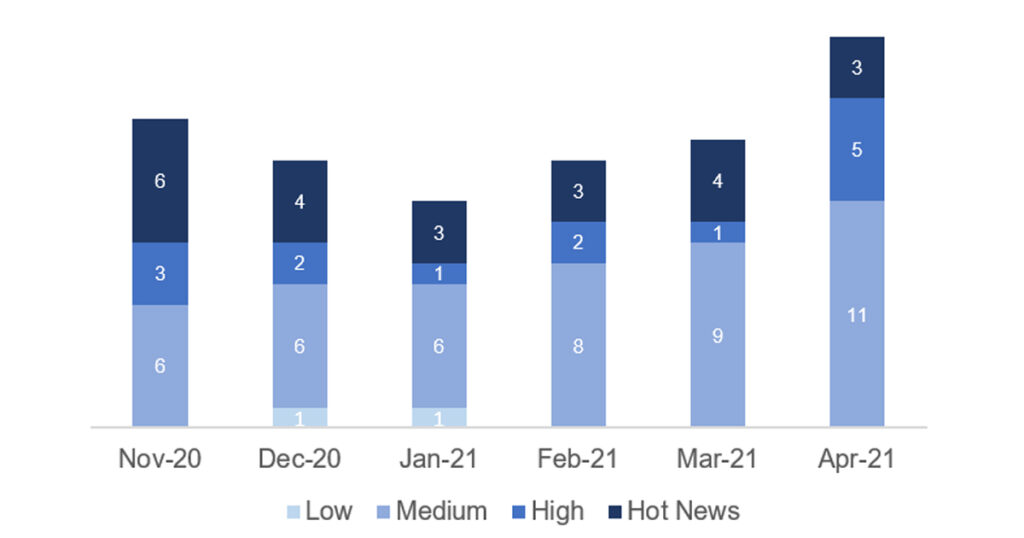
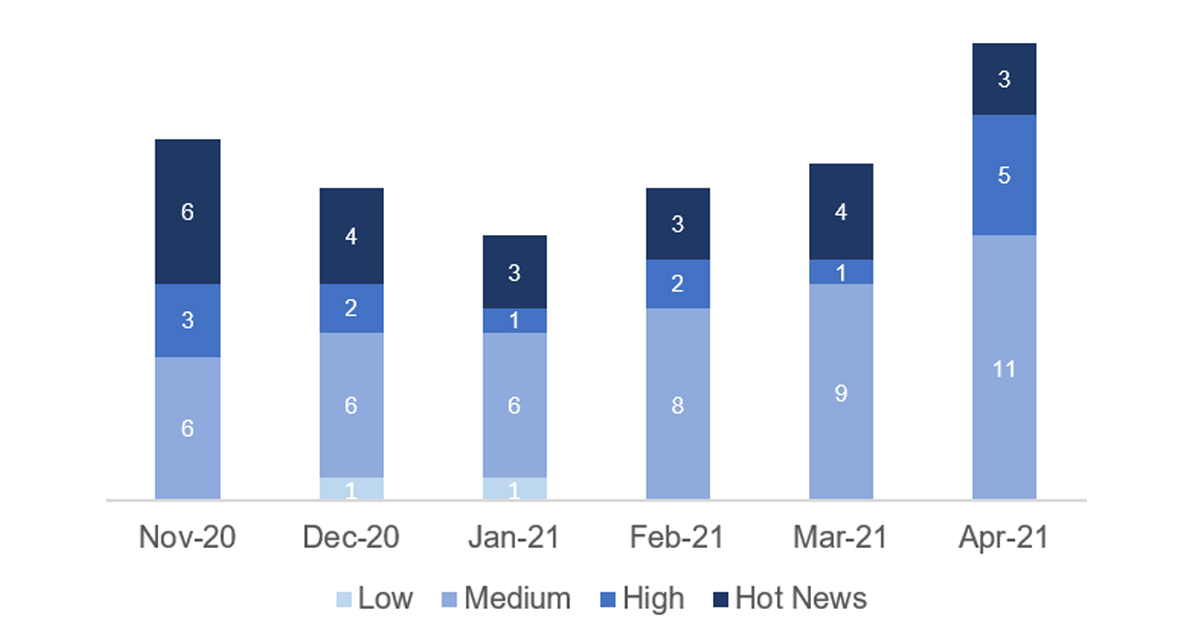
El número total de notas/parches ha aumentado con respecto al último mes. A pesar de esta subida en el número de notas totales, el número de Hot News disminuye, siendo 4 las que encontrábamos el mes pasado con respecto a las 3 existentes en Abril. Por otro lado, cabe destacar el aumento en el número de notas de criticidad alta pasando de 1 a 5 en este mes. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 8 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 23 notas para todo el mes, 5 más que el pasado Marzo (19 del patch Tuesday, 14 nuevas y 5 actualizaciones, siendo 6 notas más que el pasado mes).
Tenemos una nota crítica (Hot News) nueva, siendo el total de 3 en este mes que destacan por su alto CVVS, una de ellas la actualización recurrente para el SAP Business Client con Chromium . Además revisaremos en detalle las notas altas de este mes (con un CVSS mayor que 7), que son un total de 5.
- La nota más crítica del mes (con CVSS 10) es una actualización. Esta nota sería la habitual de “Browser Control Google Chromium Delivered with SAP Business Client”.
- Las siguientes en criticidad (con CVSS 9.9 y 9.6) es una de Code Injection Vulnerability que afecta a SAP Commerce y la otra una de Missing Authorization Check que afecta a SAP NetWeaver AS JAVA (MigrationService).
- A partir de ahí, localizamos un total de 5 notas de criticidad alta (high priority), destacando una con un CVSS de 8.3, siendo una nota nueva de posible obtención de contraseñas a través del método de fuerza bruta en las cuentas administrativas de SAP NetWeaver Master Data Management.
- Este mes los tipos más predominantes son “Information Disclosure” (6/23 y 5/19 en patch day) y “Missing Authorization Check” (4/23 y 4/19 en patch day).
En la gráfica (post Abril 2021 de SAP) podemos ver la clasificación de las notas de Abril además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas más relevantes es el siguiente (en inglés):
-
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. CVSS v3 Base Score: 10 / 10.
- Remote Code Execution vulnerability in Source Rules of SAP Commerce (3040210): SAP Commerce Backoffice application allows certain authorized users to create source rules which are translated to drools rule when published to certain modules within the application. An attacker with this authorization can inject malicious code in the source rules and perform remote code execution enabling them to compromise the confidentiality, integrity and availability of the application. SAP Commerce Cloud addresses this vulnerability by adding validation and output encoding when processing Promotion Rules and other Source Rules. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-27602).
- Update – Missing Authorization Check in SAP NetWeaver AS JAVA (Migration Service) (3022422): The MigrationService, which is part of SAP NetWeaver, does not perform an authorization check. This might allow an unauthorized attacker to access configuration objects, including such that grant administrative privileges. This could result in complete compromise of system confidentiality, integrity, and availability. Аs a final solution, you have to patch your systems with a new version of the J2EE-APPS.SCA, which is proided in the attached correction measures. The correction adds the missing authorization check. Keep in mind that this solution is an offline deployment that requires a restart of your systems. CVSS v3 Base Score: 9.6 / 10 (CVE-2021-21481).
- Information Disclosure in SAP NetWeaver Master Data Management (3017908): When security guidelines and recommendations concerning administrative accounts of a SAP NetWeaver Master Data Management installation have not been thoroughly reviewed, a malicious user with access to the MDM Server subnet might try to find the password using a bruteforce method. If successsful, the attacker could obtain access to highly sensitive data and MDM administrative privileges. The solution is to apply the latest patch, effectively replacing the main server executable and restarting it. In addition, the use of strong password should be enforced, especially for administrative accounts. It is highly recommended to create an additional administrative user in addition to the default ‘Admin’ account, in order to alleviate the possible locking of this default account. CVSS v3 Base Score: 8.3 / 10 (CVE-2021-21482).
- Information Disclosure in SAP Solution Manager (3017823): Under certain conditions SAP Solution Manager allows a high privileged attacker to get access to sensitive information which has a direct serious impact beyond the exploitable component. Some impacts of Information Disclosure could be the loss of information and system configuration confidentiality or information gathering for further exploits and attacks. The solution would be to implement the attached correction instructions in the note or install the corresponding Support Package. After you do so, the information will no longer be disclosed. CVSS v3 Base Score: 8.2 / 10 (CVE-2021-21483).
- Update – Missing Authorization check in SAP NetWeaver AS ABAP and SAP S4 HANA (SAP Landscape Transformation) (2993132): SAP Landscape Transformation allows a high privileged user to execute a RFC function module to which access should be restricted. This weakness gives attacker ability to read some sensitive internal information and also make vulnerable SAP systems completely unavailable. To solve the problem, the affected RFC function module have now been enforced to properly check access restrictions and it is necessary to implement the attached correction instructions in this security note. CVSS v3 Base Score: 7.6 / 10 (CVE-2020-26832).
- Unquoted Search Path in SAPSetup (3039649): An unquoted service path in SAPSetup could lead to privilege escalation during the installation process that is performed when an executable file is registered. This could further lead to complete compromise of confidentiality, Integrity and Availability. To fix this issue, a new process has now been created with a quoted path to the executable. In order to apply the fix, update NwSapSetup to a version 9.0.107.0 or higher from Software downloads available in the SAP Support Portal. There is no impact on functionality after the fix. CVSS v3 Base Score: 7.5 / 10 (CVE-2021-27608).
- Information Disclosure in SAP NetWeaver AS for Java (Telnet Commands) (3001824): An Unauthorized attacker may be able to entice an administrator to invoke telnet commands of an SAP NetWeaver Application Server for Java that allow the attacker to gain NTLM hashes of a privileged user. The vulnerability is a result of SMB relay attack. This correction prevents usage of SMB protocol. To fix the issue apply the corrective measure according to the “Validity” and “Support Packages & Patches” sections of the note. CVSS v3 Base Score: 7.4 / 10 (CVE-2021-21485).
Enlaces de referencia
Enlaces de referencia del CERT del INCIBE en relación a la publicación de las notas para el mes de Abril:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-abril-2021
Otras referencias, en inglés de SAP y Onapsis (Abril):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=573801649
Recursos afectados
- SAP Business Client, versión 6.5;
- SAP Commerce, versiones 1808, 1811, 1905, 2005 y 2011;
- SAP Fiori Apps 2.0 for Travel Management in SAP ERP, versión 608;
- SAP Focused RUN, versiones 200 y 300;
- SAP Manufacturing Execution, versiones 15.1, 15.2, 15.3 y 15.4;
- SAP NetWeaver:
- Master Data Management, versiones 710 y 710.750;
- AS for ABAP, versiones 2011_1_620, 2011_1_640, 2011_1_700, 2011_1_710, 2011_1_730, 2011_1_731 y 2011_1_752, 2020, 731, 740, 750 y 7.30;
- SAP NetWeaver Application Server Java (Applications based on Web Dynpro Java), versiones 7.00, 7.10, 7.11, 7.20, 7.30, 731, 7.40 y 7.50;
- SAP Netweaver AS JAVA (Applications based on HTMLB for Java), versiones:
- EP-BASIS, versiones 7.10, 7.11, 7.30, 7.31, 7.40 y 7.50;
- FRAMEWORK, versiones 7.10 y 7.11;
- FRAMEWORK-EXT , versiones 7.30, 7.31, 7.40 y 7.50;
- SAP Netweaver AS JAVA (Customer Usage Provisioning Servlet), versiones 7.31, 7.40 y 7.50;
- SAP NetWeaver AS JAVA (HTTP Service), versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP NetWeaver AS JAVA (MigrationService), versiones 7.10, 7.11, 7.30, 7.31, 7.40 y 7.50;
- SAP NetWeaver AS JAVA (Telnet Commands), versiones:
- ENGINEAPI, versiones 7.30, 7.31, 7.40 y 7.50;
- ESP_FRAMEWORK, versiones 7.10, 7.20, 7.30, 7.31, 7.40 y 7.50;
- J2EE-FRMW, versiones 7.10, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SERVERCORE, versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP Process Integration, versiones 7.10, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP S4 HANA (SAP Landscape Transformation) , versiones 101, 102, 103, 104 y 105;
- SAP Setup, versión 9.0;
- SAP Solution Manager versión 7.2;