Inprosec, through its services such as the SAP Security Assessment, helps its clients to improve the security levels of their SAP systems.
Notas Mayo 2023
Resumen y highlights del Mes
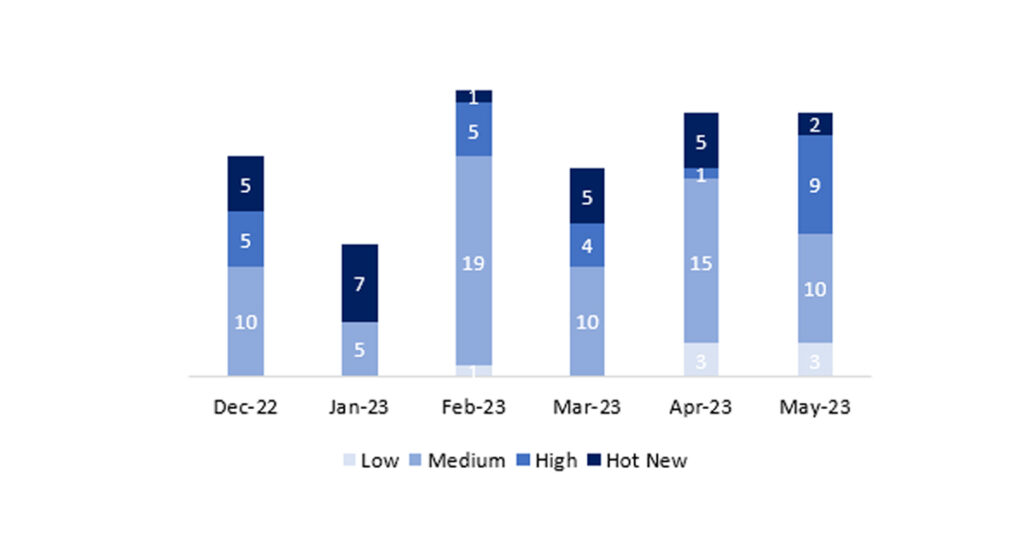
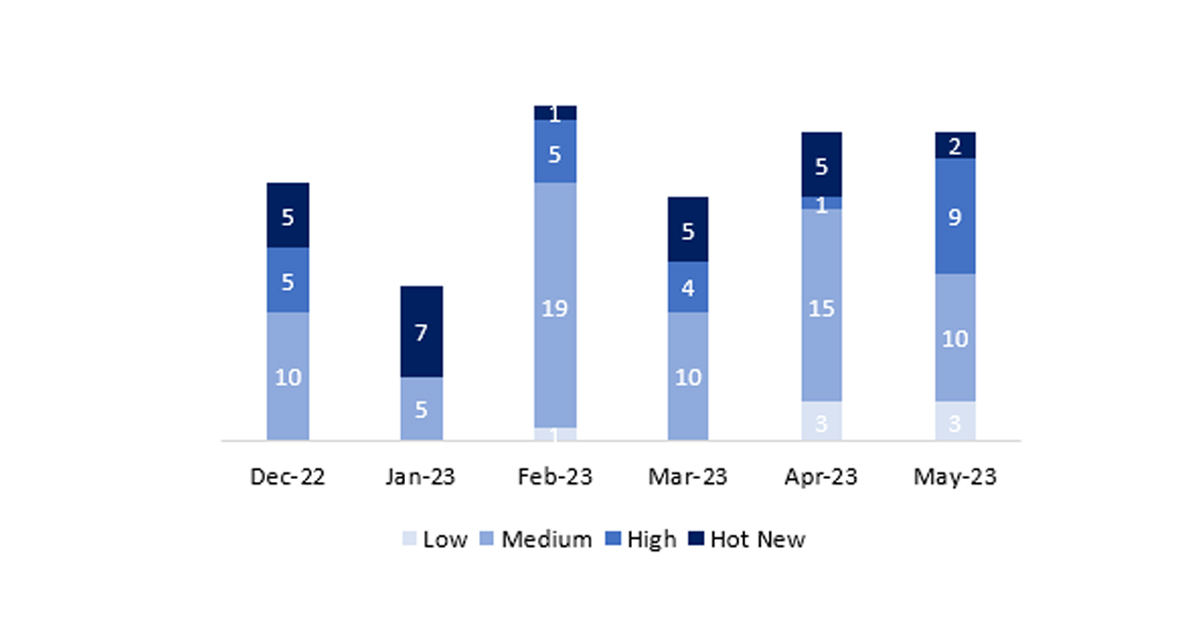
El número total de notas/parches ha sido de 25, 1 más que el mes pasado. El número de Hot News disminuye, pasando de 5 a 3 en este mes. Por otro lado, cabe destacar que el número de notas de criticidad alta aumenta pasando de 1 a 9. Como siempre dejaremos las notas medias y bajas sin revisar en este mes, pero daremos detalle de un total de 12 notas (todas las que tengan un CVSS de 7 o mayor).
Tenemos un total de 25 notas para todo el mes (las 24 del patch Tuesday, 18 nuevas y 6 actualizaciones, son el mismo número de notas que el pasado patch Tuesday).
Revisaremos en detalle 12 del total de 12 notas altas y HotNews, 2 de las 3 HotNews son nuevas y 7 de 9 notas altas serían nuevas (aquellas de CVSS mayor o igual a 7).
- La nota más crítica del mes (con CVSS 10) es una actualización de la nota habitual relacionada con “Google Chromium”.
- Las siguientes notas en criticidad (con CVSS 9,8 y 9,2) son 2 HotNews, una relacionada con “Multiple vulnerabilities associated with Reprise License Manager 14.2” y la otra está relacionada con “Information Disclosure vulnerabilities in SAP BusinessObjects Intelligence Platform”
- Las siguientes notas en criticidad (con CVSS 8,2) son 3 notas altas, la primera relacionada con “Improper access control during application start-up in SAP AS NetWeaver JAVA”, la segunda con “Privilege escalation vulnerability in SAP IBP add-in for Microsoft Excel” y la tercera se trata de una actualización de una nota publicada en agosto de 2022 “Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Monitoring DB)”
- La siguiente nota en criticidad es una nota alta (con CVSS 7,7), se trata de una actualización de una nota publicada en septiembre de 2022 relacionada con “Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (CMC)”
- Las siguientes notas en criticidad (con CVSS 7,5) son 4 notas altas, la primera relacionada con “Memory Corruption vulnerability in SAP PowerDesigner(Proxy)”, la segunda con “DOS in SAP Commerce”, la tercera está relacionada con “Information Disclosure vulnerability in SAP GUI for Windows” y la cuarta está relacionada con “Information Disclosure vulnerability in SAP Commerce (Backoffice)”
- La siguiente nota (con CVSS 7,1) es una nota alta relacionada con “Improper Neutralization of Input in SAPUI5”
- Este mes el tipo más predominante es “Information Disclosure vulnerability” (12/24 en patch day).
En la gráfica (post mayo 2023 de SAP) podemos ver la clasificación de las notas de mayo además de la evolución y clasificación de los últimos 5 meses anteriores (solo las notas del Sec. Tuesday / Patch Day – by SAP):
Detalle completo
El detalle completo de las notas SAP más relevantes es el siguiente (en inglés):
-
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open-source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. The note has been re-released with updated ‘Solution’ and ‘Support Packages & Patches’ information. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Multiple vulnerabilities associated with Reprise License Manager 14.2 component used with SAP 3D Visual Enterprise License Manager (3328495): This security note patches five vulnerabilities in version 14.2 of the Reprise License Manager(RLM) component used with SAP 3D Visual Enterprise License Manager as this component is vulnerable to vulnerabilities related to the web interface. The note contains a workaround. CVSS v3 Base Score: 9,8 / 10 [CVE-2021-44151, CVE-2021-44152, CVE-2021-44153, CVE-2021-44154, CVE-2021-44155].
- Information Disclosure vulnerabilities in SAP BusinessObjects Intelligence Platform (3307833): BusinessObjects Business Intelligence platform allows an authenticated attacker with administrator privileges to get the login token of any logged-in BI user or server over the network without any user interaction. The attacker can impersonate any user on the platform resulting into accessing and modifying data. The attacker can also make the system partially or entirely unavailable. This note includes multiple patches for Information Disclosure vulnerabilities in SAP BusinessObjects Business Intelligence Platform and replaces the patch solutions provided in notes 3217303, 3145769, 3213524, 3213507 and 3233226. CVSS v3 Base Score: 9,1 / 10 [CVE-2023-28762]
- Improper access control during application start-up in SAP AS NetWeaver JAVA (3317453): An unauthenticated attacker can connect to an open interface and make use of an open naming and directory API to instantiate an object that has methods that can be called without authorization or authentication causing a vulnerability that allows reading or changing the state of existing services without any effect on availability. CVSS v3 Base Score: 8,2 / 10 [CVE-2023-30744].
- Privilege escalation vulnerability in SAP IBP add-in for Microsoft Excel (3323415): The installer of SAP IBP, add-in for Microsoft Excel (Excel Add-in) allows an authenticated attacker to add an InstallScript custom action to a Basic MSI or InstallScript MSI project extracts few binaries to a predefined writable folder during installation time. As a result in privilege escalation, an attacker can run code as an administration that could lead to a high impact on the confidentiality, integrity and availability of the system. Only newly started installation are exploitable. CVSS v3 Base Score: 8,2 / 10 [CVE-2023-29080]
- Update – Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Monitoring DB) (3213507): Under certain conditions, an attacker authenticated as a CMS administrator and with high privileges access to the Network, can access BOE Monitoring database to retrieve and modify (non-personal) system data which would otherwise be restricted. Also, a potential attack could be used to leave the scope of the CMS and have impact on the database. The note indicates that it is necessary to implement security note 3307833 for the complete fix as the solution provided by this patch is incomplete. CVSS v3 Base Score: 8,2 / 10 [CVE-2022-31596]
- Update – Information Disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (CMC)( 3217303): Under certain conditions Central Management Console (CMC) allows an attacker to access certain unencrypted sensitive parameters which would otherwise be restricted. The note indicates that it is necessary to implement security note 3307833 for the complete fix as the solution provided by this patch is incomplete. CVSS v3 Base Score: 7,7 / 10 [CVE-2022-39014]
- Memory Corruption vulnerability in SAP PowerDesigner (Proxy) (3300624): In SAP PowerDesigner an attacker can send a crafted request from a remote host to the proxy machine and crash the proxy server due to faulty implementation of memory management causing a memory corruption. This leads to a high impact on availability of the application. Base Score: 7,5 / 10 [CVE-2023-32111]
- Denial of service (DOS) in SAP Commerce (3320145): Due to the fact that SAP Commerce uses XStream, it allows an attacker to prevent legitimate users from accessing a service by terminating the application with a stack overflow error. This has a direct impact on the availability of the system. This vulnerability can affect all SAP Commerce installations that use an outdated Xstream library that is vulnerable to CVE-2022-41966. Base Score: 7,5 / 10
- Information Disclosure vulnerability in SAP GUI for Windows (3320467): SAP GUI for Windows allows an unauthorized attacker to gain NTLM authentication information of a victim by tricking it into clicking a prepared shortcut file. Depending on the authorizations of the victim, the attacker can read and modify potentially sensitive information after successful exploitation. Base Score: 7,5 / 10 [CVE-2023-32113]
- Information Disclosure vulnerability in SAP Commerce (Backoffice) (3321309): Under certain conditions, SAP Commerce Backoffice allows an attacker to access information via a crafted POST request that would otherwise be restricted, impacting the confidentiality of the system. The Backoffice web application in SAP Commerce before version 2211 uses a version of ZK Framework that has vulnerability CVE-2022-36537. Base Score: 7,5 / 10
- Improper Neutralization of Input in SAPUI5 (3326210): Due to improper neutralization of input in SAPUI5, sap.m.FormattedText SAPUI5 control allows injection of untrusted CSS. This blocks user’s interaction with the application. Further, in the absence of URL validation by the application, the vulnerability could lead to the attacker reading or modifying user’s information through phishing attack. Base Score: 7,1 / 10 [CVE-2023-30743].
Enlaces de referencia
Otras referencias, en inglés de SAP y Onapsis (mayo):
SAP Security Patch Day: May 2023 | Onapsis
Recursos afectados
El listado completo de los sistemas/componentes afectados es el siguiente:
- SAP 3D Visual Enterprise License Manager, Version –15
- SAP AS NetWeaver JAVA, Versions -SERVERCORE 7.50, J2EE-FRMW 7.50, CORE-TOOLS 7.50
- SAP BusinessObjects Intelligence Platform, Versions –420, 430
- SAP Commerce (Backoffice), Version–2105, 2205
- SAP Commerce, Versions–2105, 2205, 2211
- SAP GUI for Windows, Versions-7.70, 8,0
- SAP IBP EXCEL ADD-IN, Versions–2211, 2302, 2305
- SAP PowerDesigner (Proxy), Version -16.7
- SAPUI5, Versions-SAP_UI 750, SAP_UI 754, SAP_UI 755, SAP_UI 756, SAP_UI 757, UI_700 20