Inprosec through its services, such as the SAP Security Assessment, helps its customers to improve the security levels of their SAP systems.
December 2024 Notes
Summary and Highlights of the Month
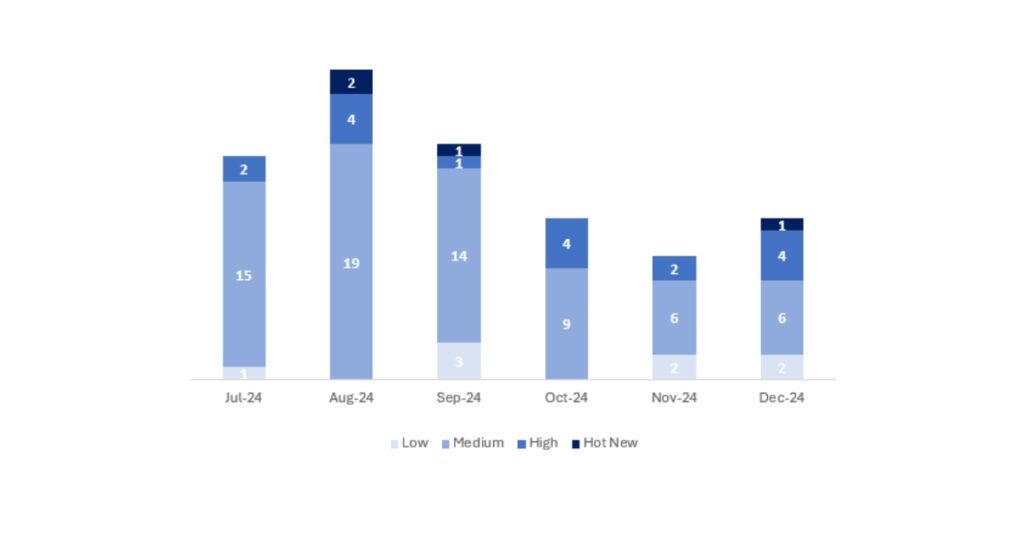
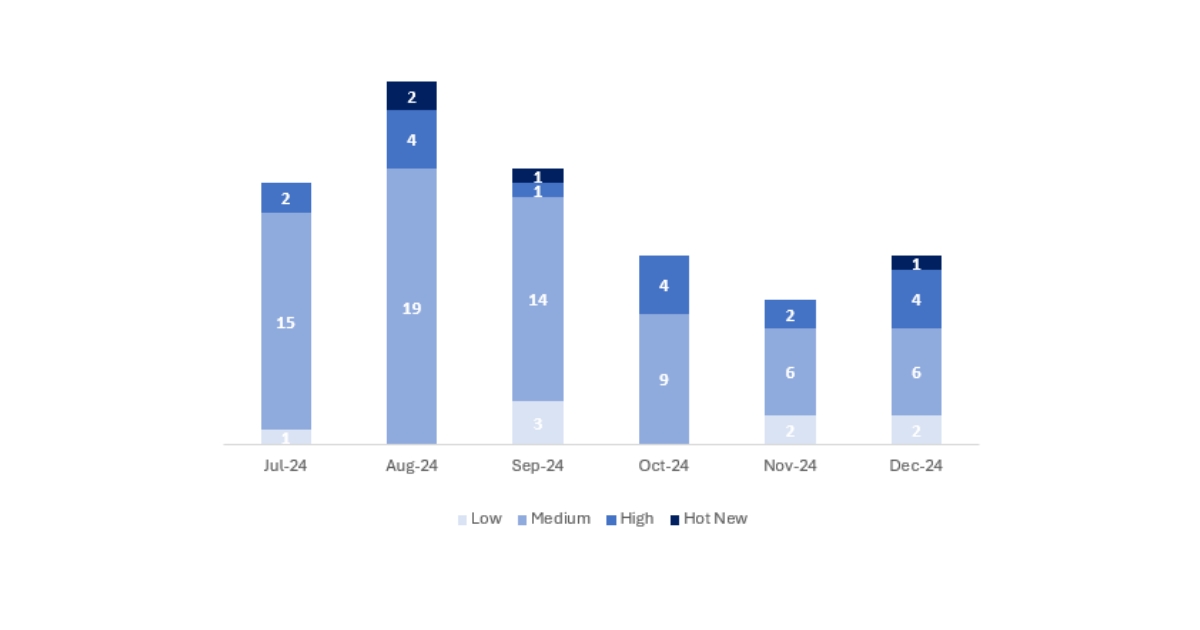
This month, the total number of notes/patches was 13, 3 more than last month. There was one HotNews this month, the first since September. Regarding the number of high-criticality notes, these increased by 2 this month, from 2 in November to 4. Medium and low-criticality notes will not be reviewed, so we will provide details on a total of 5 notes (all those with a CVSS of 7 or higher).
We have a total of 13 notes for the entire month (all 13 from Patch Tuesday: 10 new and 3 updates).
We will review in detail a total of 5 notes, the 4 high-criticality notes and the HotNews, which consist of 2 updates and 3 new notes (those with a CVSS greater than or equal to 7).
- The most critical note of the month (with CVSS 9.1) is a HotNews related to “Multiple vulnerabilities in SAP NetWeaver AS for JAVA (Adobe Document Services)”.
- The next in criticality (CVSS 8.8) is an update to the note published in November of this year, related to “Cross-Site Scripting (XSS) vulnerability in SAP Web Dispatcher”.
- The next in criticality (CVSS 8.5) is a note related to “Information Disclosure vulnerability through Remote Function Call (RFC) in SAP NetWeaver Application Server ABAP”.
- The next in criticality (CVSS 7.5) is an update to the note published in November of this year, related to “NULL Pointer Dereference vulnerability in SAP NetWeaver Application Server for ABAP and ABAP Platform”.
- The next in criticality (CVSS 7.2) is a note related to “Server-Side Request Forgery in SAP NetWeaver Administrator (System Overview)”.
- This month, the most prevalent type of vulnerability is related to “Information Disclosure vulnerability” (3/13 on Patch Day).
In the chart, we can see the classification of December notes, as well as the evolution and classification of the past 5 months (only the notes from Security Tuesday / Patch Day – by SAP):
Full details
The complete detail of the most relevant notes is as follows:
- Multiple vulnerabilities in SAP NetWeaver AS for JAVA (Adobe Document Services) (3536965): Adobe Document Service allows an attacker with administrator privileges to send a crafted request from a vulnerable web application. It is usually used to target internal systems behind firewalls that are normally inaccessible to an attacker from the external network, resulting in a Server-Side Request Forgery vulnerability. On successful exploitation, the attacker can read or modify any file and/or make the entire system unavailable. CVSS v3 Base Score 9,1/ 10 [CVE-2024-47578]
- Update – Cross-Site Scripting (XSS) vulnerability in SAP Web Dispatcher (3520281): An unauthenticated attacker can create a malicious link which they can make publicly available. When an authenticated victim clicks on this malicious link, input data will be used by the web site page generation to create content which when executed in the victim’s browser (XXS) or transmitted to another server (SSRF) gives the attacker the ability to execute arbitrary code on the server fully compromising confidentiality, integrity and availability. Note contains 3 Workarounds. CVSS v3 Base Score 8,8/ 10 [CVE-2024-47590]
- Information Disclosure vulnerability through Remote Function Call (RFC) in SAP NetWeaver Application Server ABAP (3469791): In certain conditions, SAP NetWeaver Application Server ABAP allows an authenticated attacker to craft a Remote Function Call (RFC) request to restricted destinations, which can be used to expose credentials for a remote service. These credentials can then be further exploited to completely compromise the remote service, potentially resulting in a significant impact on the confidentiality, integrity, and availability of the application. CVSS v3 Base Score 8,5/ 10 [CVE-2024-54198]
- Update – NULL Pointer Dereference vulnerability in SAP NetWeaver Application Server for ABAP and ABAP Platform (3504390): SAP NetWeaver Application Server for ABAP and ABAP Platform allows an unauthenticated attacker to send a maliciously crafted http request which could cause a null pointer dereference in the kernel. This dereference will result in the system crashing and rebooting, causing the system to be temporarily unavailable. There is no impact on Confidentiality or Integrity. CVSS v3 Base Score 7,5/ 10 [CVE-2024-47586]
- Server-Side Request Forgery in SAP NetWeaver Administrator (System Overview) (3542543): SAP NetWeaver Administrator(System Overview) allows an authenticated attacker to enumerate accessible HTTP endpoints in the internal network by specially crafting HTTP requests. On successful exploitation this can result in Server-Side Request Forgery (SSRF) which could have a low impact on integrity and confidentiality of data. It has no impact on availability of the application. CVSS v3 Base Score 7,2/ 10 [CVE-2024-54197]
Reference links
Other references, from SAP and Onapsis (december):
SAP Security Patch Day – December 2024
SAP Patch Day: December 2024 – Onapsis
Resources affected
- SAP BusinessObjects Business Intelligence platform, Versions – ENTERPRISE 430, 2025
- SAP Commerce Cloud, Versions – HY_COM 2205, COM_CLOUD 2211
- SAP HCM, Version – S4HCMGXX 101
- SAP NetWeaver Administrator (System Overview), Version – LM-CORE 7.50
- SAP NetWeaver Application Server for ABAP and ABAP Platform, Versions – KRNL64NUC 7.22, 7.22EXT, KRNL64UC 7.22, 7.22EXT, 7.53, 8.04, KERNEL 7.22, 7.53, 7.54, 7.77, 7.89, 7.93, 8.04, 9.12, 9.13
- SAP NetWeaver Application Server for ABAP and ABAP Platform, Versions – SAP_BASIS 740, SAP_BASIS 750
- SAP NetWeaver AS for JAVA (Adobe Document Services), Versions – ADSSSAP 7.50
- SAP NetWeaver AS JAVA, Version – LM-CORE 7.50
- SAP Product Lifecycle Costing, Version – PLC_CLIENT 4
- SAP Web Dispatcher, Versions – WEBDISP 7.77, 7.89, 7.93, KERNEL 7.77, 7.89, 7.93, 9.12, 9.13