Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
July 2022 notes
Summary and highlights of the month
The total number of notes/patches was 27, 10 more than last month, despite the higher number of notes, the number of Hot News decreased, being 1 the one we found last month, with none existing in July. On the other hand, it should be noted that the number of high criticality notes increased from 3 to 5 this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 5 scores (all those with a CVSS of 7 or higher).
We have a total of 27 notes for the whole month, 10 notes more than last June (The 23 from Patch Tuesday, 20 new and 3 updates, 11 notes more than last month).
We will review in detail 5 of the total 5 new high scores (those with CVSS greater than or equal to 7).
- The highest score of the month (with CVSS 8.3) is the “Information disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Central management console)”.
- The next in criticality (CVSS 7.6, 7.5, 7.4 and 7.4) are four high scores, one for “Information Disclosure vulnerability in SAP Business One”, one related to “Missing Authentication check in SAP Business One (License serviceAPI)”, one related to “Code Injection vulnerability in SAP Business One” and the last one is an update related to “Improper Access Control check in SAP NetWeaver basicadmin and adminadapter services”.
- The rest (22) are of medium and low level, and we will not see them in detail, although it should be noted that there is more than one that affects SAP NetWeaver.
- This month the most predominant types are “Cross-Site Scripting (XSS) vulnerability” (7/27 and 7/23 in patch day) and “Missing Authorization Check” (5/27 and 3/23 in patch day).
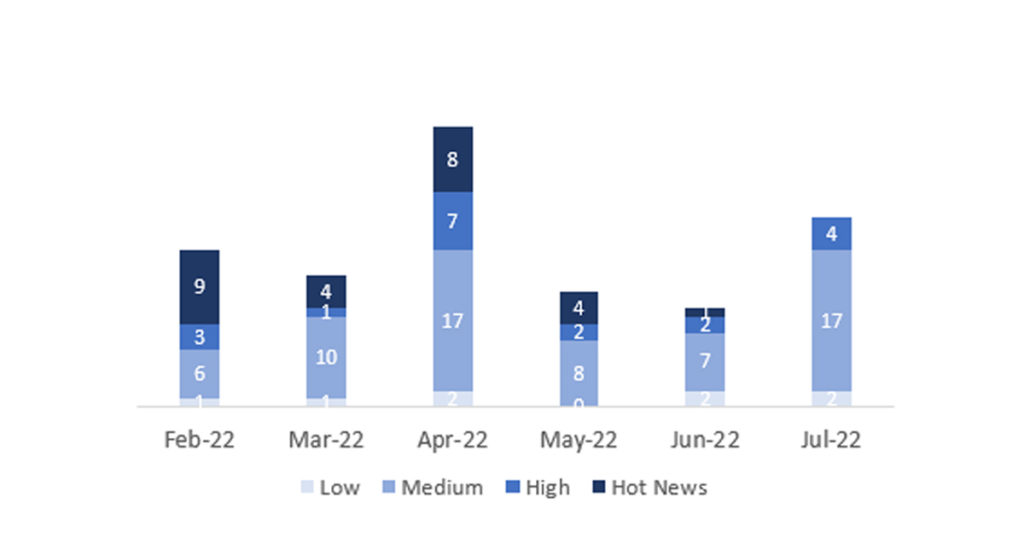
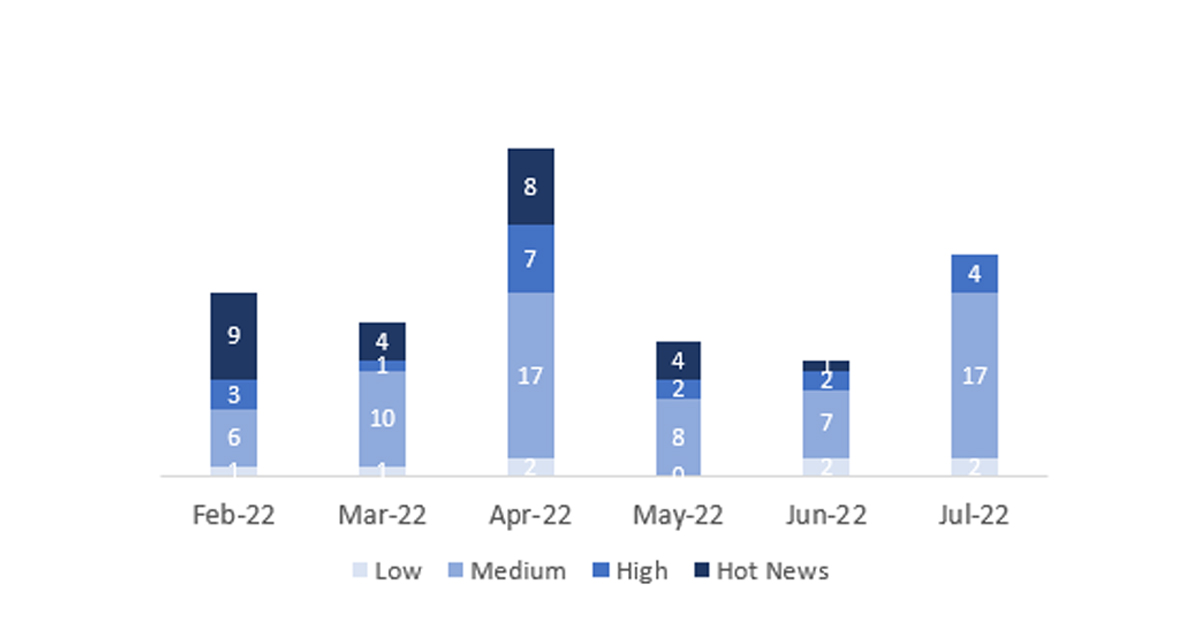
In the graph (post July 2022 from SAP) we can see the ranking of the July notes in addition to the evolution and ranking of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
- Information disclosure vulnerability in SAP BusinessObjects Business Intelligence Platform (Central management console) (3221288): SAP BusinessObjects CMC allows an unauthenticated attacker to retrieve token information over the network which would otherwise be restricted. This can be achieved only when a legitimate user accesses the application and a local compromise occurs, like sniffing or social engineering. On successful exploitation, the attacker can completely compromise the application. Taken care of hiding token.This is fixed in all available code lines. 4.2 SP09 Patch 9, 4.3 SP01 and above releases. CVSS v3 Base Score: 8,3 / 10 (CVE-2022-35228).
- Information Disclosure vulnerability in SAP Business One (3212997): Under special integration scenario of SAP Business one and SAP HANA, an attacker can exploit HANA cockpit’s data volume to gain access to highly sensitive information. The note offers a workaround, use Explicit Password instead of XPAth Password in FTP Adapter. For other parts, customer need upgrade B1. CVSS v3 Base Score: 7,6 / 10 (CVE-2022-32249).
- Missing Authentication check in SAP Business One (License service API) (3157613): Due to missing authentication check, SAP Business one allows an unauthenticated attacker to send malicious http requests over the network. On successful exploitation, an attacker can break the whole application making it inaccessible.To solve this issue, customers should upgrade to SAP Business One 10.0 FP2202. For SAP customers who cannot apply the corresponding patch immediately, the note refers to knowledge base article 3189816 for a temporary workaround describing how to prevent end users from accessing the license API. CVSS v3 Base Score: 7,5 / 10.
- Code Injection vulnerability in SAP Business One (31911012): SAP BusinessObjects CMC allows an unauthenticated attacker to retrieve token information over the network which would otherwise be restricted. This can be achieved only when a legitimate user accesses the application and a local compromise occurs, like sniffing or social engineering. On successful exploitation, the attacker can completely compromise the application. CVSS v3 Base Score: 7.4 / 10 (CVE-2022-31593).
- Update – Improper Access Control check in SAP NetWeaver basicadmin and adminadapter services (3147498): Improper Access Control is detected in SAP NetWeaver AS Java, basicadmin and adminadapter services remote objects are not properly protected. As a result, some administrative functionalities are exposed to public access, which means the Availability could be impacted. This correction discontinues public access to basicadmin and adminadapter services remote objects by introducing required authentication and authorization protection. To solve the issue, please apply the corrective measure according to the “Support Packages & Patches” section of the note. CVSS v3 Base Score: 7.4 / 10
Reference links
Other references, from SAP and Onapsis (July):
https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
https://onapsis.com/blog/sap-security-patch-day-july-2022-three-applications-focus
Resources affected
- SAP Adaptive Server Enterprise (ASE),Version -KERNEL 7.22, 7.49, 7.53, KRNL64NUC 7.22, 7.22EXT, 7.49, KRNL64UC 7.22, 7.22EXT, 7.49, 7.53
- SAP Business Objects, Version -420
- SAP Business One License serviceAPI, Version -10.0
- SAP Business One, Version -10.0
- SAP BusinessObjects Business Intelligence Platform (Central management console),Versions -420, 430
- SAP BusinessObjects Business Intelligence Platform (LCM),Versions -420, 430
- SAP BusinessObjects Business Intelligence Platform (Visual Difference Application),Versions -420, 430
- SAP BusinessObjects Business Intelligence Platform 4.x,Versions -420, 430
- SAP BusinessObjects BW Publisher Service, Versions -420,430
- SAP Enterprise Extension Defense Forces & Public Security (EA-DFPS),Versions -605, 606, 616,617,618, 802, 803, 804, 805, 806
- SAP Enterprise Portal, Versions -7.10, 7.11, 7.20, 7.30, 7.31, 7.40, 7.50
- SAP NetWeaver Application Server for ABAP and ABAP Platform,Versions -700, 701, 702, 710, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755, 756, 787, 788
- SAP NetWeaver Enterprise Portal (WPC), Versions -7.30, 7.31, 7.40, 7.50
- SAP NetWeaver Enterprise Portal, Versions -7.10, 7.11, 7.20, 7.30, 7.31, 7.40, 7.5
- SAP3D Visual Enterprise Viewer, Version -9.0
- SAPS/4HANA(Supplier Factsheet and Enterprise Search for Business Partner, Supplier and Customer),Versions -104, 105, 106
- SAPS/4HANA, Versions -101, 102, 103, 104, 105, 106
- SAPS/4HANA, Versions -S4CORE 101, 102, 103, 104, 105, 106, SAPSCORE 127