Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
June 2022 notes
Summary and highlights of the month
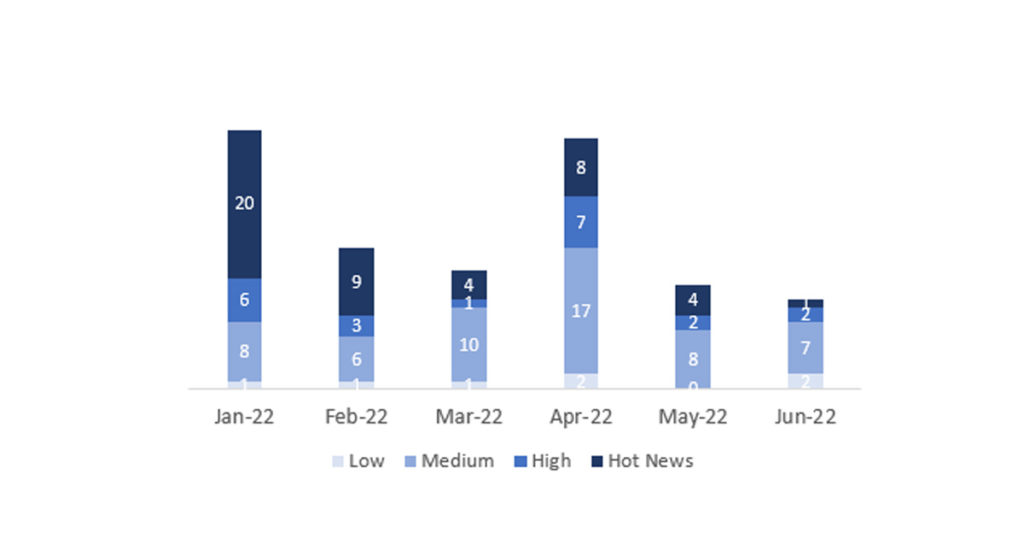
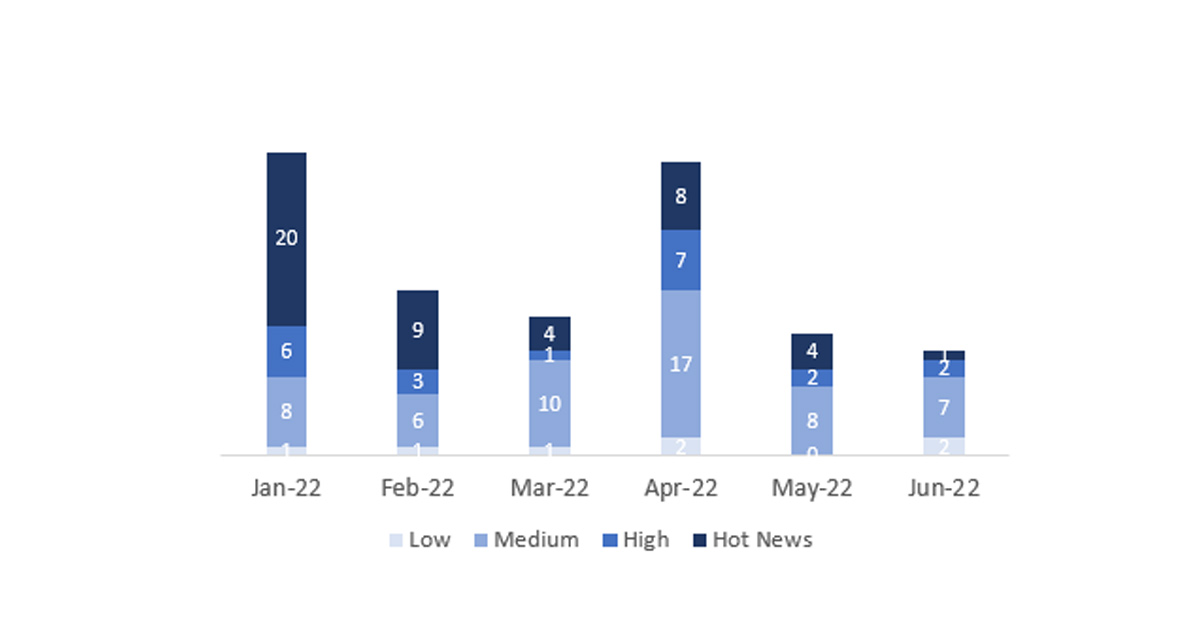
The total number of notes/patches has remained the same as last month. In addition to this equality in the total number of notes, the number of Hot News decreased, with 4 notes last month compared to the only one in June. On the other hand, it should be noted that the number of high criticality notes increased from 2 to 3 this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 4 scores (all those with a CVSS of 7 or higher).
We have a total of 17 notes for the whole month, exactly the same as last May (12 from Patch Tuesday, 10 new ones and 2 updates, being the same as last month).
We have only one critical note (Hot News), being this one an update, in this month, that stands out for its high CVVS. We will also review in detail 3 of the total of 3 new high notes (those with CVSS greater than or equal to 7).
- The most critical note of the month (with CVSS 10) is the usual note related to “Google Chromium”.
- The next in criticality (CVSS 8.6, 8.2 and 7.8) are three high scores, one related to “Improper Access Control of SAProuter for SAP NetWeaver and ABAP Platform”, another one related to “Improper Access Control check in SAP Netweaver AS JAVA”, and the last one related to “Potential privilege escalation in SAP PowerDesigner Proxy 16.7”.
- The rest (9) are medium and low level, and we will not see them in detail, although it should be noted that there is more than one that affects SAP NetWeaver.
This month the most predominant types are “Privilege Escalation vulnerability” (4/17 and 4/12 in patch day) and “Missing Authorization Check” (3/17 and 1/12 in patch day).
In the graph (post June 2022 from SAP) we can see the classification of the June notes in addition to the evolution and classification of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open source project Chromium. The note priority is based on the highest CVSS score of all the vulnerabilities fixed in the latest browser release. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. The solution will be to update the SAP Business Client patch to the newest one, which contains the most current stable major release of the Chromium browser control, which passed the SAP internal quality measurements of SAP Business Client. CVSS v3 Base Score: 10 / 10 (Multiple CVE´s).
- Improper Access Control of SAProuter for SAP NetWeaver and ABAP Platform (3158375): Depending on the configuration of the route permission table in file «saprouttab», it is possible for an unauthenticated attacker to execute SAProuter administration commands in SAP NetWeaver and ABAP Platform, from a remote client, for example stopping the SAProuter, that could highly impact systems availability. SAProuter is designed to restrict administration commands to clients that run on the same host as SAProuter. Administration commands should not be allowed from remote clients. The correction is contained in SAProuter, it is delivered in the following components on SAP Service Marketplace: SAPROUTER versions 7.53 and 7.22, and in the Package saprouter.sar in the SAP KERNEL versions 7.85, 7.81 and 7.77. Nevertheless, it is recommended to use SAPROUTER version 7.53. Keep in mind that the correction will be delivered in future versions of SP stack kernel SAPEXE.SAR, but it will not be available in SAPEXE.SAR in all versions when this SAP note is published. CVSS v3 Base Score: 8,6 / 10 (CVE-2022-27668).
- Improper Access Control check in SAP NetWeaver basicadmin and adminadapter services (3147498): Improper Access Control is detected in SAP NetWeaver AS Java, basicadmin and adminadapter services remote objects are not properly protected. As a result, some administrative functionalities are exposed to public access, which means the Availability could be impacted. This correction discontinues public access to basicadmin and adminadapter services remote objects by introducing required authentication and authorization protection. To solve the issue, please apply the corrective measure according to the «Support Packages & Patches» section of the note.. CVSS v3 Base Score: 8,2 / 10.
- Potential privilege escalation in SAP PowerDesigner Proxy 16.7 (3197005): SAP PowerDesigner Proxy, allows an attacker with low privileges and has local access, with the ability to work around system’s root disk access restrictions to Write/Create a program file on system disk root path, which could then be executed with elevated privileges of the application during application start up or reboot, potentially compromising Confidentiality, Integrity and Availability of the system. This issue when «SAP PowerDesigner Proxy 16.7» SP05 up to including PL2 is installed. To solve the issue, the action would be to upgrade the «SAP PowerDesigner Proxy 16.7» to version SP05 PL03 or higher. CVSS v3 Base Score: 7.8 / 10 (CVE-2022-31590).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for June:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-junio-2022
Other references, from SAP and Onapsis (June):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
Resources affected
- SAP 3D Visual Enterprise Viewer, versión 9.0;
- SAP Adaptive Server Enterprise (ASE), versiones -KERNEL 7.22, 7.49, 7.53, KRNL64NUC 7.22, 7.22EXT, 7.49, KRNL64UC 7.22, 7.22EXT, 7.49, 7.53;
- SAP Business Client, versión 6.5;
- SAP ERP, localization for CEEcountries, versiones -C-CEE110_600, 110_602, 110_603, 110_604, 110_700;
- SAP Financials, versiones -SAP_FIN 618, 720;
- SAP Host Agent, versión – 7.22;
- SAP NetWeaver Application Server for ABAP and ABAP Platform, versiones -700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755, 756, 787, 788;
- SAP NetWeaver AS ABAP, AS Java, and HANA Database, versiones -KERNEL 7.22, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87, 7.88, KRNL64NUC 7.22, 7.22EXT, 7.49, KRNL64UC 7.22, 7.22EXT, 7.49, 7.53;
- SAP NetWeaver and ABAP Platform, versiones -KERNEL 7.22, 7.49, 7.53, 7.77, 7.81, 7.85, 7.86, 7.87, 7.88, 8.04, KRNL64NUC .22, 7.22EXT, 7.49, KRNL64UC 7.22, 7.22EXT, 7.49, 7.53, 8.04, SAP_ROUTER 7.53, 7.22;
- SAP NetWeaver Developer Studio (NWDS), versión -7.50;
- SAP NetWeaver Development Infrastructure (Design Time Repository), versiones -7.30, 7.31, 7.40, 7.50;
- SAP PowerDesigner Proxy 16.7;
- SAP S/4Hana Core, versiones -S4CORE 100, 101, 102, 103, 104, 105, 106, 107, 108;