Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
February 2021 notes
Summary and highlights of the month
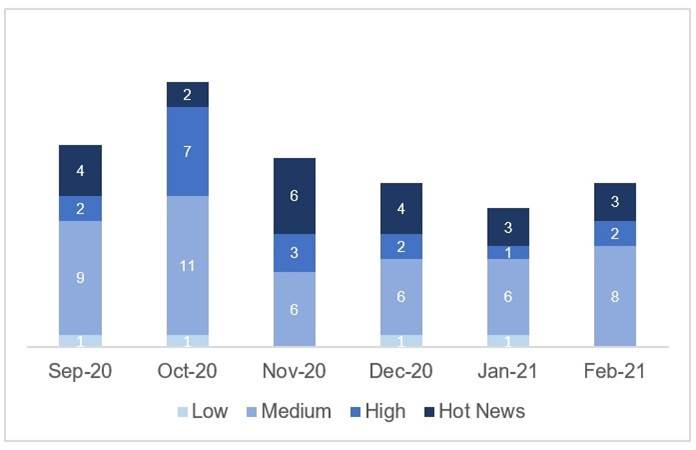
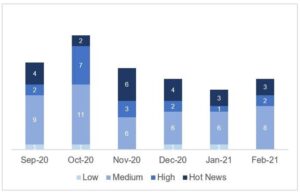
The total number of notes/patches has increased compared to last month. Despite this increase in the total number of notes, the number of Hot News also decreased, from 5 last month to 3 in February. On the other hand, it is worth noting that the number of high criticality notes remains the same, being 2 both last month and this month. As usual, we will leave the medium and low scores unchecked this month, but we will give details of a total of 5 scores (all those with a CVSS of 7 or higher).
We have a total of 20 notes for the whole month, 1 more than last January (13 from Patch Tuesday, 7 new and 6 updates, being 4 less than last month).
We have one new Hot News, being the total of 3 in this month that stand out for their high CVVS, one of them the recurring update for the SAP Business Client with Chromium. In addition we will review in detail 2 of the total of 2 high notes (those with CVSS greater than or equal to 7), both new notes.
- The most critical note of the month (with CVSS 10) is the recurring update of “Browser Control Chromium Delivered with SAP Business Client (2622660)”.
- The next 2 criticality notes (CVSS 9.9) are a new note and an update of a previous note, the first one affects SAP Commerce due to a remote code execution vulnerability, and the second one occurs due to multiple vulnerabilities in SAP Business Warehouse (Database Interface).
- From there, we located 2 notes of high criticality (high priority) being the most relevant with a CVSS of 7.6 an update related to the lack of authorization checks affecting SAP NetWeaver AS ABAP and SAP S4 HANA. The rest (15) are medium and low level, and we will not look at them in detail.
- This month the most predominant types are “Reverse Tabnabbing” (5/20 and 2/13 in patch day), “Missing Authorization Check” (3/20 and 3/13 in patch day). and “Clickjacking” (3/20 and 1/13 in patch day).
In the graph (post February 2021 from SAP) we can see the ranking of the February notes in addition to the evolution and ranking of the last 5 previous months (only the notes of Sec. Tuesday / Patch Day – by SAP):
Full details
The full details of the most relevant notes are as follows:
- Update – Security updates for the browser control Google Chromium delivered with SAP Business Client (2622660): This security note addresses multiple vulnerabilities in the 3rd party web browser control Chromium, which can be used within SAP Business Client. This note will be modified periodically based on web browser updates by the open-source project Chromium. From SAP Business Client 6.5 PL5 and above you can use the browser control Chromium for displaying HTML content within SAP Business Client. As this full browser control is delivered and can be installed with SAP Business Client, security corrections for this browser control are shipped with SAP Business Client patches. If the SAP Business Client release is not updated to the latest patch level, displaying web pages in SAP Business Client via this open-source browser control might lead to different vulnerabilities like memory corruption, Information Disclosure and the like. Some well-known impact of those vulnerabilities are: system information disclosure or system crash in worst cases; vulnerabilities might have direct impact on confidentiality, integrity and availability of a system; information gathered can be used to craft further attacks, possibly with more severe consequences. CVSS v3 Base Score: 10 / 10.
- Remote Code Execution vulnerability in SAP Commerce (3014121): SAP Commerce Backoffice application enables certain users with required privileges to edit drools rules. An authenticated attacker with this privilege will be able to inject malicious code in the drools rules which, when executed, leads to Remote Code Execution vulnerability enabling the attacker to compromise the underlying host enabling him to impair confidentiality, integrity and availability of the application. This patch addresses this remote code execution vulnerability by improving the default permissions that govern change access to scripting facilities of DroolsRules and by disabling script editing facilities for DroolsRules in the SAP Commerce Backoffice. CVSS v3 Base Score: 9.9 / 10 (CVE-2021-21477).
- Update – Multiple vulnerabilities in SAP Business Warehouse (Database Interface) (2986980): It patches a SQL Injection vulnerability, tagged with CVSS score of 9.9, and a Missing Authorization Check vulnerability, tagged with CVSS score of 6.5. Both vulnerabilities were found in the Database Interface of SAP BW. An improper sanitization of provided SQL commands allowed an attacker to execute arbitrary SQL commands on the database which could lead to a full compromise of the affected system. The Missing Authorization Check vulnerability that was fixed with note #2986980 could lead to an escalation of privileges allowing an attacker to read out any database table. SAP has solved the issue by just disabling the function module. Attention: This will cause a dump in any application that calls this function module, so, it is highly recommended to check your custom code before applying the patch. If the function module is still in use, it is also strongly recommended to think about an alternative “as it must not be used anymore” and to implement the patch. Based on that statement, there is a high chance that the dangerous function module will be removed anyway with one of the next updates. CVSS v3 Base Score: 9.9 / 10 (Multiple CVE IDs).
- Update – Missing Authorization check in SAP NetWeaver AS ABAP and SAP S4 HANA (SAP Landscape Transformation) (2993132): Fixes an issue in the SLT component of SAP NetWeaver AS ABAP and S/4 HANA systems. A missing explicit authorization check-in a remote enabled function module allowed a high privileged user to execute functions to which access should be restricted. CVSS v3 Base Score: 7.6 / 10 (CVE-2020-26832).
- Update – Denial of service (DOS) in SAP NetWeaver AS ABAP and ABAP Platform (3000306): It patches a scenario in SAP NetWeaver AS and ABAP Platform that could lead to a Denial-of-Service experience for the users. Starting the demo examples that are embedded in ABAP Server’s and ABAP Platform’s ABAP Keyword Documentation via the web version allows an unauthenticated attacker to prevent legitimate users from accessing a service, either by crashing or flooding the service. The provided fix prevents the demo examples from being started in parallel. CVSS v3 Base Score: 7.5 / 10 (CVE-2021-21446).
Reference links
Reference links of the CERT of the INCIBE in relation to the publication of the notes for January:
https://www.incibe-cert.es/alerta-temprana/avisos-seguridad/actualizacion-seguridad-sap-febrero-2021
Other references, from SAP and Onapsis (February):
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=568460543
https://onapsis.com/blog/sap-security-patch-day-february-2021-critical-patch-released-sap-commerce
Resources affected
- SAP Business Client, versión 6.5;
- SAP Business Objects Business Intelligence platform (CMC and BI Launchpad), versiones 410, 420 y 430;
- SAP Business Warehouse, versiones 700, 711, 730, 731, 740, 750, 751, 752, 753, 754, 755 y 782;
- SAP Commerce, versiones 1808, 1811, 1905, 2005 y 2011;
- SAP HANA Database, versiones 1.0 y 2.0;
- SAP NetWeaver:
- AS ABAP, versiones 740, 750, 751, 752, 753, 754 y 755;
- AS ABAP (SAP Landscape Transformation – DMIS), versiones 2011_1_620, 2011_1_640, 2011_1_700, 2011_1_710, 2011_1_730, 2011_1_731 y 2011_1_752, 2020;
- Master Data Management, versiones 710 y 710.750;
- Process Integration (Java Proxy Runtime), versiones 7.10, 7.11, 7.30, 7.31, 7.40 y 7.50;
- SAP Software Provisioning Manager 1.0 (SAP NetWeaver Master Data Management Server 7.1), versión 1.0;
- SAP S4 HANA (SAP Landscape Transformation), versiones 101, 102, 103, 104 y 105
- SAP UI, versiones 7.5, 7.51, 7.52, 7.53 y 7.54;
- SAP UI 700, versión 2.0
- SAP UI5, versiones 1.38.49, 1.52.49, 1.60.34, 1.71.31, 1.78.18, 1.84.5, 1.85.4 y 1.86.1
- SAP Web Dynpro ABAP;