Today, we resume our tipical post “SAP Security Updates”. This post is about SAP Security Update during the fourth quarter of 2018. Soon we will post SAP Security Notes of 2019.
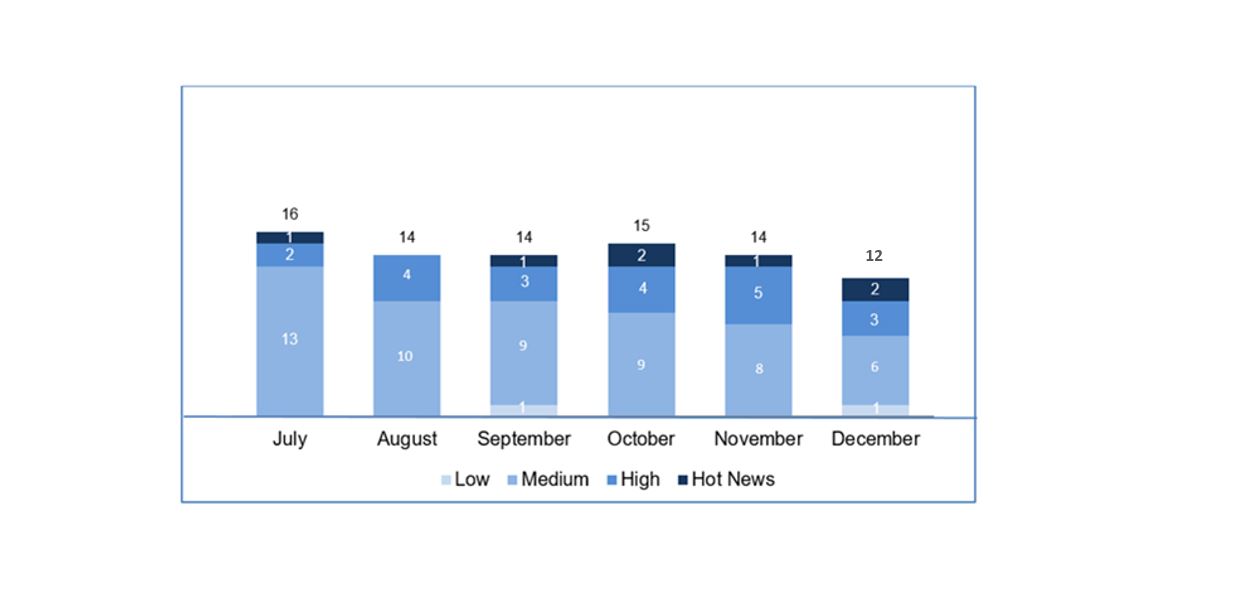
We had 5 hot news in the last quarter of 2018. For this reason, we are going to explain 16 notes.
We highlight:
- The most critical vulnerability of the quarter: SAP HANA Streaming Analytics that would allow an attacker the remote execution of a code with the same permissions as the service that executes them. CVSS of 9.9.
- The first critical note for “SAP Business Objects BI Suite” for more tan 6 years. CVSS of 9.8.
- And the classic “SAP Business Client”, with six updates during 2018. CVSS of 9.8.
In the graph, we can see the evolution of the notes during the fourth quarter of 2018 and during the fourth quarter of 2017:
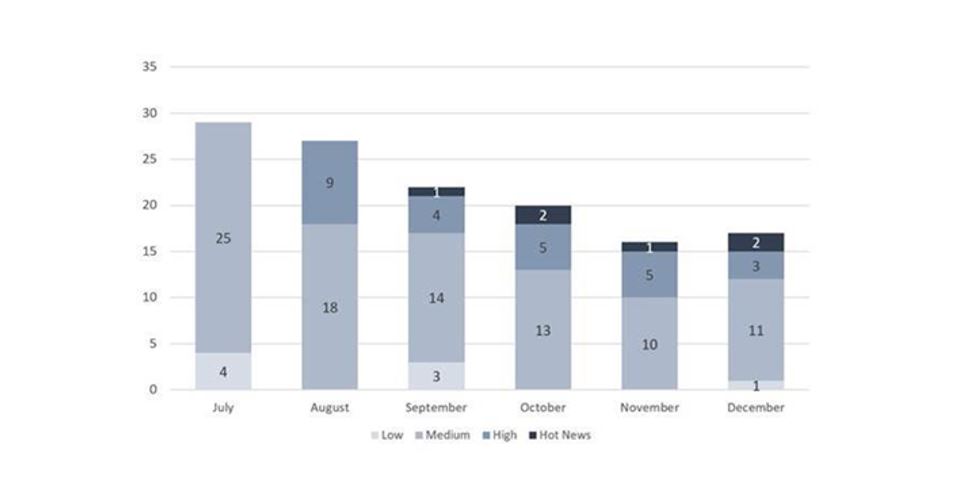
In the following graph, we can see the same evolution but including the monthly notes:
All the details of the most revelant notes below:
- data, debugging information, etc.) that will help to learn about a system and plan other attacks. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 9.8 / 10
- SAP Business Client has a security vulnerability (2622660): This note bundles multiple vulnerabilities. The bugs concern vulnerabilities in web browser controls that are used to display pages in SAP Business Client 6.5 PL5. Web browser controls are programmable building blocks that software developers use to embed web pages in their applications. Depending on the vulnerability, attackers can exploit a Memory corruption vulnerability for injecting specially crafted code into a working memory which will be executed by the vulnerable application. This can lead to taking complete control of an application, denial of service, command execution and other attacks. This fact has a negative influence on business processes and business reputation as a result. Install this SAP Security Note to prevent the risks. Updated in October and December 2018 (“If this note has been already implemented, then there is no action required.” Manual steps only have usability impact and no security implications). CVSS v3 Base Score: 9.8 / 10
- Gardener has a Missing network isolation vulnerability (2699726): Following the Gardener architecture, the Kubernetes apiserver of a Gardener managed shoot cluster resides in the corresponding seed cluster. Due to missing network isolation a shoot’s apiserver can access services/endpoints in the private network of its corresponding seed cluster. Combined with other minor Kubernetes security issues, the missing network isolation theoretically can lead to compromise other shoot or seed clusters in the Gardener context. The issue is rated high due to the high impact of a potential exploitation in the Gardener context. In the Gardener context, missing network isolation can enable an attacker who is admin in a shoot cluster to compromise the corresponding seed cluster or other shoot clusters which are controlled by this seed cluster. Install this SAP Security Note to prevent the risks. Updated in October and November 2018. CVSS Base Score: 8.5 / 10
- SAP Plant Connectivity (PCo) has a Denial of service (DOS) vulnerability (2674215): An attacker can use Denial of service vulnerability for terminating a process of vulnerable component. For this time nobody can use this service, this fact negatively influences on a business processes, system downtime and business reputation as result. Install this SAP Security Note to prevent the risks. CVSS Base Score: 8.2 / 10
- Leveraging Privileges by Customer Transaction Code (2392860 – Re-release): UPDATE – No action is required if this note was already installed after its initial release in February 2017. It fixes the possible use of a reserved transaction code included in a standard SAP role. Exploitation requires a malicious user to use that code in a development system and let that change be transported to the production system. CVSS Base Score: 8.0 / 10
- Missing XML Validation vulnerability in SAP HANA, Extended Application Services classic model (2681207 – Re-release): UPDATE – The reason for the re-release is not the patch itself, which has no changes, but involves a technical description of the note. In the solution section, SAP re-named the previously called ‘workarounds’ to ‘measures to reduce the attack surface’ which mostly consists of a further explanation of possible protection measures that could be present on OData software packages running in HANA’s Extended Application Services classic model. CVSS Base Score: 7.5 / 10
- Denial of Service(DoS) vulnerability in SAPFoundation / database (2696962): This note affects users or developers of the SAP Cloud Platform SDK for iOS due to a vulnerability in the widely used SQLite database which is prone to local Denial of Service. It can be solved both by installing the appropriate patch and following some simple rules for coding the mobile software detailed in the security note. CVSS Base Score: – (not available yet) / 10
- SAP HANA Streaming Analytics has a Security vulnerability in Spring Framework (2681280): An attacker can use a Remote command execution vulnerability for unauthorized execution of commands remotely. Executed commands will run with a same privileges of a service that executed a command. An attacker can access to arbitrary files and directories located in a SAP server file system including application source code, configuration and critical system files. It allows obtaining critical technical and business-related information stored in a vulnerable SAP system. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 9.9 / 10
- SAP Fiori Client has multiple vulnerabilities (DoS, HTML Injection, Missing Authorization Check) (2691126): An attacker can use multiple vulnerabilities and exploit one of the listed or mix them together. An attacker can use a Denial of service vulnerability to terminate a process of vulnerable component, and nobody would use this service. Missing authorization check vulnerability can be used for accessing a service without authorization procedures and for employing service functionality with restricted access that can lead to information disclosure or attacks like privilege escalation. Cross-site scripting vulnerability allows injecting a malicious script into a page. Reflected XSS feature refers to tricking a user who would follow a malicious link. In case of stored XSS, malicious script is injected and permanently stored in a page body, so that user would be attacked without performing any actions. The malicious script can access critical information that are stored by browser (including all cookies, session tokens, etc.) and used for interacting with a site. An attacker can gain access to user’s session and see all business-critical information or even get control over it. XSS can be used for unauthorized modifying of displayed site content. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 8.6 / 10
- Zip Slip in SAP Disclosure Management (2701410): This vulnerability consists of a fail in the location where the files are written when decompressed. It is a widespread vulnerability because it is originated in many commonly used libraries. This vulnerability can be exploited when a malicious archive is processed by a vulnerable decompressing extraction code. With it, an attacker may delete or overwrite data, target remote files he can execute or read the content of arbitrary files. The patch prevents further uploads of specially crafted compressed files. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 8.0 / 10
- Web Intelligence Richclient 3 Tiers Mode has a Denial of service (DOS) vulnerability (2657670): An attacker can use a Denial of service vulnerability for terminating a process of a vulnerable component, and nobody would use this service. This fact negatively influences business processes, system downtime and business reputation as a result. Install this SAP Security Note to prevent the risks. CVSS Base Score: 7.7 / 10
- Leveraging privileges by customer transaction code (2693083): In some SAP standard roles, a transaction code reserved for customer is used. By implementing such transaction code a malicious user may execute unauthorized transaction functionality. That transaction code can be abused by someone with development privileges and having the possibility to get it transported to a production system. Install this SAP Security Note to prevent the risks. CVSS Base Score: 7.6 / 10
- SAP Hybris Commerce storefronts has a Cross-Site Scripting vulnerability (2711425): An attacker can use Cross-site scripting vulnerability for injecting a malicious script into a page. Reflected XSS feature is necessity of tricking a user from an attackers’ side – he must make user to use specially crafted link. Speaking about stored XSS, malicious script is injected and permanently stored in a page body, this way user is attacked without performing any actions. The malicious script can access to all cookies, session tokens and other critical information stored by browser and used for interaction with a site. An attacker can gain access to user’s session and learn business-critical information, in some cases it is possible to get control over this information. Also XSS can be used for unauthorized modifying of displayed site content. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 9.3 / 10
- Missing Authorization check in SAP Customizing Tools (2698996): An attacker can use the lack of authorization checks to perform an escalation of privileges. SAP Customizing Tools do not perform necessary authorization checks for an authenticated user, resulting in escalation of privileges. Some well-known impacts of Missing Authorization check in this case are the abuse of functionality restricted to a particular user group; or the reading, modification or deletion of restricted data. Install this SAP Security Note to prevent the risks. CVSS v3 Base Score: 8.3 / 10
- SAP Java keystore service has Implementation flaw vulnerability (2658279): Depending on the problem, an implementation flaw can cause unpredictable behaviour of a system, troubles with stability and safety. Patches solve configuration errors, add new functionality and increase system stability. Install this SAP Security Note to prevent the risks. CVSS Base Score: 7.4 / 10
- SAP NetWeaver AS Java has XML external entity (XXE) vulnerability (2642680): SAP NetWeaver AS Java has XML external entity (XXE) vulnerability (CVSS Base Score: 7.1 CVE- 2018-2485) An attacker can use XML external entity vulnerability to send specially crafted unauthorized XML requests which will be processed by XML parser. An attacker can use a XML external entity vulnerability for getting unauthorised access to OS filesystem. Install this SAP Security Note to prevent the risks. CVSS Base Score: 7.1 / 10
English References:
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=500633095
https://www.onapsis.com/blog/sap-patch-notes-october-2018
https://erpscan.io/press-center/blog/sap-cyber-threat-intelligence-report-october-2018/
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=503809832
https://www.onapsis.com/blog/sap-security-notes-november-18-mobile-client-side-menace
https://erpscan.io/press-center/blog/sap-cyber-threat-intelligence-report-november-2018/
https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=508559699
https://erpscan.io/press-center/blog/sap-cyber-threat-intelligence-report-december-2018/
The complete list of affected systems / components below:
- Knowledge Management (XMLForms) in SAP NetWeaver, versiones desde la 7.30, 7.31, 7.40 hasta la 7.50
- Proyecto Gardener, versión 0.12.2.
- Project “Gardener”, versión 0.12.4
- SAP_ABA, versiones desde la 7.00 hasta la 7.02, desde la 7.10 hasta la 7.11, desde la 7.30, 7.31, 7.40, 7.50 y 75C hasta la 75D
- SAP ABAP Change and Transport System (CTS), versiones SAP KERNEL 32 NUC, SAP KERNEL 32 Unicode, SAP KERNEL 64 NUC, SAP KERNEL 64 Unicode 7.21, 7.21EXT, 7.22 y 7.22EXT; SAP KERNEL 7.21, 7.22, 7.45, 7.49, 7.53, 7.73, 7.74
- SAP Adaptive Server Enterprise (ASE), versiones 15.7 y 16.0.
- SAP BASIS, versiones 6.40, 7.00, 7.01, 7.02, 7.10, 7.11, 7.20, 7.30, 7.31, 7.40
- SAP Basis (“AS ABAP of SAP NetWeaver” 700 a 750, para 750 posteriormente entregadas como “ABAP Platform”) versiones 7.00 a 7.02, 7.10 a 7.30, 7.31, 7.40, 7.50 a 7.53
- SAP Basis (TREX / BWA installation), versiones desde la 7.0 hasta la 7.02, desde la 710 hasta la 7.11, desde la 7.30, 7.31, 7.40 y 7.50 hasta la 7.53
- SAP Business Client, versión 6.5.
- SAP BusinessObjects BI Platform Server, versiones 4.1 y 4.2
- SAP BusinessObjects Business Intelligence Platform (BIWorkspace) versiones 4.1 y 4.2
- SAP BusinessObjects BI Platform Servers (Software Development Kit), versiones 4.1 y 4.2.
- SAP Business One Service Layer, versión B1_ON_HANA (9.2, 9.3)
- AP Commerce (SAP Hybris Commerce), versiones 6.2, 6.3, 6.4, 6.5, 6.6, 6.7
- SAP Data Services, versión 4.2.
- SAP Disclosure Management, versiones 10.x
- SAP Fiori 1.0 para SAP ERP HCM (Approve Leave Request, versión 2), versión 1.0.
- SAP Fiori Client
- SAP HANA, versiones 1.0 y 2.0.
- SAP HANA Streaming Analytics, versión 2.0
- SAP Marketing, versiones UICUAN (1.20, 1.30, 1.40), SAPSCORE (1.13, 1.14)
- SAP Mobile Secure Android Application, version 6.60.19942.0
- SAP Mobile Secure for Android, versión 6.60.19942.0 SP28 1711
- SAP NetWeaver, versiones – ServerCore (7.11, 7.20, 7.30, 7.31, 7.40, 7.50)
- SAP NetWeaver (Application Server Java Library), versiones 7.20, 7.30, 7.31 y 7.50
- SAP NetWeaver (forums), versiones 7.30, 7.31 y 7.40
- SAP Netweaver Application Server para ABAP, versiones desde 7.0 hasta 7.02, 7.30, 7.31, 7.40 y desde 7.50 hasta 7.53.
- SAP NetWeaver AS ABAP Business Server Pages
- SAP NetWeaver AS Java, versiones ServerCore (7.10, 7.11, 7.20, 7.30, 7.31, 7.40, 7.50)
- SAP Plant Connectivity, versiones 15.0, 15.1 y 15.2.
SAP Records Management, versiones 7.0 a 7.02, 7.10, 7.11, 7.30, 7.31, 7.40, 7.50 y 7.51.