What is Emergency Access Management (EAM)? It is one of the GRC modules that allow end users to step out of their usual roles to perform the tasks necessary to resolve an emergency situation. SAP EAM is designed to assign emergency access in a controlled and auditable process. Originally, Emergency Access was a component that was installed in each of the SAP systems where it was intended to have these accesses.
When SAP made the leap to GRC.10.0, it published SAP EAM Centralized, which, through RFC connections, connects to the target systems. Simplifying the access to the different systems, since, from one system an emergency access can be used in any other.
But organizations were used to work in a decentralized way, through SAP IDEAS, SAP listened to these organizations and published Decentralized EAM.
In Decentralized EAM, the configuration is done centrally in GRC, the master data is handled centrally in GRC and the assignment of Emergency Access is done in GRC, but all this information is automatically replicated in the target systems. Giving organizations the advantage that the person intending to use EAM does not need to have access to GRC.
How EAM works
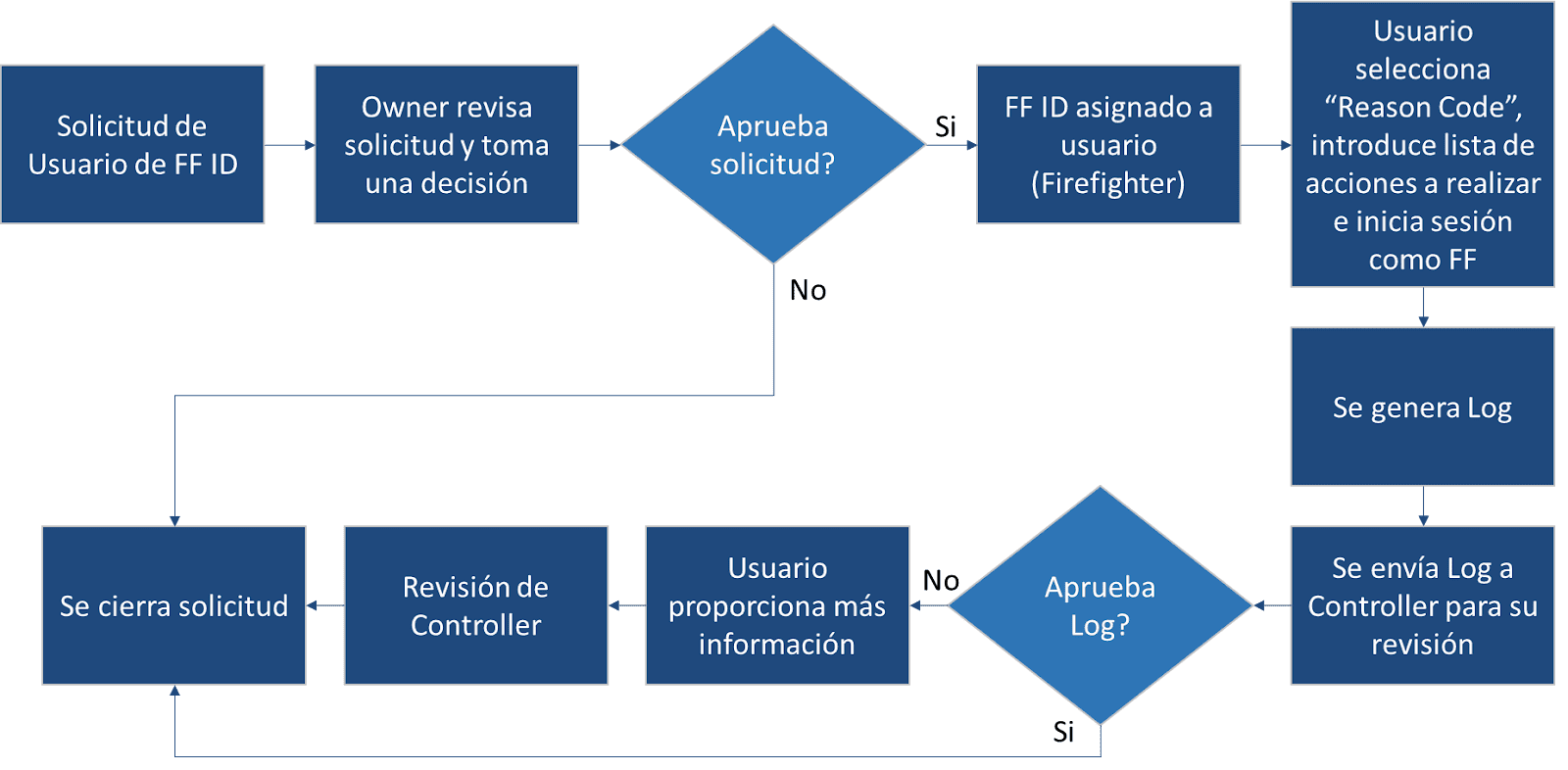
Emergency Access Management (EAM) is an SAP service that addresses major audit issues by separating the most critical authorizations from regular user access. Users can request access to these transactions by submitting a request. Once the user logs in with Firefighter, all user activities are logged while tracking changes and notifying the controller to review the logs at the completion of the session. As a standard outline of the flow that the EAM service follows we would have the following:
There are two types of applications for using Firefighting:
- Firefighter ID-based: in this case, what you do is provide Firefighter authorizations by assigning a Firefighter ID to users. Firefighters use the Emergency Access Management (EAM) panel to access their IDs and systems. Users can access the EAM panel in two ways, depending on whether the type of configuration is:
- Centralized (on the GRC system): you log into the GRC system and use the “GRAC_EAM” transaction to remotely access all authorized satellite (plug-in) systems. In this type, the GRC system and the EAM platform provide a centralized access point to the satellite systems for the Firefighter.
- Decentralized (on the satellite systems): the “GRCPI/GRIA_EAM” transaction is used to perform the Firefighting activities. With this method, as Firefighting is performed locally on each of the satellite systems, you have uninterrupted Firefighter access in case GRC is not available. However, you must ensure that you have accounts on each of the satellite systems. In addition, functions such as assignments and reports are still maintained in the GRC system.
- Based on Firefighter Role: In this case, Firefighter roles are created in the satellite system and assigned to users from the GRC system. The Firefighter logs directly into the satellite system using his user ID and performs the Firefighting activities.
Types of EAM users
In order to use EAM it is necessary to take into account the different types of users that can be found and the roles and functions they perform within the process:
- Owner: Owners are the owners of Firefighter IDs and can assign Firefighter IDs to Firefighters and define Controllers. In addition, they can see the Firefighter IDs assigned to them by the Administrator, although they cannot assign Firefighter IDs to themselves.
- Controller: Controllers monitor Firefighter ID usage by reviewing the Logs report and receiving email notifications of Firefighter ID login events.
- Firefighter: Firefighters can access the Firefighter IDs assigned to them and can perform tasks for which they were previously not authorized. These users use Firefighter ID logins to execute transactions during emergency situations.
- Firefighter ID: This role is used for ID-based Firefighting only. When any user ID is assigned the role “SAP_GRAC_SPM_FFID” it is considered a Firefighter ID (FF ID). In this way, it can later be assigned to a Firefighter user to obtain the necessary permissions to execute transactions and perform emergency tasks, to which it did not have access.
Conclusions
EAM is a GRC module that will allow us to safeguard the most critical accesses of the system, so that they are controlled and audited, without numerous users having them assigned without any control. Additionally, it will also be of great help in cases of emergency or important deployments to have control over the changes that are made or to justify manual changes in productive environments.
In turn, EAM has different modalities, depending on whether you want to work in a centralized or decentralized way, giving different options for a more comfortable and efficient management according to the company’s needs.