Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
Today we bring you the update of the Q4 2020 SAP security notes. In this quarter there has been a slight increase in the number of notes in relation to the previous quarter, in addition, we continue to have a significant number of critical notes and in the same quarter we have four new notes of maximum criticality (CVSS 10). It should be noted that at least three of them could have a considerable impact, since they are precisely for SAP Solution Manager (which is the recommended tool for the management and application of the notes).
Q4 2020 notes
Summary and highlights of the quarter
As mentioned above, the total number of notes/patches has increased compared to the last quarter. It also increases the number of critical and high notes. Unlike other quarters where we didn’t find any low scores, they are present in this quarter. As always we will leave the average and low grades unchecked this quarter, but we will detail a total of 24 grades (all those with a CVSS of 7 or higher). As we said, it is important to note that the critical notes are especially high (CVSS).
We have 8 new Hot News, totaling 12 this quarter. We will also review in detail 12 of the total 12 high scores (those of CVSS greater or equal to 7) for the detailed review of 24 different scores.
- The most critical notes of the quarter (all four with CVSS 10) would be two related to the lack of authentication verification in SAP Solution Manager, one related to the lack of authentication verification in SAP NetWeaver AS JAVA, and one affecting CA Introscope Enterprise Manager.
- The next in criticality (CVSS 9.8) are 2. One is the usual “Browser Control Chromium Delivered with SAP Business Client (2622660)” and another is related to multiple vulnerabilities in SAP Data Services.
- From there, we have a review with CVSS of 9.6, four with 9.1 and the last one with a CVSS of 9.
- Among the high level ones, perhaps we should point out that there is one that would be affecting Solution Manager, with CVVS of 8. 5, and another one for SAP NetWeaver (ABAP Server) and ABAP Platform, with CVSS of 8. 3, being an update of the month of August.
We have a total of 62 notes for the entire quarter, 1 more than last quarter (49 of the Tuesday patches, 7 more than last quarter):
- A total of 29 notes were released in October (21 in the Security Notes Tuesday – 15 new and 6 updates to previous notes).
- We have 1 new critical note (Hot News), being the total of 2 in this month that stand out for their high CVVS, one of them the recurrent update for the SAP Business Client with Chromium . In addition we will review in detail 7 of the total 7 high notes (those of CVSS greater or equal to 7) where this month we located 3 new and 4 updates.
- The most critical note of the month (with CVSS 10) is an OS Command Injection Vulnerability in CA Introscope Enterprise Manager that affects SAP Solution Manager and SAP Focused Run.
- The next critical note (CVSS 9. 8) is a note that is repeated for “Browser Control Chromium Delivered with SAP Business Client (2622660)”.
- From there, we located the 7 notes of high criticality (high priority) being the most relevant with a CVSS of 8.3 an update that affects SAP NetWeaver (ABAP) and ABAP Platform. The rest (20) are medium and low level, and we will not see them in detail, although it is worth noting that there are more than one that affects the SAP Commerce Cloud.
- This month the most predominant types are “Cross-Site Scripting (XSS)” (8/29 and 6/21 in patch day) and “Missing Authorization Check” (5/29 and 2*/21 in patch day).
- A total of 19 notes were published in November (15 in the Security Notes Tuesday – 12 new and 3 updates to previous notes).
- In addition we have a total of 6 “hot news” (critical), highlighting 2 notes with the maximum note of CVVS (10), which would be the lack of authentication checks in Solution Manager and an update of the note that we saw in May and allowed attackers to execute arbitrary commands, compromising the integrity of the system.
- The most critical notes of the month (both with CVSS 10) would be one that affects the lack of authentication check in SAP Solution Manager and another an update of a May note.
- The next in criticality (CVSS 9. 8) is a note that resolves several vulnerabilities in SAP Data Services that compromised system integrity.
- From there, we have two critical notes with a CVSS of 9. 1, and another with a CVSS of 9.
- There are also a total of 3 high level notes, one affecting SAP Fiori Launchpad, with a note of 8. 6, and 2 related to SAP Commerce Cloud, both with CVVS 7. 5. The rest (10) are medium and low level, and we will not see them in detail.
- This month the most predominant types are “Information Disclosure” (3/19 and 4/15 in patch day), “Missing Authorization Check” (2/19 and 3/15 in patch day) and “Missing Authentication Check” (2/19 and 5/15 in patch day).
- A total of 14 notes were published in December (13 in the Security Notes Tuesday – 11 new and 2 updates to a previous note).
- We have 3 new critical notes (Hot News), being the total of 4 in this month that stand out for their high CVVS.
- The most critical note of the month (with CVSS 10) is a Missing Authentication Check affecting SAP NetWeaver AS JAVA (P2P Cluster Communication).
- Next in critical (CVSS 9. 6) is a Missing XML Validation note affecting the AP BusinessObjects Business Intelligence Platform.
- From there, we located the 2 notes of high criticality (high priority) being the most relevant with a CVSS of 8.5 a new note that affects SAP Solution Manager 7. 2. The rest (8) are of medium and low level, and we will not see them in detail, although it is worth noting that there are more than one that affects SAP NetWeaver.
- This month the most prevalent types are “Code Injection” (2/14 and 2/13 in patch day) and “Missing Authentication Check” (2/14 and 1/21 in patch day).
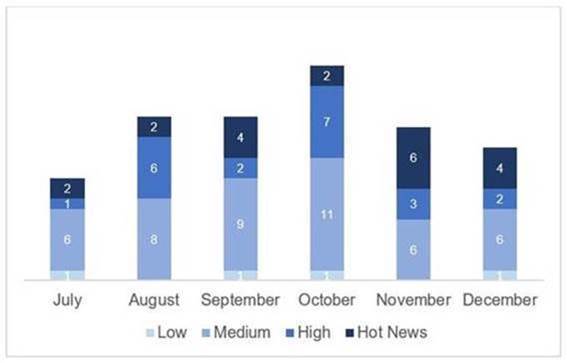
In the graph (post December 2020 of SAP) we can see the evolution and classification of the notes of the 3 months of the last quarter of the year (2020), in addition to the 3 months of the last quarter (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The full details of the most relevant notes are as follows:
- OS Command Injection Vulnerability in CA Introscope Enterprise Manager (Affected Products: SAP Solution Manager and SAP Focused Run) (2969828): It affects all CA Introscope Enterprise Manager versions with release 10.7.0.304 or lower. The vulnerability can allow an attacker to inject OS commands and thus gain complete control of the host running the CA Introscope Enterprise Manager. The CVSS score of 10 considers the fact that an exploit can be started remotely and does not require authentication or any privileges. CVSS v3 Base Score: 10 / 10 (CVE-2020-6364]).
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This note addresses multiple vulnerabilities in the third-party web browser control Chromium, which is used in SAP Business Client and is periodically updated based on web browser updates. Since exploits for third-party tools are more common than exploits that are SAP-specific, which tend to be more targeted and selective, it is important to keep this note installed with every update to stay secure. This update patches 25 security issues, seven of them with High Priority. CVSS v3 Base Score: 9.8 / 10.
- Update – Code Injection Vulnerability in SAP NetWeaver (ABAP) and ABAP Platform (2941667): This note has been re-released with the updated automatic correction instruction for NW Release 750 to additionally cover SP00 to SP05. SAP NetWeaver (ABAP Server) and ABAP Platform allows a low privileged attacker to inject code by executing an ABAP report over the network. An attacker could so get access to data, overwrite arbitrary SAP programs including essential logon program and could thereby lead to a Denial of Service. CVSS v3 Base Score: 8.3 / 10 (CVE-2020-6296).
- Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Composite Application Framework (2972661): It allows an unauthenticated attacker to trick an unsuspecting authenticated user to click on a malicious link. The end user’s browser has no way to know that the script should not be trusted, and will execute the script, resulting in sensitive information being disclosed or modified. CVSS v3 Base Score: 8.2 / 10 (CVE-2020-6367).
- Missing XML Validation in SAP NetWeaver (Compare Systems) (2969457): A missing XML validation allows an attacker with administrative privileges to retrieve arbitrary files from the OS level of the application server and/or to start a denial-of-service attack.. CVSS v3 Base Score: 7.6 / 10 (CVE-2020-6366).
- Hard-coded Credentials in CA Introscope Enterprise Manager (Affected products: SAP Solution Manager and SAP Focused Run) (2971638): It allows a remote attacker to bypass authentication if the default passwords for Admin and Guest have not been changed. CVSS v3 Base Score: 7.5 / 10 (CVE-2020-6369).
- Update – Missing Authentication check in SAP NetWeaver AS JAVA (2941315): This note has been re-released with updated ‘Support Packages & Patches’ information. For the release ESI – WSRM 7.11, we added the Patch level 000001 under SP019 and for the release ENGINEAPI 7.10, we added the Patch level 000007 under SP024.SAP NetWeaver application exposes a web service which does not perform any authentication checks leading to complete denial of service. The solution: Update to latest available patch level as mentioned in the note. CVSS v3 Base Score: 7.5 / 10 (CVE-2020-6309).
- Update – Information Disclosure in SAP Business Objects Business Intelligence Platform (dswsbobje Web Application) (2898077): This note has been re-released with updated ‘Support Packages & Patches’ information. For the release SBOP BI PLATFORM SERVERS 4.2, we added the Patch level 001000 under SP007.Under certain conditions SAP Business Objects – dswsbobje web application allows an attacker to access information which would otherwise be restricted. Some well-known impacts of Information Disclosure are: loss of information and system configuration confidentiality or information gathering for further exploits and attacks. CVSS v3 Base Score: 7.5 / 10 (CVE-2020-6238).
- Privilege Escalation in SAP Landscape Management (SAP Adaptive Extensions) (2902456): This note has been re-released with updated ‘Support Packages & Patches’ information. We added the patch 000053 for the component SAP ADAPTIVE EXTENSIONS 1.0. An attacker with admin_group privileges could change ownership and permissions of arbitrary files remotely. This results in the possibility to execute these files as root user from a non-root context. The solution: Install SAP Adaptive Extensions patch 53 or newer. CVSS v3 Base Score: 7.2 / 10 (CVE-2020-6236).
- Missing Authentication Check in SAP Solution Manager (JAVA stack) (2985866): Some Authentication checks are missing in SAP Solution Manager (software component LM-SERVICE). An un-authenticated attacker is able to compromise the system. This has an impact to the integrity as well as availability of the service. The fix enables user authentication. CVSS v3 Base Score: 10 / 10 (Multiple CVE IDs).
- Update – Missing Authentication Check in SAP Solution Manager (2890213): SAP Solution Manager User-Experience Monitoring does not perform any authentication for a service resulting in complete compromise of all SMDAgents connected to the Solution Manager. This fix enables user authentication on the User-Experience Monitoring administration service and thereby removes the root cause of finding CVE-2020-6207. CVSS v3 Base Score: 10 / 10 (CVE-2020-6207).
- Multiple Vulnerabilities in SAP Data Services (2982840): An insufficient input validation allows an unauthenticated attacker to send malicious requests that could result in remote code execution and thus, a complete compromise of system confidentiality, integrity and availability.. CVSS v3 Base Score: 9.8 / 10 (Multiple CVE IDs).
- Code Injection in SAP AS ABAP and S/4 HANA (DMIS) (2973735): SAP AS ABAP and SAP S/4 HANA allows an authenticated attacker to inject arbitrary code in the application and change the course of execution. Due to lack of input validation, an attacker, who was granted access (S_RFC) to execute the function module can inject malicious ABAP code, which will be saved persistently in a report in the ABAP repository. This report can then be executed by using the remote function module without additional authorization checks. The successful exploitation of the identified vulnerability can allow the attacker to take complete control of the affected system. The solution for the issue is to introduce an authorization check (object S_DMIS, level ‘Package’, and activity value ’01’ – create and generate) in the affected function module, and to remove/delete the generated coding from the ABAP repository. The generated report still exists but without any coding, therefore removing the possibility to exploit the identified vulnerability. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-26808).
- Privilege escalation in SAP NetWeaver Application Server for Java (UDDI Server) (2979062): The UDDI Server of SAP NetWeaver Application Server for Java allows an attacker to execute arbitrary OS commands without having the required permissions, known as escalation of privileges vulnerability. Potential impact is total compromise of confidentiality, integrity and availability of server OS. Arbitrary OS command execution is now prevented by prefer list approach. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-26820).
- Update – Cross-Site Scripting (XSS) in SAP NetWeaver (Knowledge Management) (2928635): SAP NetWeaver Knowledge Management (KM) allows the automatic execution of script content in a stored file due to inadequate filtering with the accessing user’s privileges. If the accessing user has administrative privileges, then the execution of the script content could result in complete compromise of system confidentiality, integrity and availability. Malicious resource execution in SAP NetWeaver Knowledge Management is fixed now. CVSS v3 Base Score: 9 / 10 (CVE-2020-6284).
- Security Vulnerabilities in SAP Fiori Launchpad (NewsTile Application) (2984627): SAP Fiori Launchpad News tile Application allows an unauthorized attacker to send a crafted request to a vulnerable web application, resulting in a Server-Side Request Forgery vulnerability. Besides, an unauthorized attacker can use SAP Fiori Launchpad News tile Application to send malicious code, to a different end user (victim), because News tile does not sufficiently encode user controlled inputs, resulting in Reflected Cross-Site Scripting (XSS) vulnerability. In order to solve this issue, the affected system components no longer reveal internal information to non-authenticated users. CVSS v3 Base Score: 8.6 / 10 (CVE-2020-26815 and CVE-2020-26825)
- Information Disclosure in SAP Commerce Cloud (2975189): An attacker can bypass existing authentication and permission checks via the «/medias» endpoint in SAP Commerce, hence gaining access to Secure Media folders. This folder could contain sensitive files that results in disclosure of sensitive information and impact system configuration confidentiality. Additional controls have been implemented to restrict access to secure media folders. CVSS v3 Base Score: 7.5 / 10 (CVE-2020-26809).
- Multiple Vulnerabilities in SAP Commerce Cloud (Accelerator Payment Mock) (2975170): An unauthenticated attacker can submit a crafted request over a network to a particular SAP Commerce module URL which will be processed without further interaction. There is a crafted request which can render the SAP Commerce service itself unavailable with no impact on confidentiality or integrity. Users of SAP Commerce can protect from this vulnerability by upgrading to the latest patch release. CVSS v3 Base Score: 7.5 / 10 (CVE-2020-26810 and CVE-2020-26811).
- Missing Authentication Check In SAP NetWeaver AS JAVA (P2P Cluster Communication) (2974774): P2P Cluster Communication is dedicated for the server nodes in the cluster to exchange messages between each other. However, due to implementation flaw, it accepts arbitrary connections even from processes that are outside the cluster and even outside the network segment dedicated for the internal cluster communication. As result, an unauthenticated attacker can invoke certain functions that would otherwise be restricted to system administrators only, including access to system administration functions or shutting down the system completely. The solution: The Server Socket for P2P communication now listens only on the network interface dedicated to internal cluster communication. Extra security measures have been introduced in the P2P handshake protocol so that if attackers gain access to the network segment dedicated to the AS Java Cluster, they cannot establish connection to the P2P Server Socket of any server nodes in the Cluster. CVSS v3 Base Score: 10 / 10 (CVE-2020-26829).
- Missing XML Validation in SAP BusinessObjects Business Intelligence Platform (Crystal Report) (2989075): Fixes a Missing XML Validation vulnerability in the Crystal Report component of SAP Business Objects. An exploit would allow an attacker with basic privileges to inject arbitrary XML entities leading to the disclosure of internal files and directories and allowing Server Side Request Forgery (SSRF) as well as Denial-of-Service (DoS) attacks. CVSS v3 Base Score: 9.6 / 10 (CVE-2020-26831).
- Code Injection vulnerability in SAP Business Warehouse (Master Data Management) and SAP BW4HANA (2983367): Describes a Code Injection vulnerability which affects SAP BW Master Data Management and SAP BW4HANA. Only the fact that an attacker requires high privileges prevents the vulnerability from becoming the sixth CVSS 10 vulnerability in 2020. Having these privileges, an attacker can submit crafted requests to generate and execute arbitrary code without any additional user interaction and thus, potentially leading to a full compromise of the system’s confidentiality, integrity, and availability. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-26838).
- Update – Code Injection in SAP AS ABAP and S/4 HANA (DMIS) (2973735): The patched vulnerability affects the SAP Landscape Transformation (SLT) component of SAP NetWeaver AS ABAP and S/4 HANA systems and allows a remote attacker to inject and execute arbitrary code and thus taking complete control of the affected system. CVSS v3 Base Score: 9.1 / 10 (CVE-2020-26808).
- Path traversal and Missing Authorization check in SAP Solution Manager 7.2 (User Experience Monitoring) (2983204): This note solves a Path Traversal vulnerability and a Missing Authentication vulnerability in the User Experience Monitoring component of Solution Manager. Exploiting both vulnerabilities, a remote attacker having access to an unprivileged user could partially compromise availability in making certain services unavailable. The exploits would even allow the attacker to gain access to sensitive information such as usernames and passwords that can be used to access other SAP systems in the landscape. CVSS v3 Base Score: 8.5/ 10 (CVE-2020-26837).
- Missing Authorization check in SAP NetWeaver AS ABAP and SAP S4 HANA (SAP Landscape Transformation) (2993132): Fixes an issue in the SLT component of SAP NetWeaver AS ABAP and S/4 HANA systems. A missing explicit authorization check-in a remote enabled function module allowed a high privileged user to execute functions to which access should be restricted. CVSS v3 Base Score: 7.6 / 10 (CVE-2020-26832).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for the 3 months of this quarter:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-octubre-2020
Other references, from SAP and Onapsis (in order: October ->December):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=558632196
https://onapsis.com/blog/sap-security-notes-October-2020
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=562725571
https://onapsis.com/blog/sap-security-notes-november-2020
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=564757079
https://onapsis.com/blog/sap-security-notes-december-2020
Resources affected
- BANKING SERVICES FROM SAP 9.0 (Bank Analyzer), versión 500;
- S/4HANA FIN PROD SUBLDGR, versión 100;
- SAP 3D Visual Enterprise Viewer, versión 9;
- SAP Adaptive Extensions, versión 1.0;
- SAP Adaptive Server Enterprise, versiones 15.7, 16.0.
- SAP AS ABAP(DMIS), versiones 2011_1_620, 2011_1_640, 2011_1_700, 2011_1_710, 2011_1_730, 2011_1_731, 2011_1_752 y 2020;
- SAP Business Client, versión 6.5;
- SAP Business Objects Business Intelligence Platform, versiones 4.1, 4.2 y 4.3.
- SAP Business Objects BI Platform (Crystal Report), versiones 4.1, 4.2 y 4.3;
- SAP Business Planning y Consolidation, versiones 750, 751, 752, 753, 754, 755, 810, 100 y 200;
- SAP Business Warehouse, versiones 700, 701, 702, 731, 740, 750, 751, 752, 753, 754, 755 y 782;
- SAP BW4HANA, versiones 100 y 200;
- SAP Commerce Cloud, versiones 1808, 1811, 1905 y 2005;
- SAP Data Services, versión 4.2;
- SAP Disclosure Management, versión 10.1;
- SAP ERP, versiones 600, 602, 603, 604, 605, 606, 616, 617 y 618;
- SAP ERP (HCM Travel Management), versiones 600, 602, 603, 604, 605, 606, 607 y 608;
- SAP ERP Client para E-Bilanz 1.0, versión 1.0;
- SAP Fiori Launchpad (News Tile Application), versiones 750, 751, 752, 753, 754 y 755;
- SAP HANA Database, versión 2.0.
- SAP Landscape Management, versión 3.0;
- SAP NetWeaver:
- ABAP Server y ABAP Platform, versiones 700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 753 y 755;
- AS ABAP, versiones 620, 640, 700, 710, 730, 731, 740, 750, 751, 752, 753 y 754;
- AS ABAP (POWL test application), Versiones – 710, 711, 730, 731, 740, 750
- Composite Application Framework, versiones 7.20, 7.30, 7.31, 7.40, 7.50;
- DI Design Time Repository versiones 7.11, 7.30, 7.31, 7.40, 7.50;
- Enterprise Portal (Fiori Framework Page), versiones 7.50, 7.31, 7.40;
- SAP NetWeaver AS JAVA (P4 Protocol), versiones:
- AS Java, versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40, 7.50;
- ENGINEAPI versiones 7.10;
- J2EE-FRMW versiones 7.10, 7.11;
- WSRM versiones 7.10, 7.11, 7.20, 7.30, 7.31, 7.40, 7.50;
- SAP Process Integration (PGP Module – Business-to-Business Add On), versión 1.0;
- SAP S4 HANA, versiones 100, 101, 102, 103, 104 y 105;
- SAP Solution Manager y SAP Focused Run, versiones 9.7, 10.1, 10.5 y 10.7;
- SAP UI 700, versión 2.0;
- SAP UI, versiones 7.5, 7.51, 7.52, 7.53 y 7.54.