Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
February 2025 Notes
Summary and Highlights of the Month
This month the total number of notes/patches was 21, 7 more than the previous month. There were no HotNews this month, whereas in January there were 2. Regarding the number of high-severity notes, they increased by 3 compared to the previous month, going from 3 to 6. The medium and low notes will not be reviewed, so we will provide details for a total of 6 notes (all those with a CVSS of 7 or higher).
We have a total of 21 notes for the entire month (19 of these notes are new, while two are updates of notes published in previous months).
We will review in detail a total of 6 notes, all of high severity:
- The most critical note of the month (CVSS 8.8) is a High; it is an update of the note published in February last year, related to “Cross Site Scripting vulnerability in NetWeaver AS Java (User Admin Application)”.
- The next in severity (CVSS 8.7) is a note related to “Improper Authorization in SAP BusinessObjects Business Intelligence platform (Central Management Console)”.
- The next in severity (CVSS 8.6) is a note related to “Path traversal vulnerability in SAP Supplier Relationship Management (Master Data Management Catalog)”.
- This month the most predominant type is related to “Cross Site Scripting vulnerability in NetWeaver AS Java (User Admin Application)” (2/21 on patch day).
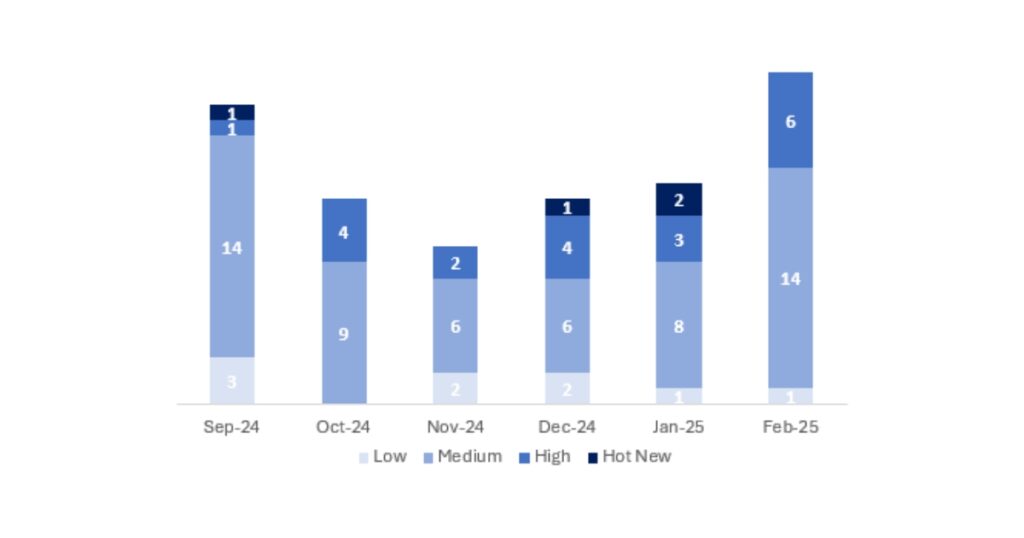
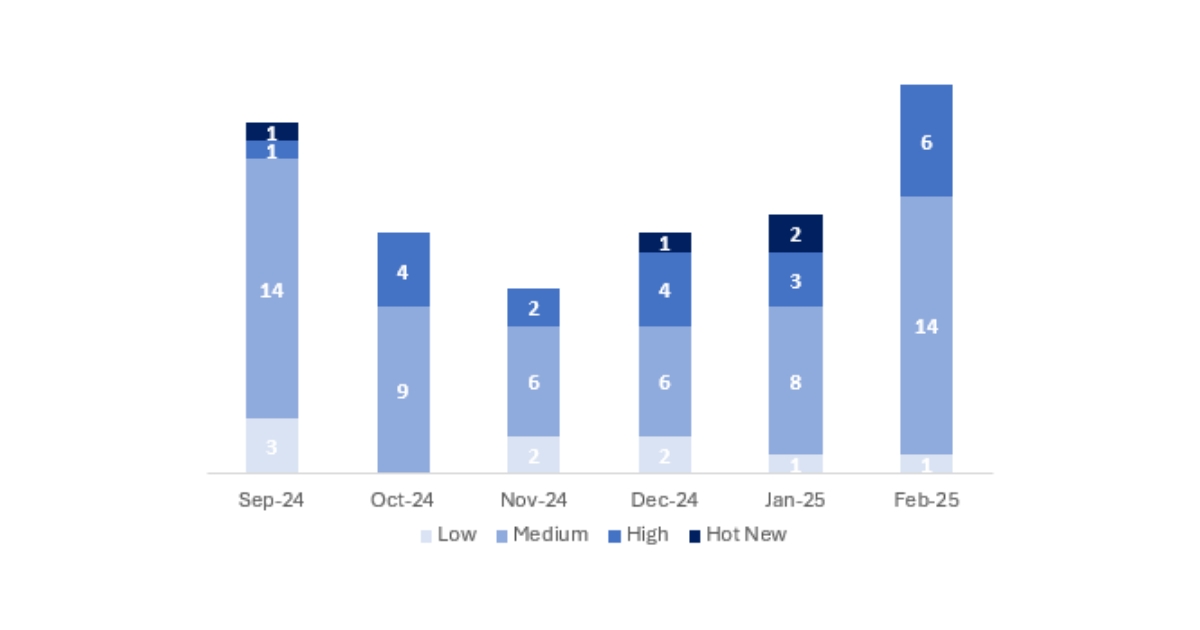
In the graph we can see the classification of the notes from February, as well as the evolution and classification of the last 5 previous months (only the notes from Sec. Tuesday / Patch Day – by SAP).
Full details
The complete detail of the most relevant notes is as follows:
- Cross Site Scripting vulnerability in NetWeaver AS Java (User Admin Application) (3417627): The User Admin application of SAP NetWeaver AS for Java – version 7.50, insufficiently validates and improperly encodes the incoming URL parameters before including them into the redirect URL. This results in Cross-Site Scripting (XSS) vulnerability, leading to a high impact on confidentiality and mild impact on integrity and availability. This error can be solved by applying the correction according to the “Validity” and “Support Packages & Patches” sections of this note. Note: To avoid incompatibilities on the system, check SAP Note 1974464 – Information on SCA Dependency Analysis for Java download objects. CVSS v3 Base Score 8,8/ 10 [CVE-2024-22126]
- Improper Authorization in SAP BusinessObjects Business Intelligence platform (Central Management Console) (3525794): Under specific conditions, the Central Management Console of the SAP BusinessObjects Business Intelligence platform allows an attacker with admin rights to generate or retrieve a secret passphrase, enabling them to impersonate any user in the system. This results in a high impact on confidentiality and integrity, with no impact on availability. To solve the issue, please implement the patches listed in “Support Packages & Patches” section of this Security Note.For Business Intelligence Platform maintenance schedule and strategy see the Knowledge Base Article 2144559 in References section. Besides, after upgrading to the patches in this Security Note, configure the system with HTTPS as described in the product documentation referenced in this note, such as the Securing the BI Platform section of the Business Intelligence Platform Administrator Guide (subsection Trusted Authentication). It is highly recommended (but not mandatory) to configure the system with CORBA SSL as explained in the same section Configuring backend servers for SSL. For implementation steps and further details see SAP KBA 3559381. CVSS v3 Base Score 8,7/ 10 [CVE-2025-0064]
- Path traversal vulnerability in SAP Supplier Relationship Management (Master Data Management Catalog) (3567551): SAP Supplier Relationship Management (Master Data Management Catalog) allows an unauthenticated attacker to use a publicly available servlet to download an arbitrary file over the network without any user interaction. This can reveal highly sensitive information with no impact to integrity or availability. This issue exists due to the programmatic error of insufficient sanitization of input path. To solve the issue, please implement the patches listed in “Support Packages & Patches” section of this Security Note. CVSS v3 Base Score 8,6/ 10 [CVE-2025-25243]
- Authentication bypass via authorization code injection in SAP Approuter (3567974): The SAP Approuter Node.js package version v16.7.1 and before is vulnerable to Authentication bypass. When trading an authorization code an attacker can steal the session of the victim by injecting malicious payload causing High impact on confidentiality and integrity of the application. To fix the error, please upgrade to SAP Approuter node.js package to 16.7.2 or higher. This fix ensures that the url protocol in the login callback url is a valid one. CVSS v3 Base Score 8,1/ 10 [CVE-2025-24876]
- Multiple vulnerabilities in SAP Enterprise Project Connection (3567172): SAP Enterprise Project Connection uses versions of Spring Framework open-source libraries which could be vulnerable to CVEs mentioned in the “Other terms” section of this SAP Security Note. To solve this issue, implement the patch referenced by this SAP Security Note. By implementing this patch, above mentioned CVEs are fixed by upgrading to the relevant Spring framework libraries. CVSS v3 Base Score 7,5/ 10 [CVE-2024-38819]
- Open Redirect Vulnerability in SAP HANA extended application services, advanced model (User Account and Authentication Services) (3563929): The User Account and Authentication service (UAA) for SAP HANA extended application services, advanced model (SAP HANA XS advanced model) allows an unauthenticated attacker to craft a malicious link, that, when clicked by a victim, redirects the browser to a malicious site due to insufficient redirect URL validation. On successful exploitation attacker can cause limited impact on confidentiality, integrity, and availability of the system. To fix the error, please implement the Support Packages and Patches referenced by this SAP Note. Validation of redirect URLs is applied in UAA for SAP HANA XS advanced model. The fix is available since SAP HANA XSA version 1.3.3. CVSS v3 Base Score 7,1/ 10 [CVE-2025-24868]
Reference links
Other references, from SAP and Onapsis (february):
SAP Security Patch Day – February 2025
SAP Patch Day: February 2025 – Onapsis
Resources affected
- SAP NetWeaver AS Java (User Admin Application), Version – 7.50
- SAP BusinessObjects Business Intelligence platform (Central Management Console), Versions – ENTERPRISE 430, 2025
- SAP Supplier Relationship Management (Master Data Management Catalog), Version – SRM_MDM_CAT 7.52
- SAP Enterprise Project Connection, Version – 3.0
- SAP HANA extended application services, advanced model (User Account and Authentication Services), Version – SAP_EXTENDED_APP_SERVICES 1
- SAP Commerce, Versions – HY_COM 2205, COM_CLOUD 2211
- SAP GUI for Windows, Version – BC-FES-GUI 8.00
- SAP Fiori Apps Reference Library (My Overtime Requests), Version – GBX01HR5 605
- SAP NetWeaver and ABAP Platform (SDCCN), Versions – ST-PI 2008_1_700, ST-PI 2008_1_710, ST-PI 740
- SAP NetWeaver Server ABAP, Versions – SAP_BASIS 700, SAP_BASIS 701, SAP_BASIS 702, SAP_BASIS 731, SAP_BASIS 740, SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758
- SAP NetWeaver AS Java for Deploy Service, Version – ENGINEAPI 7.50, SERVERCORE 7.50
- SAP NetWeaver Application Server Java, Version – WD-RUNTIME 7.50
- SAP ABAP Platform (ABAP Build Framework), Versions – SAP_BASIS 750, SAP_BASIS 751, SAP_BASIS 752, SAP_BASIS 753, SAP_BASIS 754, SAP_BASIS 755, SAP_BASIS 756, SAP_BASIS 757, SAP_BASIS 758
- SAP Fiori for SAP ERP, Version – SAP_GWFND 740, 750, 751, 752, 753, 754, 755, 756, 757, 758