Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
September 2024 notes
Summary and highlights of the month
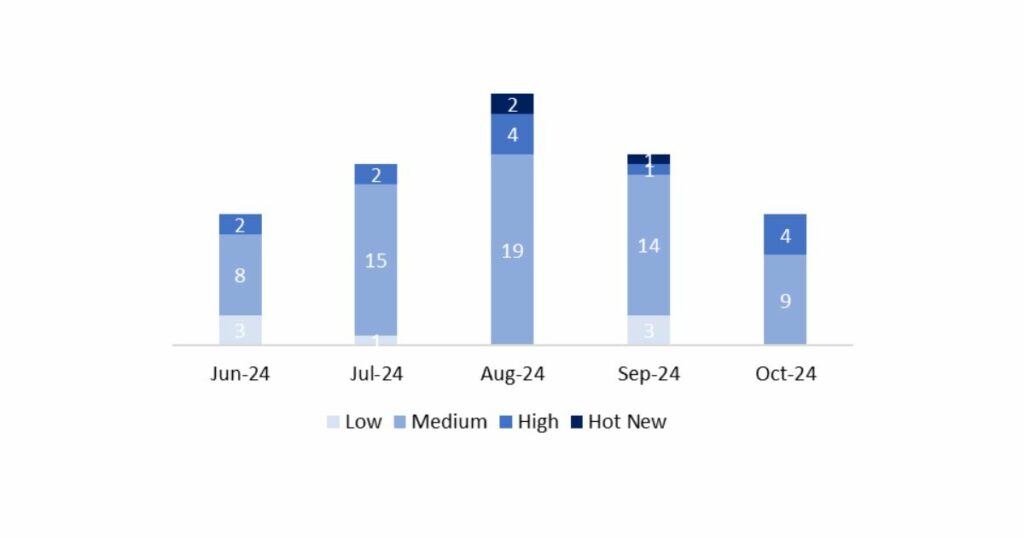
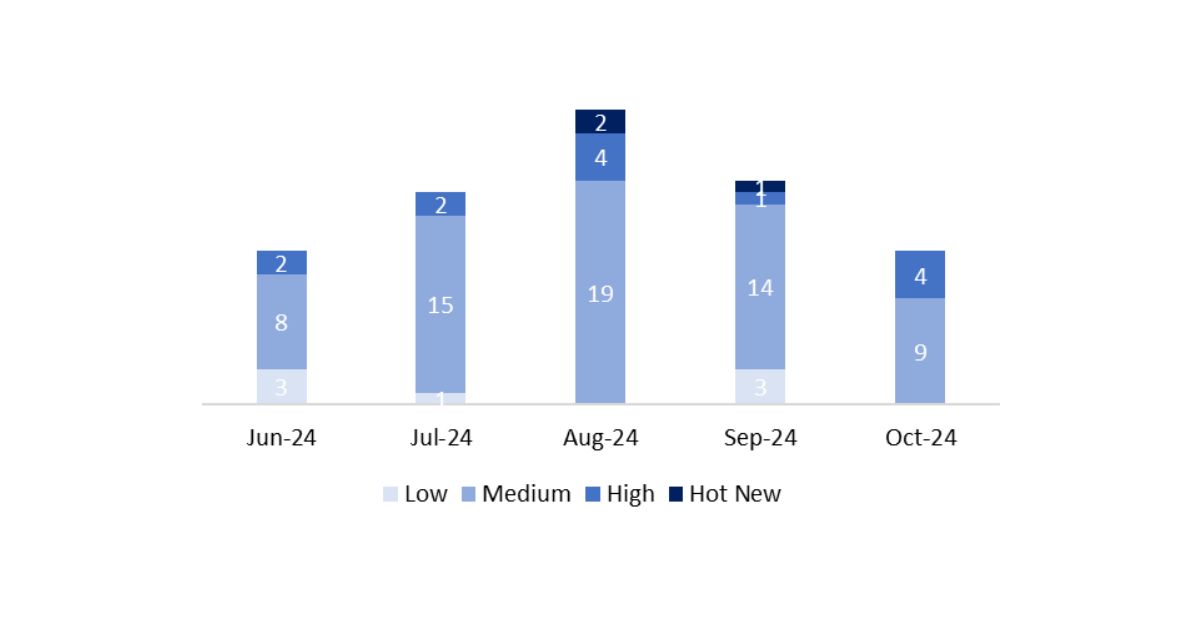
The total number of notes/patches was 13, 6 fewer than last month. This month there were no HotNews, unlike last month, when there was 1. On the other hand, it is worth noting that the number of high-criticality notes has increased compared to last month: 4 this month. As always, we will leave the medium and low notes unreviewed, but we will provide details on a total of 4 notes (all of which have a CVSS of 7 or higher).
We have a total of 13 notes for the entire month (all 13 from Patch Tuesday, 7 new ones and 6 updates).
We will review in detail a total of 4 notes, the high-priority notes for this month, which consist of 2 updates and 2 new notes (those with a CVSS score greater than or equal to 7).
- The most critical note of the month (with a CVSS 9.8) is a note with critical priority related to “Missing Authentication check in SAP BusinessObjects Business Intelligence Platform”.
- The next in criticality (CVSS 8.0) is another high-priority note related to “Multiple vulnerabilities in SAP Enterprise Project Connection”.
- The next in criticality (CVSS 7.7) is a high-priority note related to “Insecure File Operations vulnerability in SAP BusinessObjects Business Intelligence Platform (Web Intelligence)”.
- The next in criticality (CVSS 7.7) is a high-priority note related to “Missing Authorization check in SAP PDCE”.
- The following in criticality (CVSS 6.5and 6.0) are two medium-priority notes related to “Multiple vulnerabilities in SAP Replication Server (FOSS)” and “Information disclosure vulnerability in SAP NetWeaver AS for Java (Destination Service)”.
- This month, the most predominant types are related to “Missing Authorization check in SAP” (3/13 on patch day) and “Information Disclosure vulnerability in SAP” (3/13 on patch day).
In the graph, we can see the classification of the October notes, as well as the evolution and classification over the last 5 previous months (only Sec. Tuesday / Patch Day notes – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
- Update – Missing Authentication check in SAP BusinessObjects Business Intelligence Platform (3479478): In SAP BusinessObjects Business Intelligence Platform, if Single Sign-On (SSO) is enabled in enterprise authentication, an unauthorized attacker can obtain a login token through a REST endpoint, which could compromise the entire system. This severely affects confidentiality, integrity and availability. The issue is fixed in the patches for SBOP BI PLATFORM SERVERS 4.2, 4.3 and 2025 releases. CVSS v3 Base Score: 9,8 / 10 [CVE-2024-41730]
- Multiple vulnerabilities in SAP Enterprise Project Connection (3523541): SAP Enterprise Project Connection uses vulnerable versions of the open-source libraries Spring Framework and Log4j, related to the CVEs: CVE-2024-22259, CVE-2024-38809, CVE-2024-38808, and CVE-2022-23302. The solution is to apply a patch that updates the libraries to safe versions, using Spring framework and reload4j. It is recommended to implement the patch mentioned in the SAP Security Note to resolve these vulnerabilities. CVSS v3 Base Score 8,0 / 10 [CVE-2022-23302].
- Insecure File Operations vulnerability in SAP BusinessObjects Business Intelligence Platform (Web Intelligence) (3478615): SAP BusinessObjects Business Intelligence Platform allows an authenticated user to download files from the server, severely affecting confidentiality. This is due to the lack of restrictions in the personal data provider function. The solution is to apply a patch and create a PersonalFile_AllowList.txt file that specifies the allowed folders for personal data providers. CVSS v3 Base Score 7,7/ 10 [CVE-2024-37179].
- Update – Missing Authorization check in SAP PDCE (348334): PDCE elements do not properly verify authorization for authenticated users, allowing privilege escalation. This allows an attacker to access sensitive information, severely affecting the confidentiality of the application. As a solution, the affected functions have been disabled to restrict access. It is recommended to implement the corresponding support package or follow the remediation instructions in the security note. CVSS v3 Base Score 7,7/ 10 [CVE-2024-39592].
Reference links
Other references, from SAP and Onapsis (october):
SAP Patch Day: October 2024 – Onapsis
Resources affected
- SAP BusinessObjects Business Intelligence Platform, Versions – ENTERPRISE 420, 430, 440
- SAP Enterprise Project Connection, Version – 3.0
- SAP BusinessObjects Business Intelligence Platform (Web Intelligence), Version – ENTERPRISE 420, 430, 2025, ENTERPRISECLIENTTOOLS 420, 430, 2025
- SAP PDCE, Versions – S4CORE 102, 103, S4COREOP 104, 105, 106, 107, 108
- SAP Replication Server, Versions – 16.0.3, 16.0.4
- SAP NetWeaver AS for Java (Destination Service). Versions – 7.50
- SAP Commerce Backoffice, Versions – HY_COM 2205, COM_CLOUD 2211
- SAP NetWeaver Enterprise Portal (KMC), Version – KMC-BC 7.5
- SAP HANA Client, Version – HDB_CLIENT 2.0
- SAP S/4 HANA (Manage Bank Statements), Versions – S4CORE, 102, 103, 104, 105, 106, 107
- SAP NetWeaver BW (BEx Analyzer), Versions – DW4CORE 200, DW4CORE 300, DW4CORE 400, SAP_BW 700, SAP_BW 701, SAP_BW 702, SAP_BW 731, SAP_BW 740, SAP_BW 750, SAP_BW 751, SAP_BW 752, SAP_BW 753, SAP_BW 754, SAP_BW 755, SAP_BW 756, SAP_BW 757, SAP_BW 758
- SAP Student Life Cycle Management (SLcM), Versions – IS-PS-CA 617, 618, 802, 803, 804, 805, 806, 807, 808
- SAP NetWeaver Application Server for ABAP and ABAP Platform. Versions – SAP_BASIS 700, SAP_BASIS 701, SAP_BASIS 702, SAP_BASIS 731, SAP_BASIS 740, SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758