Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
March 2022 notes
Summary and highlights of the month
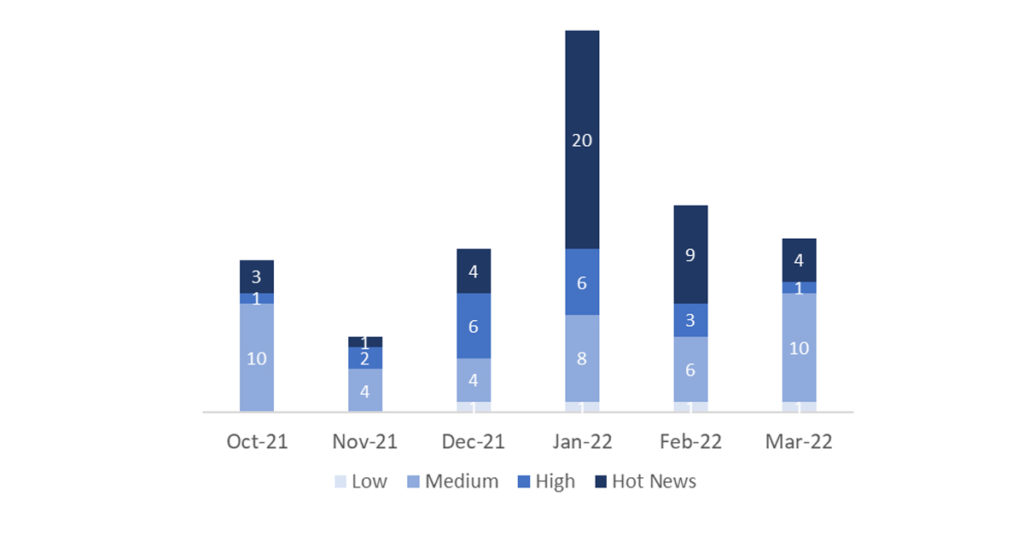
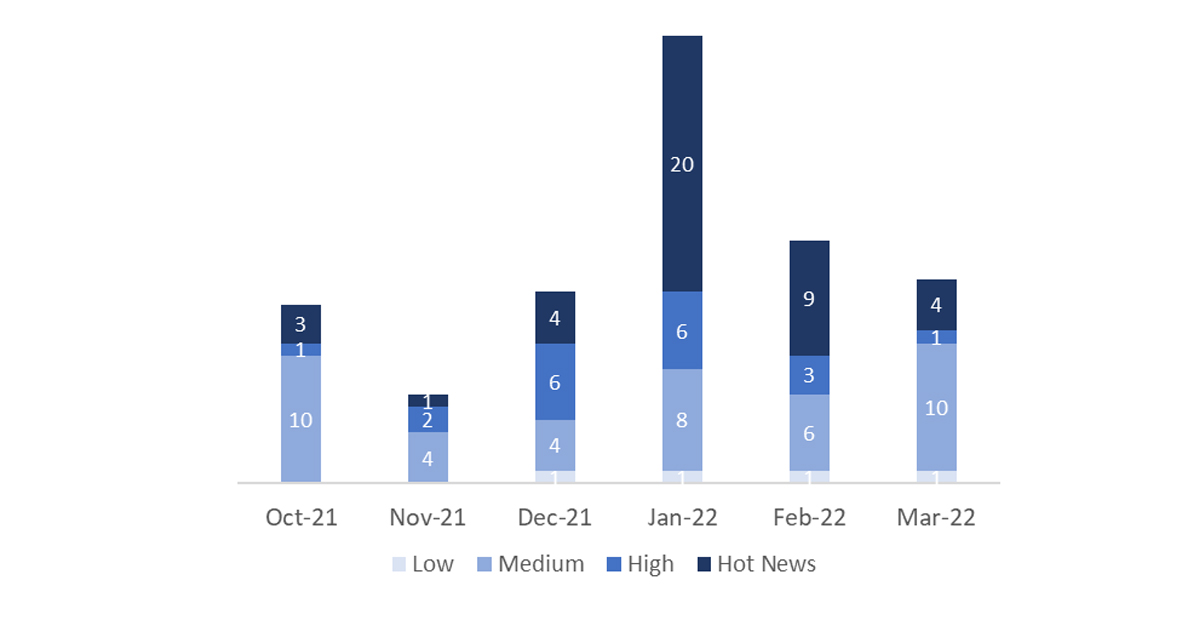
The total number of notes/patches has decreased compared to last month. In addition to this decrease in the total number of notes, the number of Hot News has also decreased, with 9 notes last month compared to 4 in March. On the other hand, it should be noted that the number of high criticality notes decreased from 3 to 1 this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 5 scores (all those with a CVSS of 7 or higher).
We have a total of 17 notes for the whole month, 5 less than last February (16 from Patch Tuesday, 12 new and 4 updates, being 6 less than last month).
We have 4 critical notes (Hot News), 2 new and 2 updates, in this month, which stand out for their high CVVS. We will also review in detail 1 of the total of 1 high notes (those with CVSS greater than or equal to 7), which this month is a new note.
- The most critical notes of the month (with CVSS 10) are 3. On the one hand the central note that affects Apache Log4j 2 component and the note of “Remote Code Execution vulnerability” that affects Apache Log4j 2 component used in SAP Work Manager. On the other hand, the third note with this CVSS affects SAP NetWeaver, SAP Content Server and SAP Web Dispatcher.
- Next in criticality (CVSS 9.3) is a “Missing Authentication check” note that affects SAP Focused Run.
- From there, we locate the high criticality note (CVSS 8.1) of “Information Disclosure vulnerability” affecting SAP S/4HANA. The rest (12) are medium and low level, and we will not see them in detail, although it is worth noting that there is more than one that affects SAP NetWeaver.
- This month the most predominant note types are “Cross-Site Scripting (XSS)” (4/17 and 4/16 on patch day), “Missing Authorization Check” (3/17 and 3/16 on patch day) and “Information Disclosure” (3/17 and 3/16 on patch day).
In the graph (post March 2022 from SAP) we can see the ranking of the March notes in addition to the evolution and ranking of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The full details of the most relevant notes are as follows:
- Update – Central Security Note for Remote Code Execution vulnerability associated with Apache Log4j 2 component (3131047): It is the central SAP Security Note for the Log4j vulnerability and was updated with information about the new note #3154684. CVSS v3 Base Score: 10 / 10 (CVE-2021-44228).
- Remote Code Execution vulnerability associated with Apache Log4j 2 component used in SAP Work Manager (3154684): It affects the SAP Work Manager and SAP Inventory application. Both applications run on SAP Mobile Platform (SMP) and only on-premise installations of the SMP are affected. The note recommends upgrading to SAP Work Manager 6.6.1 and/or SAP Inventory Manager 4.4.1 since these application versions were built with the new library versions of the log4j library. As a workaround, a direct replacement of the vulnerable log4j library on the SMP server can be implemented. Due to the fact that SAP Work Manager versions prior to 6.4 do not use log4j libraries, they are not affected by the Log4j vulnerabilities. CVSS v3 Base Score: 10 / 10 (CVE-2021-44228).
- Update – Request smuggling and request concatenation in SAP NetWeaver, SAP Content Server and SAP Web Dispatcher (3123396): Update that was initially released on February’s Patch Day. It contains some additional information, including a reference to the Knowledge Base Article #3148968 which contains an FAQ about the patch. CVSS v3 Base Score: 10 / 10 (CVE-2022-22536).
- Missing Authentication check in SAP Focused Run (Simple Diagnostics Agent 1/0) (3145987): It patches a Missing Authentication vulnerability in the SAP Simple Diagnostics Agent. This agent is installed and deployed as an add-on to the SAP Host Agent and it is a prerequisite for using the Simple System Integration (SSI) in SAP Focused Run. CVSS v3 Base Score: 9.3 / 10 (CVE-2022-24396).
- Cross-Site Scripting (XSS) vulnerability in SAP Fiori launchpad (3149805): It patches a Cross-Site Scripting (XSS) vulnerability in SAP Fiori launchpad. Our research team detected that SAP Fiori launchpad allows an unauthenticated attacker to manipulate the SAP-theme URL parameter — and inject HTML code — and create a link over the network for a user to click on. Once the link is clicked, successful exploitation allows the attacker to hijack user privileges that can be used to exfiltrate data and craft a CSRF attack to manipulate data. This can limit the application’s confidentiality and pose risks to its integrity, as well as increase the likelihood of it being completely compromised. CVSS v3 Base Score: 8.1 / 10 (CVE-2022-26101).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for March:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-marzo-2022
Other references, from SAP and Onapsis (March):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
Resources affected
- Fiori Launchpad, versiones: 754, 755 y 756;
- SAP Business Objects Business Intelligence Platform, versiones 420 y 430;
- SAP Content Server, versión 7.53;
- SAP Financial Consolidation, versión 10.1;
- SAP Focused Run, versiones: 200 y 300;
- SAP Inventory Manager, versiones: 4.3 y 4.4;
- SAP NetWeaver and ABAP Platform, versiones: KERNEL 7.22, 8.04, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87, KRNL64UC 8.04, 7.22, 7.22EXT, 7.49, 7.53, KRNL64NUC 7.22, 7.22EXT y 7.4;
- SAP NetWeaver:
-
- Application Server for ABAP, versiones: 700, 701, 702 y 731;
- AS JAVA (Portal Basis), versión 7.50;
- Enterprise Portal, versiones: 7.10, 7.11, 7.20, 7.30, 7.31, 7.40 y 7.50;
- SAP Web Dispatcher, versiones: 7.49, 7.53, 7.77, 7.81, 7.85, 7.22EXT, 7.86 y 7.87;
- SAP Work Manager, versiones: 6.4, 6.5 y 6.6;
- SAPCAR, versión 7.22;
- SAP-JEE, versión 6.40;
- SAP-JEECOR, versiones: 6.40, 7.00 y 7.01;
- SAPS/4HANA (Hoja de datos de proveedores y búsqueda de empresas para socios comerciales, proveedores y clientes), versiones: 104, 105 y 106;
- SERVERCORE, versiones: 7.10, 7.11, 7.20, 7.30 y 7.31;
- Simple Diagnostics Agent, versiones: =>1.0 a < 1.58.
- Simple Diagnostics Agent;