During this article, we will analyse the authorisation related to line and organisational criteria for tables.
Tables in SAP, depending on the information they store, can be a critical resource for the system (IT tables, configuration, etc.) or for the business (approver tables, accounting periods, etc.). As such, it has always been sought to restrict access to only those users who must have it. It is quite common to consider standard table modification or display transactions (e.g. SM30 or SE16) as Critical Actions and to monitor their assignment through risk analysis tools such as the Access Risk Analysis (ARA) module of SAP® GRC.
As for all other transactions, it is possible to restrict and control access to the different SAP® tables using the standard authorisation model. Authorisation objects are the basic unit for controlling user permissions in an SAP® system, and in this case, we have 3 objects for this purpose:
- S_TABU_DIS: allows you to control access to display or modify tables, using the authorisation group to which the table belongs.
- S_TABU_NAM: allows you to control access to display or modify tables, directly using the individual table you want to restrict.
- S_TABU_LIN: allows you to control the authorisation to display or modify the contents of tables, based on a previously defined organisational criterion. This object must be used in conjunction with one of the previous two.
To grant access to a table, it is sufficient to use one of the first two objects (S_TABU_DIS or S_TABU_NAM). However, these objects will allow the entire table to be displayed or modified, without being able to restrict according to content. Here we can use the S_TABU_LIN object, which is part of an extension of the authorisations concept called Line-Related Authorisations. In the following, we will detail this extension of the authorisations, to facilitate its implementation when needed.
Line Referenced Authorisations
This is an authorisations concept that extends and complements the traditional one. It allows to restrict access to tables according to previously defined organisational criteria. In this way it is possible to grant a user an access authorisation only to specific rows of a table.
Using the traditional authorisations, objects S_TABU_NAM and S_TABU_DIS, it is possible to allow the display or maintenance of contents in the whole table. The S_TABU_LIN object, on the other hand, adds the possibility to filter at line level. For example, if you decide to use country as an organisational criterion in a table, you can restrict user access so that users can only view and modify records corresponding to their country in a table with information for all countries. The use of this object and authorisation concept is optional and must always be done in conjunction with the objects S_TABU_DIS/S_TABU_NAM.
Define and Activate Organisational Criteria
To apply the concept of line-related authorisations, an organisational criterion must be defined and activated in advance. These criteria define which tables and fields are to be considered for applying a certain restriction and will be necessary when creating the authorisations as well. All of them must always be key fields of the table to be restricted.
To define an organisational criterion, it can be done from the Implementation Guide (SPRO) in the following path: SAP® NetWeaver → Application Server → System Management → Users and Authorisations → Line-Related Authorisations → Define Organisational Criteria.
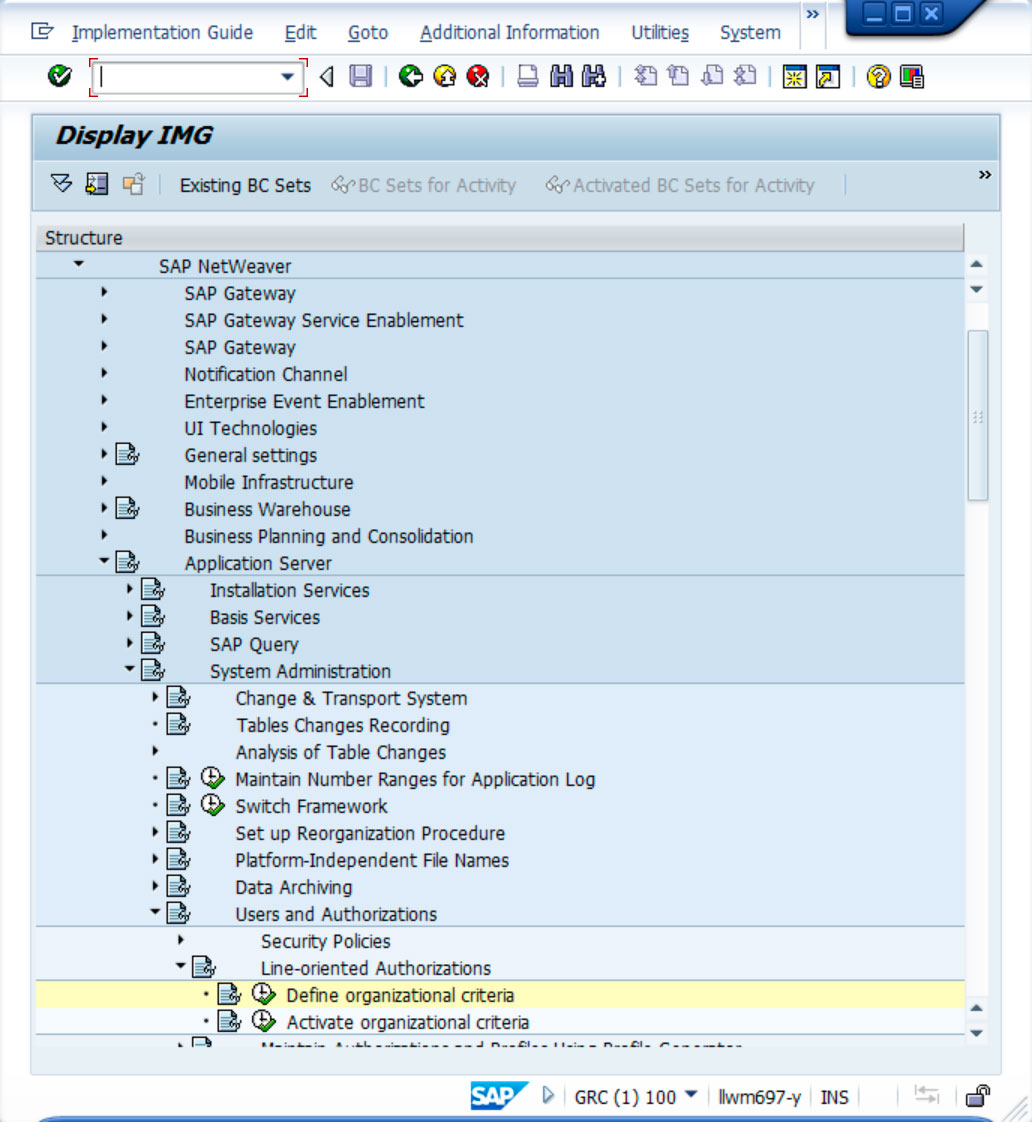
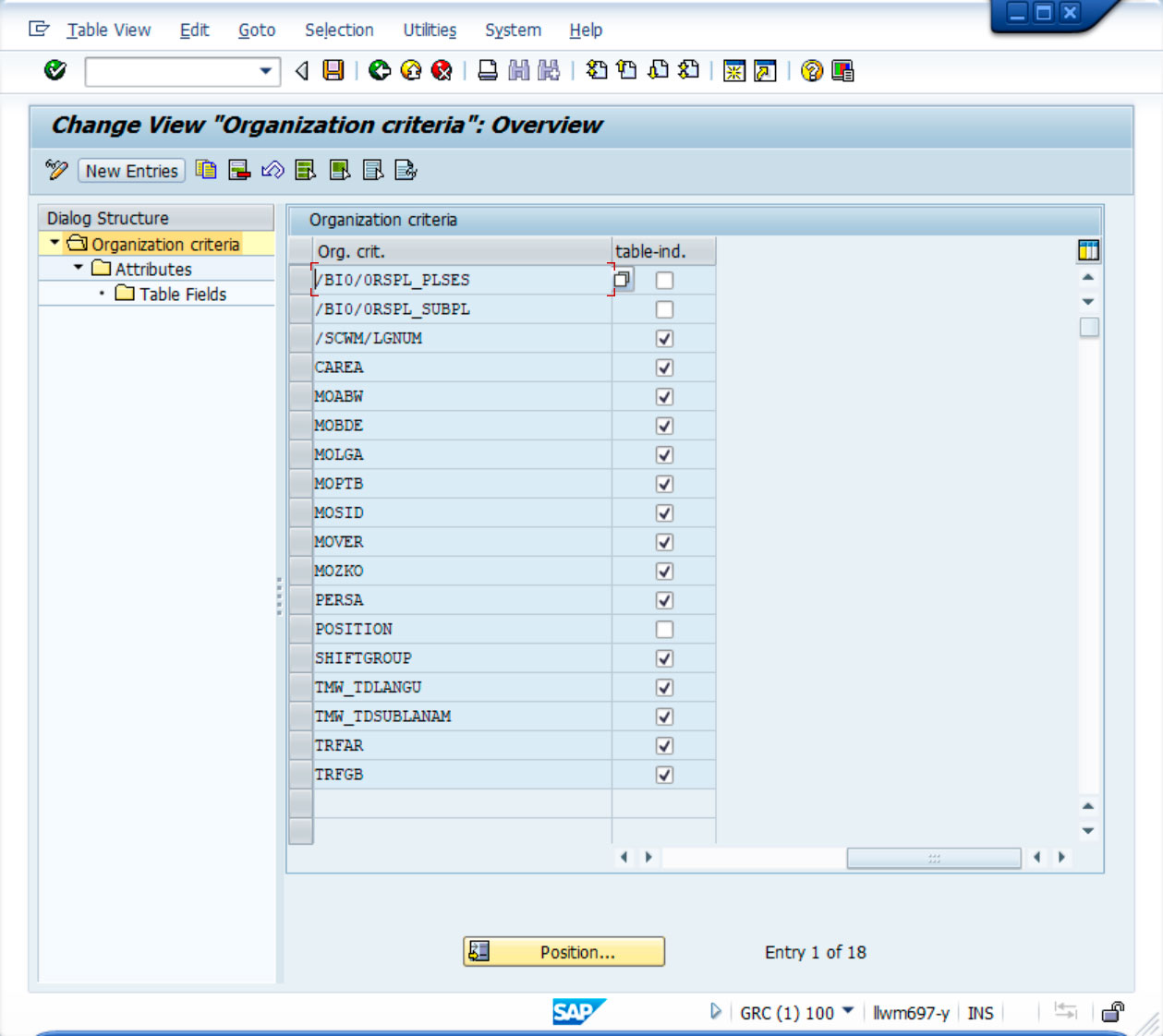
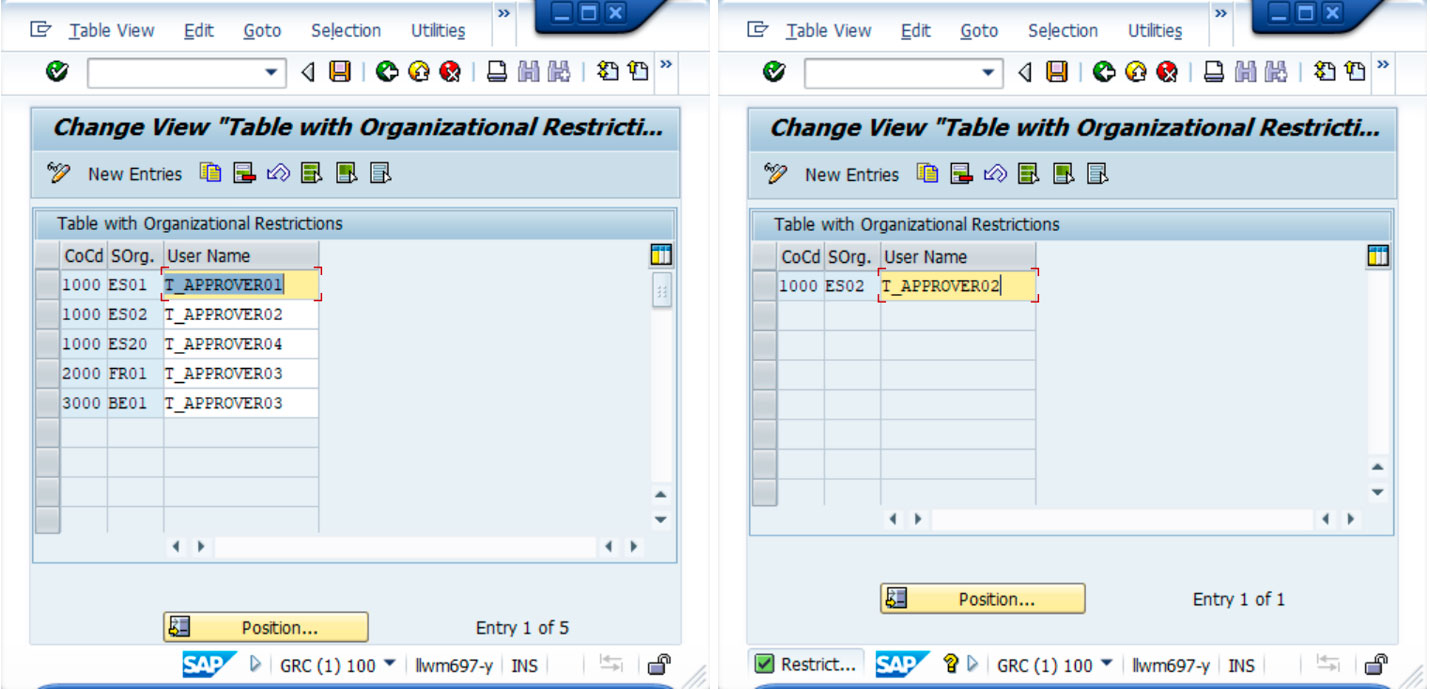
The following example provides a customised table that allows you to define approvers according to the Company (BUKRS) and the Sales Organisation (VKORG), on which you want to apply a restriction using these two fields:
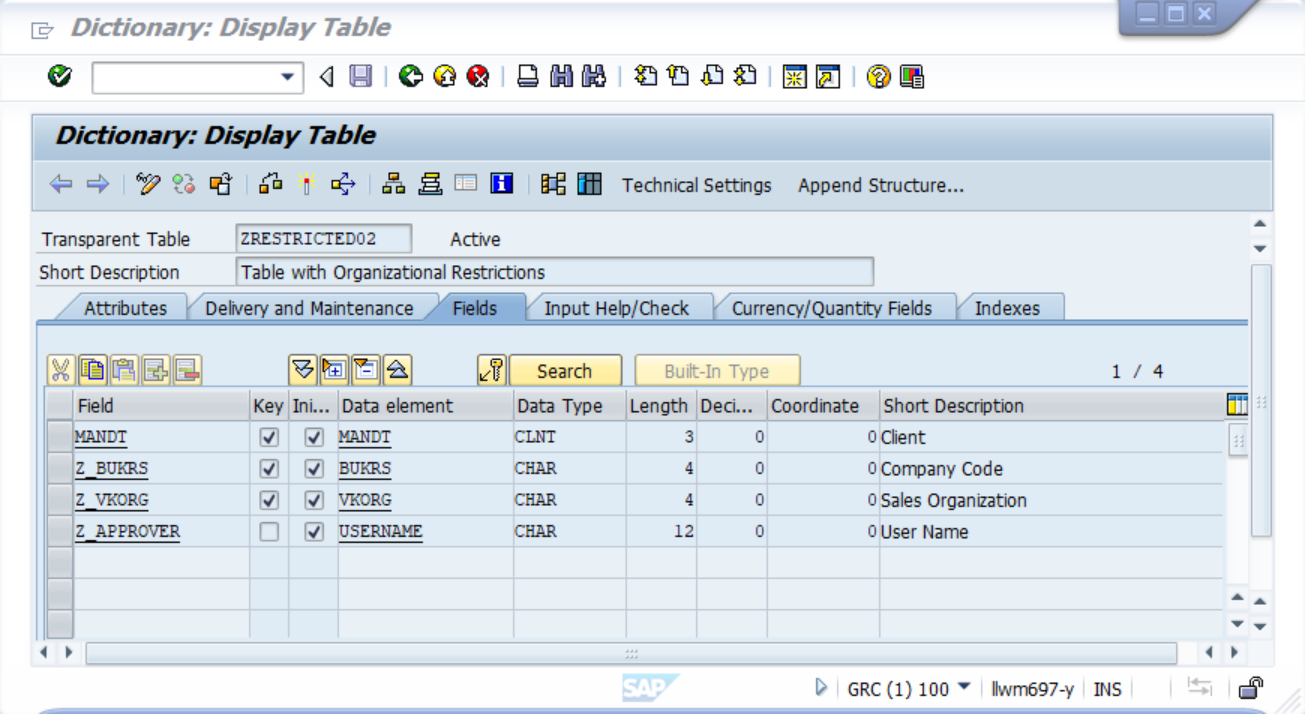
Organisational criteria have been defined for this table as follows:
1st) A new entry has been created with the name ZRESTRICTED02, as an example.
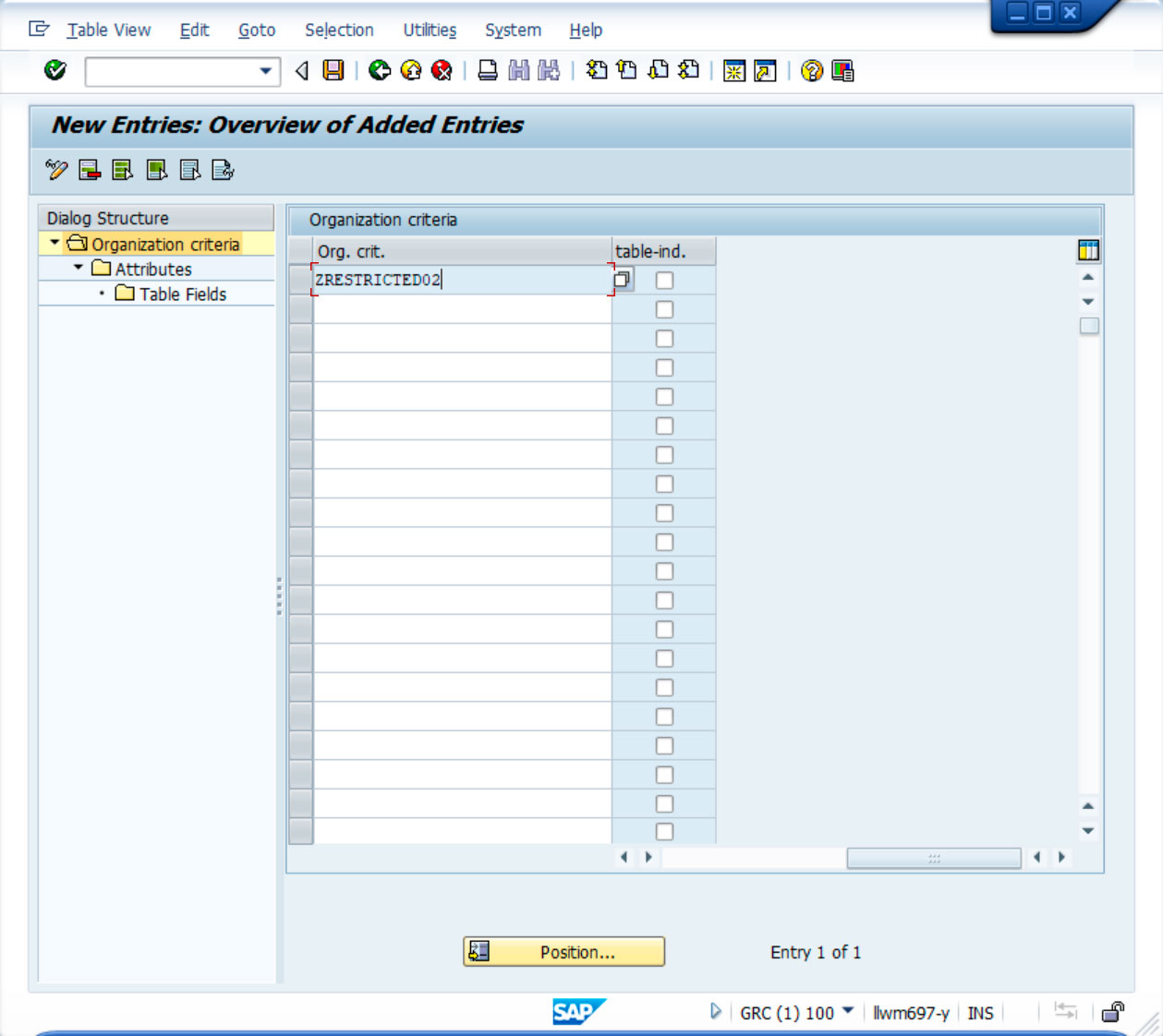
When you create the criteria, it is possible to unlink it to a specific table, which will make it apply to the whole system. To do this, the table-ind column must be selected.
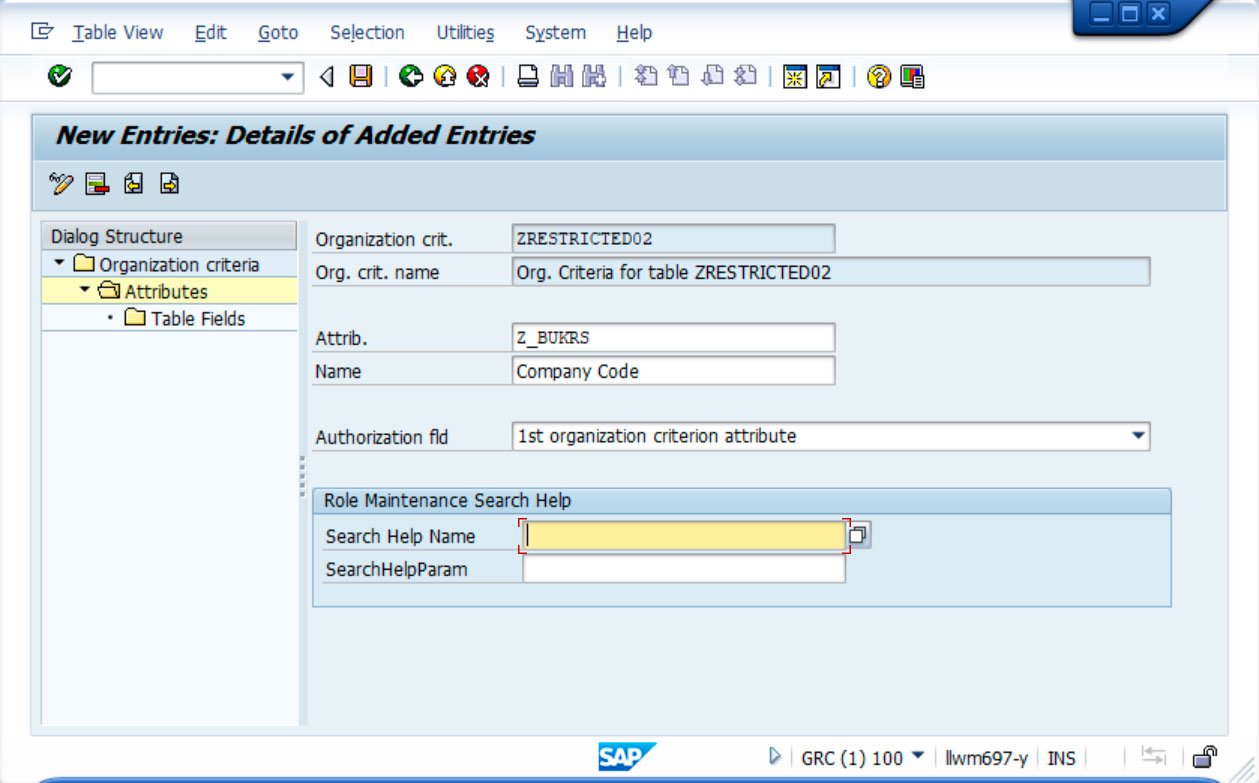
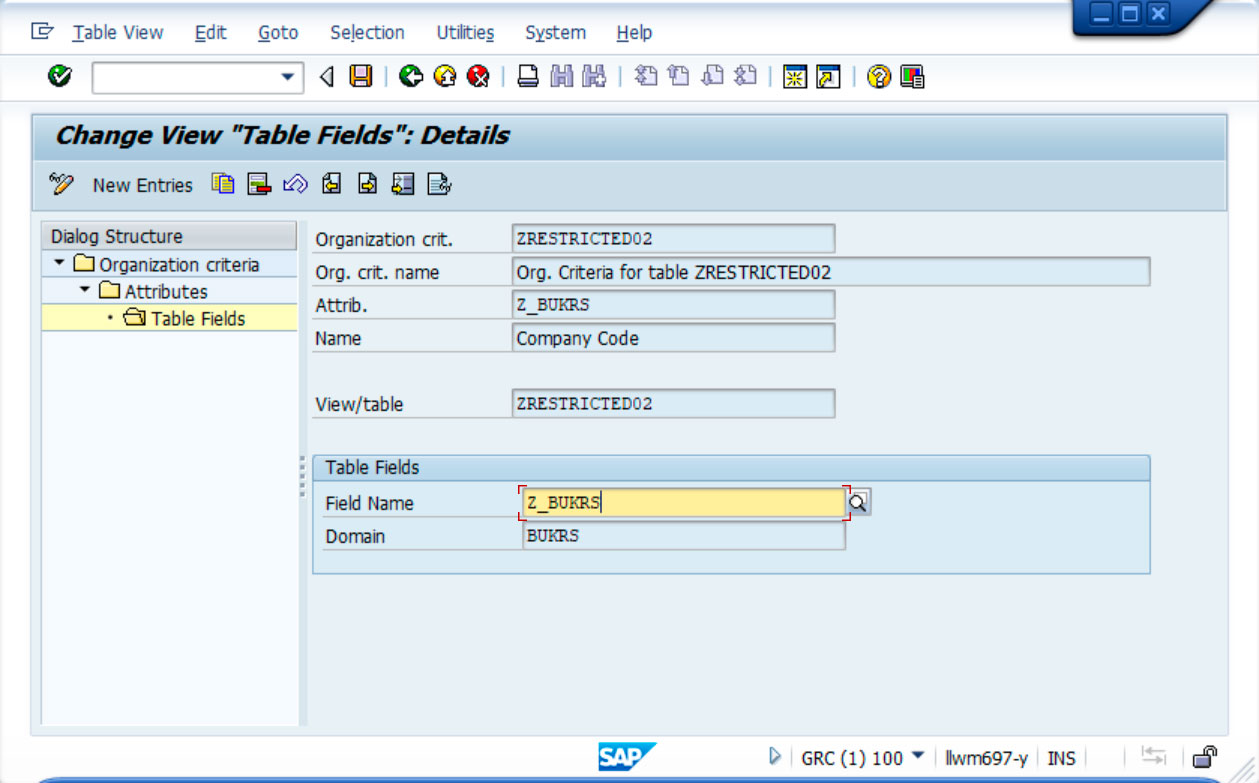
2º) A first attribute of the organisation criterion has been created with the name Z_BUKRS, which in turn has been linked to the field of the same name in the example table.
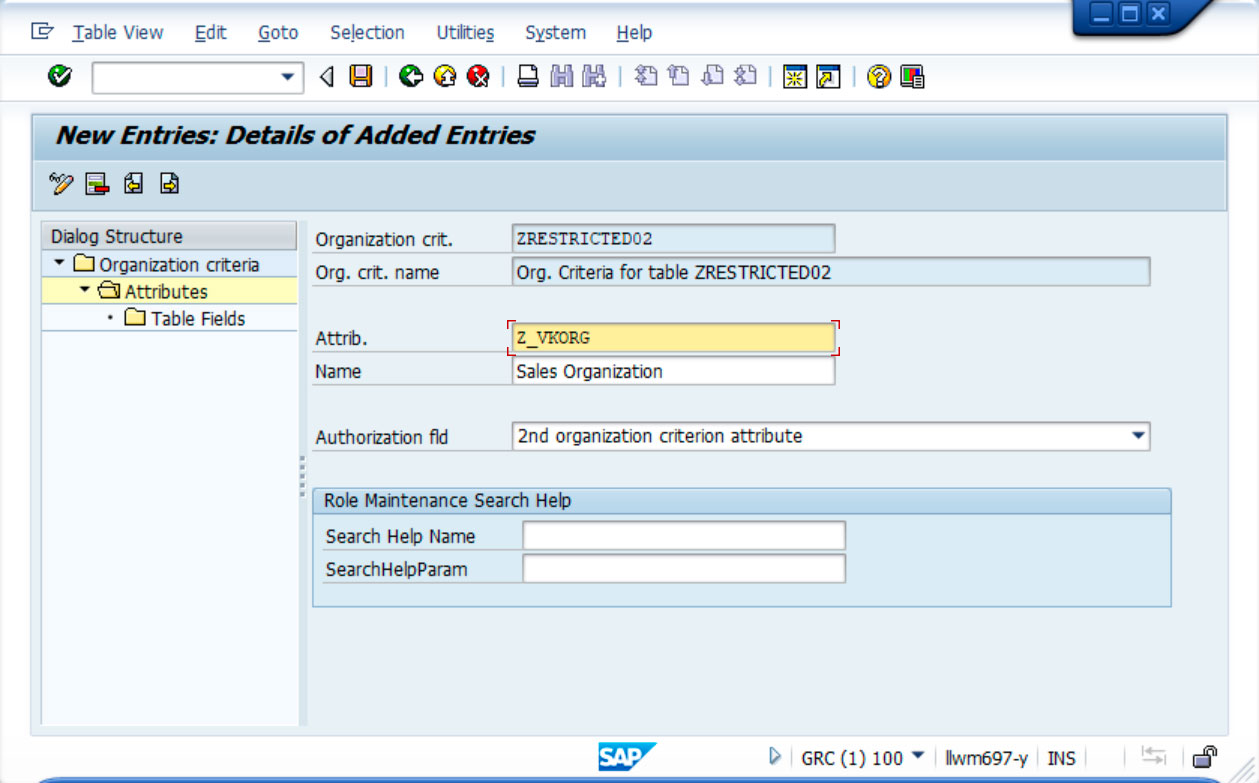
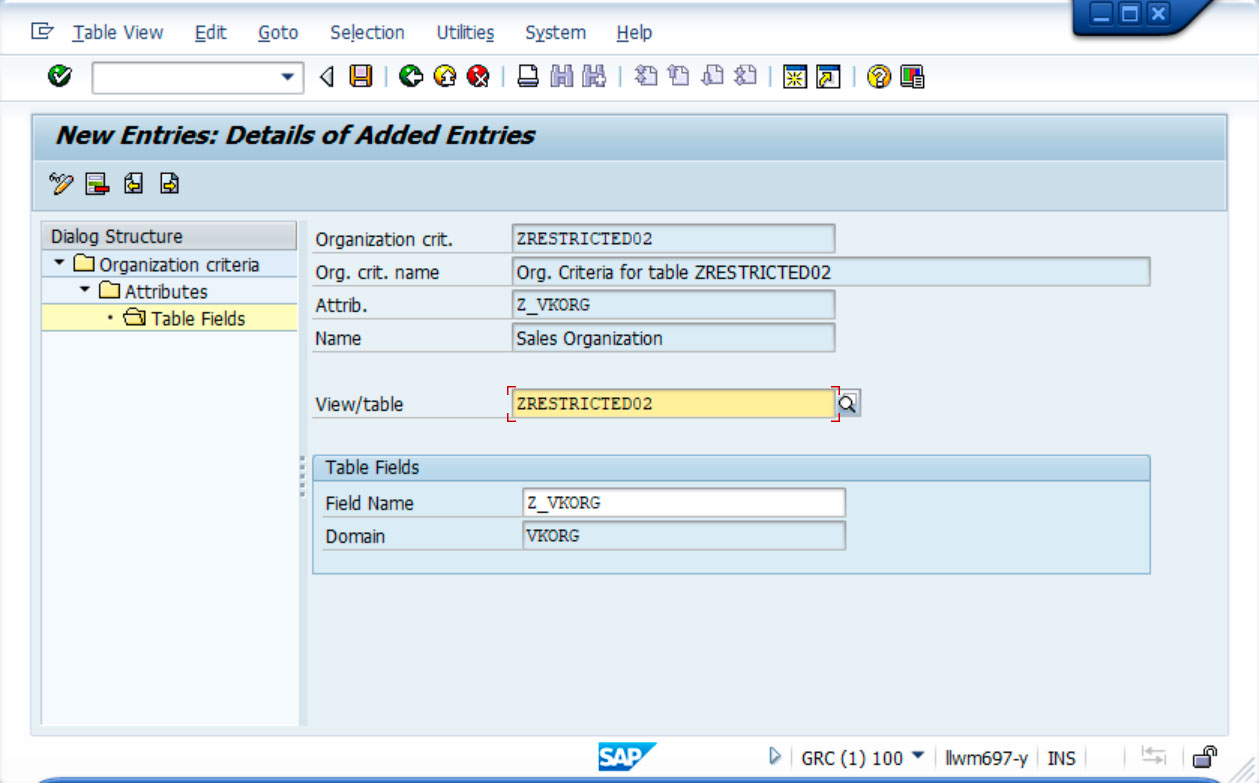
3º) A first attribute of the organisation criterion has been created with the name Z_VKORG, which in turn has been linked to the field of the same name in the example table.
At this point, an organisational criterion is already available for the example table ZRESTRICTED02.
The organisational criteria are defined independently of the client and are available in all of them. However, they operate in a client-dependent manner, so they must be activated in a client-specific manner where required.
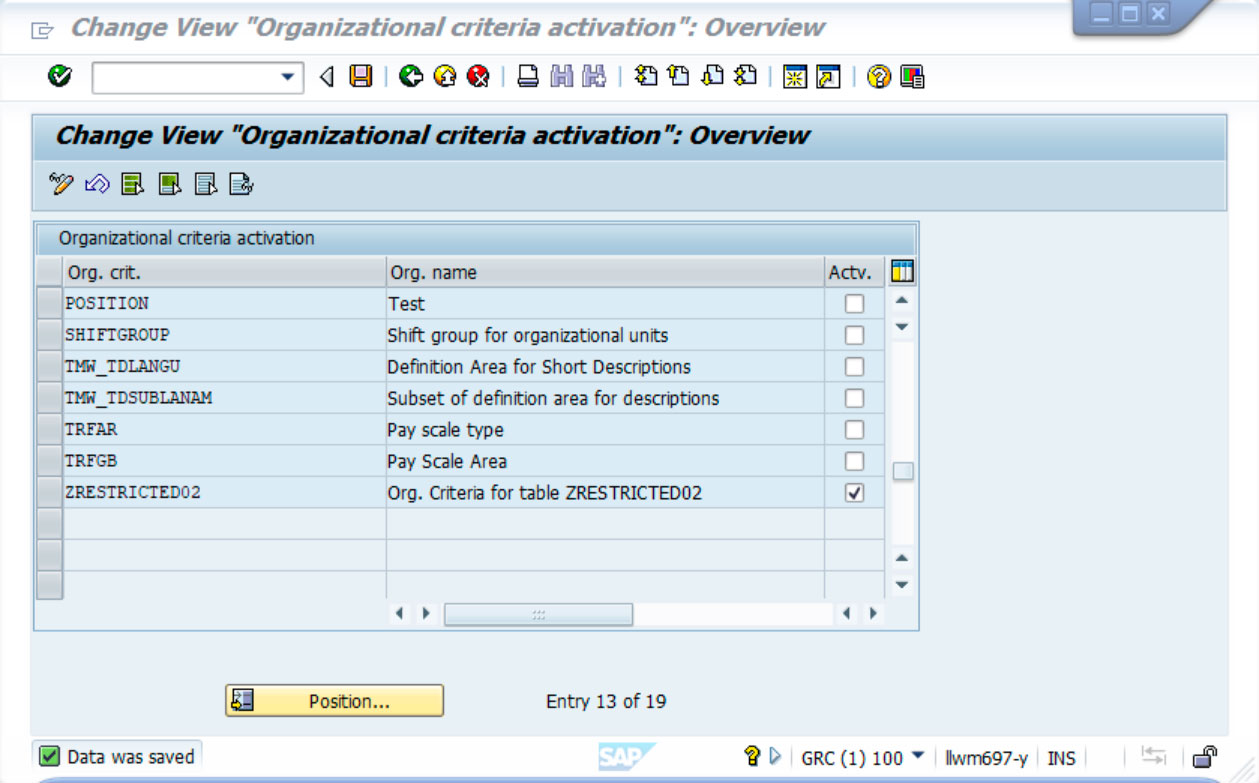
To activate an organisational criterion, this can be done from the Implementation Guide (SPRO) in the following path: SAP® NetWeaver → Application Server → System Management → Users and Authorisations → Line-Related Authorisations → Activate Organisational Criteria.
From this tool, the previously created organisational criteria have been activated by ticking the activated box and saving the changes.
Role and Authorisation Construction
The table maintenance transactions at first check the existing values for the S_TABU_DIS/S_TABU_NAM objects. If the check is successful, they check whether any organisational criteria have been defined for the key fields of the table. If so, it checks whether you have authorisation for the different values of the fields defined in the criterion, using the S_TABU_LIN object. Only those values for which the authorisation check is successful are displayed.
This behaviour inherent to standard maintenance transactions also extends to those parameter transactions that have been created from them. Therefore, the restrictions will also apply to custom table maintenance transactions.
Following the example above, a role has been created that will give a user access to modify the created table, but only for the desired values of Company and Sales Organisation.
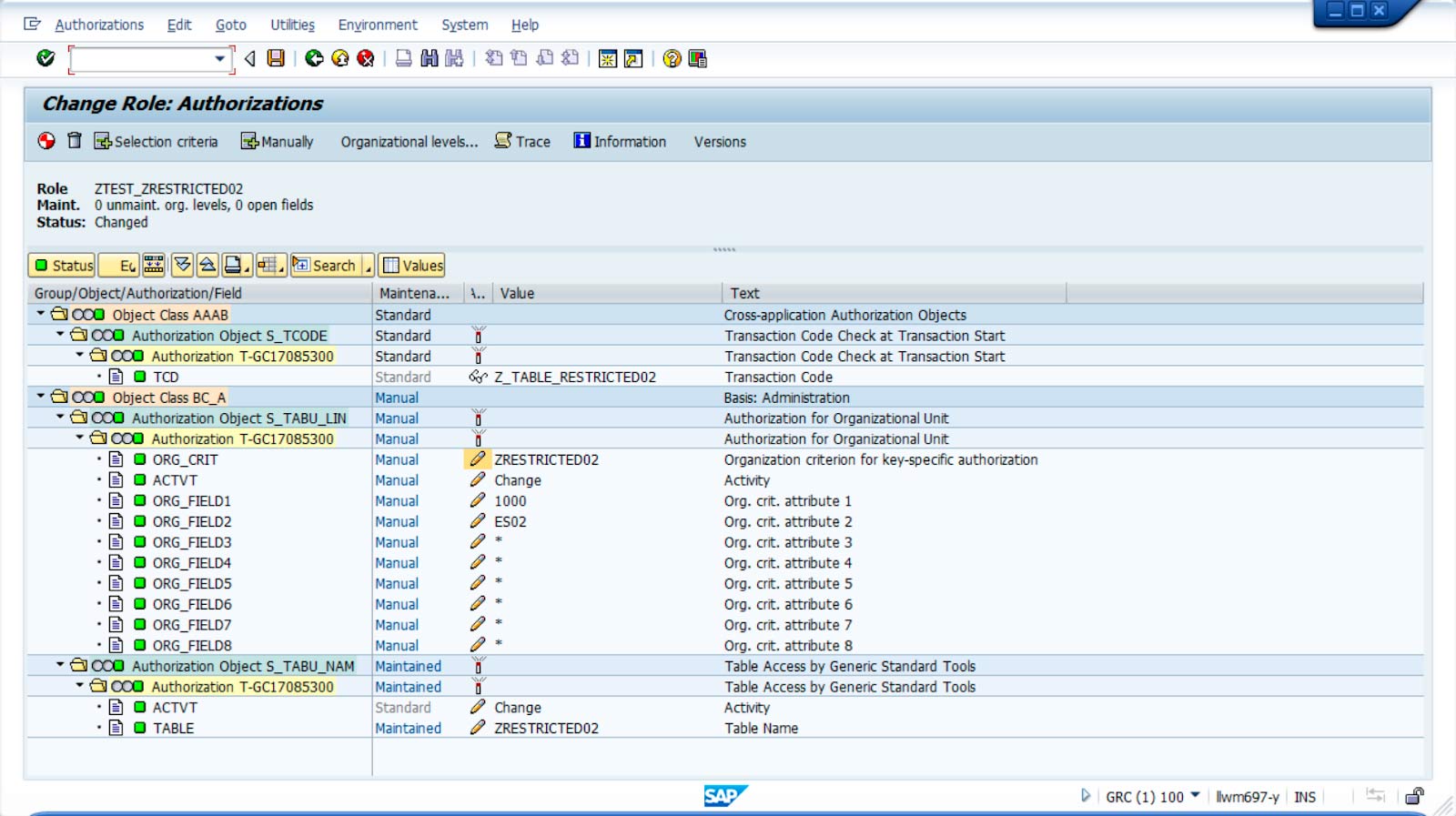
The role created includes the object S_TABU_NAM, which is necessary to give access to the table; but it also includes the object S_TABU_LIN, with the organisational criteria defined in the previous example and the values 1000 and ES02 for Company and Sales Organisation respectively.
Key Points
Tables will continue to be a widely used element in SAP®, both for configuration tasks and business needs. It is often necessary for users to be able to view and modify data, but at the same time it must be considered that the necessary tools are available to give these accesses in an appropriate, restricted way and always based on specific needs.
With the concept of line-related authorisations, more control is available with very little effort. These restrictions also become particularly relevant when customised tables come into play, where the fields do not necessarily have to match the standard, and often there are no authorisation objects that perfectly match what you want to restrict. In short, greater flexibility is achieved for the authorisation model and better protection of the information, adapted to the specific needs of the client.



