One more quarter, from Inprosec, we analyzed the notes published by SAP, this time those referring to the third quarter of 2018.
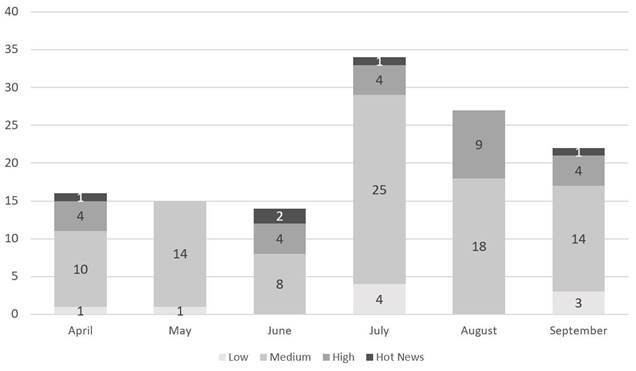
We have 1 critical note (Hot News) this quarter, although it is an update (it was published in April and updated in June, July and September) and 8 high level highlights, to which we will add a medium level note, the most critical in June for the detailed review of 10 notes.
- The most critical note (CVSS 9. 8), previous note update, is related to the “SAP Business Client” component and is a recurring note with the 4th update so far this year in September.
- In addition, we highlight one of the highest CVSS scores (8. 8) in relation to “SAP ECC Sales Support”..
We have a total of 83 notes for the entire quarter, 28 more than last quarter, (44 of the Tuesday patches, 12 more than last quarter):
- A total of 34 notes were published in July (16 in the Security Notes Tuesday – 11 new and 5 updates to previous notes).
- The only “hot news” (critical) is an update of a note from April of this year that had already been updated in June related to the “SAP Business Client” and to a CVSS of 9. 8, which will also be updated again in September and which we will detail although it is not a new note due to its relevance
- On the other hand, we have 4 high priority notes but all of them are updates of previous notes being the maximum criticality with a CVSS of 7. 3.
- This month the most predominant type is “Missing Authorization Check” (5/35 and 1/16 in patch day).
- A total of 27 notes have been published in August (14 in the Security Notes Tuesday – 12 new and 2 updates of previous notes).
- Although this month there is no “hot news” (critical), we have 9 highly critical notes (high priority), of which we highlight 4 being the new ones and with CVSS between 7. 2 and 8. 6.
- The most critical note (CVSS 8. 6) is the lack of an authorization check in the SAP SRM (Supplier Relationship Management) system.
- This month the most predominant types are “Missing Authorization Check” (6/27 and 1/14 in patch day) and “Information Disclosure” (5/27 and 2/14 in patch day).
- A total of 22 notes were published in September (14 in the Security Notes Tuesday – 13 new and 1 update of previous notes).
- The only “hot news” is again the update of an April note related to the “SAP Business Client” with its third update so far this year and a CVSS of 9. 8. Important to install it again.
- There are also a total of 4 high priority, 3 of which are very significant with a SVC of 8. 8 and the remaining with a SVC of 7. 5..
- This month the most predominant type is “Missing Authorization Check” (6/22 and 3/14 in patch day).
In the graph (September 2018 of SAP post) we can see the evolution and classification of the notes of the 3 months of the third quarter of the year (2018), in addition to the 3 months of the last quarter (only the notes of Sec. Tuesday / Patch Day – by SAP):
And in the following graph (September 2018 of ERP Scan post) we can see the same evolution, but including all the notes of the month, even those published in addition to the Sec. Tuesday / Patch Day:
All the details of the most relevant notes below:
- SAP Business Client has a security vulnerability (2622660): This note bundles multiple vulnerabilities. The bugs concern vulnerabilities in web browser controls that are used to display pages in SAP Business Client 6.5 PL5. Web browser controls are programmable building blocks that software developers use to embed web pages in their applications. Depending on the vulnerability, attackers can exploit a Memory corruption vulnerability for injecting specially crafted code into a working memory which will be executed by the vulnerable application. This can lead to taking complete control of an application, denial of service, command execution and other attacks. This fact has a negative influence on business processes and business reputation as a result. Install this SAP Security Note to prevent the risks. Updated in July & September 2018 (“If this note has been already implemented, then there is no action required.” Manual steps only have usability impact and no security implications). CVSS v3 Base Score: 9.8 / 10
- SAP ABAP has an Missing Authorization check vulnerability (2652578): An attacker can use a Missing authorization check vulnerability to access a service without any authorization procedures and to use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation, and other attacks. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 6.4 / 10
- SAP SRM MDM Catalog has a Missing Authorization check vulnerability (2655250): An attacker can use the vulnerability to access a service without any authorization procedures and to use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation, and other attacks. Install this SAP Security Note to prevent the risks. CVSS Base Score: 8.6 / 10
- SAP BI Launchpad Web Intelligence has an SQL Injection (SQLi) vulnerability (2644154): An attacker can use this vulnerability with a help of specially crafted SQL queries. He or she can read and modify sensitive information in a database, execute administration operations, destroy data or make it unavailable. In some cases, the hacker can access system data or execute OS commands. Install this SAP Security Note to prevent the risks. CVSS Base Score: 7.7 / 10
- SAP BusinessObjects Business Intelligence platform has a Memory Corruption vulnerability (2614229): An attacker can use Buffer overflow vulnerability for injecting specially crafted code into a working memory which will be executed by vulnerable application. Executed commands will run with the same privileges of a service that executed a command. This can lead to complete control of an application, denial of service, command execution, and other attacks. In case of command execution, attackers can obtain critical technical and business-related information stored in a vulnerable SAP system or use it for privilege escalation. Speaking about denial of service, it is possible to terminate a process of a vulnerable component so that nobody can use this service. Install this SAP Security Note to prevent the risks. CVSS Base Score: 7.5 / 10
- SAP MaxDB/liveCache has a SQL Injection Vulnerability (2660005): This is a security issue with the SAP live cache technology in MaxDB versions 7.8 and 7.9. It allows an attacker to get the DBM operator privileges and abuse them to, at the end, read, modify or delete sensitive information from the database. The required update of the software solves the problem by removing those abusable privileges from the DBM operator. CVSS Base Score: 7.2 / 10
- SAP ECC Sales Support has a Missing Authorization check vulnerability (2449974): An attacker can use this vulnerability to access a service without any authorization procedure and employ service functionality that has restricted access. This can lead to information disclosure, privilege escalation, and other attacks. Install this SAP Security Note to prevent the risks. CVSS Base Score: 8.8 / 10
- SAP Business One and SAP HANA Installer has an Information Disclosure vulnerability (2670284): An attacker can use the Information disclosure vulnerability to reveal additional information (system data, debugging information, etc.) which would help to learn about a system and plan other attacks. Install this SAP Security Note to prevent the risks. CVSS Base Score: 8.8 / 10
- SAP BEx Web Java Runtime Export Web Service has a Missing XML Validation (XXE) vulnerability (2644279): An attacker can use XML external entity vulnerability to send specially crafted unauthorized XML requests, which would be processed by XML parser. The attacker would gain unauthorised access to OS filesystem. Install this SAP Security Note to prevent the risks. CVSS Base Score: 8.8 / 10
- SAP HANA, Extended Application Services classic model has a Missing XML Validation vulnerability in (2681207): SAP HANA, Extended Application Services classic model OData parser does not sufficiently validate XML. By exploiting, an unauthorized hacker can cause the database server to crash. CVSS Base Score: 7.5 / 10
INCIBE CERT reference links in relation to the publication of the notes for the 3 months of this quarter
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-julio-2018
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-agosto-2018
Other references, in English from SAP, Onapsis and ERPScan (in order: July->September):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=497256000
https://www.onapsis.com/blog/SAP-Security-Notes-July-18-rise-of-security-notes
https://erpscan.io/press-center/blog/sap-cyber-threat-intelligence-report-july-2018/
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=499352742
https://www.onapsis.com/blog/sap-patch-notes-august-2018
https://erpscan.io/press-center/blog/sap-cyber-threat-intelligence-report-august-2018/
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=499356993
https://www.onapsis.com/blog/sap-patch-notes-september-2018
https://erpscan.io/press-center/blog/sap-cyber-threat-intelligence-report-september-2018/