Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
November 2024 notes
Summary and highlights of the month
We have a total of 10 notes for the entire month (the 10 from Patch Tuesday, 8 new and 2 updates).
We will review in detail a total of 2 notes, the high notes of this month, which consist of 1 update and 1 new note (those with a CVSS of 7 or higher).
-
The most critical note of the month (with CVSS 8.8) is a high-priority note related to “Cross-Site Scripting (XSS) vulnerability in SAP Web Dispatcher”.
-
The next in criticality (CVSS 7.7) is an update to the note published in July of this year, related to “Multiple vulnerabilities in SAP Enterprise Project Connection”.
-
This month, the most prevalent type is related to “Missing Authorization check in SAP” (4/10 on Patch Day).
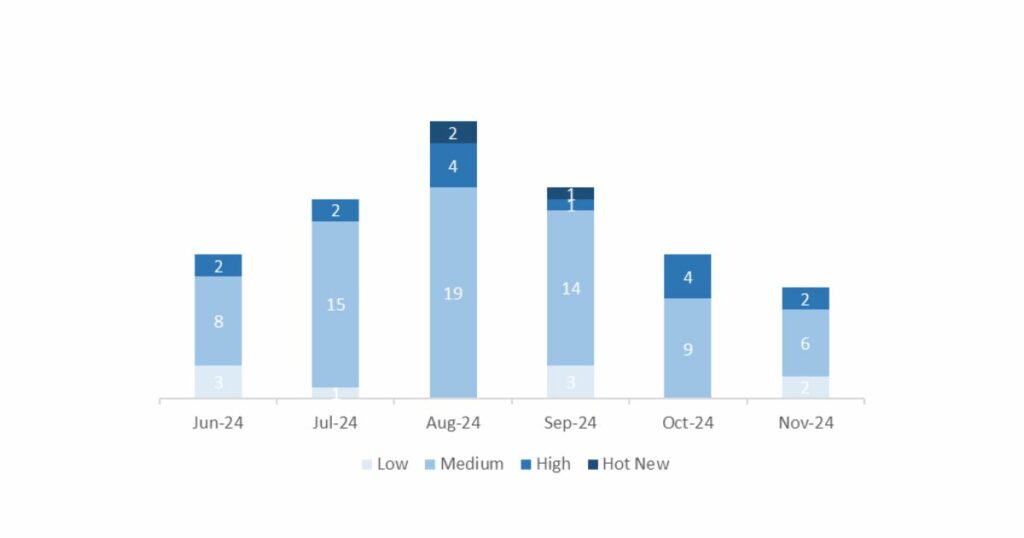
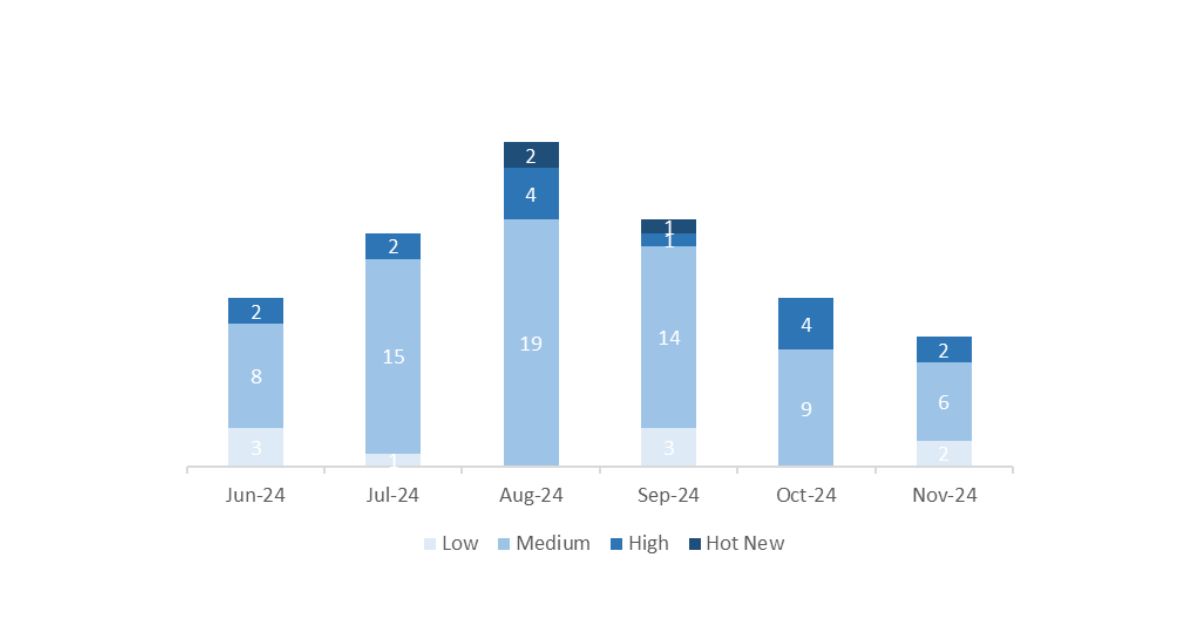
In the chart, we can see the classification of the November notes, along with the evolution and classification of the past 5 months (only notes from Sec. Tuesday / Patch Day – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
- Cross-Site Scripting (XSS) vulnerability in SAP Web Dispatcher(3520281): An unauthenticated attacker can create a malicious link that, when executed in the victim’s browser (XXS) or transmitted to another server (SSRF), gives the attacker the ability to execute arbitrary code on the server, totally compromising confidentiality, integrity and availability. CVSS v3 Base Score 8,8/ 10 [CVE-2024-47590]
- Update – Missing Authorization check in SAP PDCE(3483344): Elements of PDCE does not perform necessary authorization checks for an authenticated user, resulting in escalation of privileges. This allows an attacker to read sensitive information causing high impact on the confidentiality of the application The update contains corrections for SEM-BW 602 to SEM-BW 748 .CVSS v3 Base Score 7,7/ 10 [CVE-2024-39592].
Reference links
Other references, from SAP and Onapsis (november):
SAP Security Patch Day – November 2024
SAP Patch Day: November 2024 – Onapsis
Recursos afectados
Resources affected
- SAP Web Dispatcher, Versions – WEBDISP 7.77, 7.89, 7.93, KERNEL 7.77, 7.89, 7.93, 9.12, 9.13
- SAP PDCE, Version – S4CORE 102, 103, S4COREOP 104, 105, 106, 107, 108
-
SAP NetWeaver AS Java (System Landscape Directory), Versions – LM-SLD 7.5
-
SAP NetWeaver Application Server Java (Logon Application), Versions – SERVERCORE 7.5
-
SAP NetWeaver Application Server for ABAP and ABAP Platform, Versions – KRNL64NUC 7.22, 7.22EXT, KRNL64UC 7.22, 7.22EXT, 7.53, 8.04, KERNEL 7.22, 7.53, 7.54, 7.77, 7.89, 7.93, 8.04, 9.12, 9.13
-
SAP NetWeaver Java (Software Update Manager), Versions – SUM 1.1
-
SAP Cash Management (Cash Operations), Version – S4CORE 103, 104, 105, 106, 107, 108
-
SAP Bank Account Management, Version – 100, 101, 102, 103, 104, 105, 106, 107, 108