One of our company’s greatest success stories has been the implementation of the SAP® GRC Access Control tool for a leading client in the energy sector, becoming the tenth implementation of SAP® GRC Access Control that Inprosec has carried out for its clients.
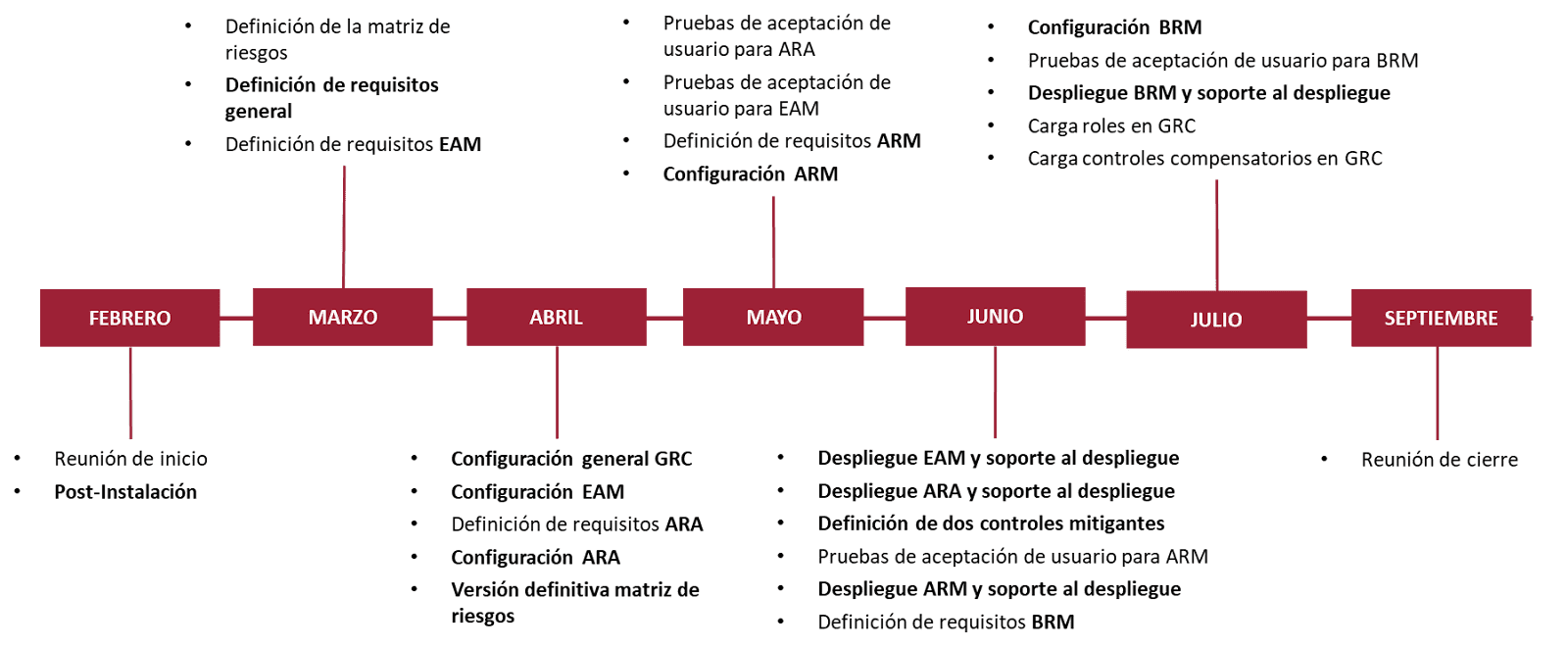
This implementation marked the beginning of the client’s use of the SAP® GRC tool, with an 8-month project starting in February 2024 and concluding in September 2024.
The client we are referring to is a leading group in the energy and chemical sector dedicated to the production of high-tech lubricant bases used in the formulation of synthetic oils. These products are essential for improving engine performance and energy efficiency while also contributing to reducing environmental impact.
The Challenge
The client faced several critical challenges:
- Inefficient or inadequate access management: The lack of an integrated tool to manage user access could result in users accessing information or systems they are not authorized to, increasing the risk of security and compliance issues.
- Segregation of Duties (SoD) risks: The lack of proper controls to prevent SoD conflicts increases the possibility of internal fraud or errors in financial processes, as the same user could perform incompatible tasks (e.g., creating and approving payments).
- Costly and complex audits: Without an automated solution to manage access, audits required much more time and resources.
- Manual role and permission management: The client relied on manual management, which is not only more error-prone but also inefficient, especially in large organizations or those with complex IT structures.
- Poor regulatory compliance: The client must comply with various industry-specific regulations, which require robust, auditable access management and strict control over who has access to what information.
The challenge was to strengthen the client’s internal control framework to improve security and ensure compliance with applicable regulations.
Inprosec Solution
To address these challenges, we implemented SAP GRC Access Control, a modular solution tailored to the client’s specific needs. Each module was customized to cover key areas, providing the following functionalities:
- Access Risk Analysis (ARA): This module allowed us to provide the client with preventive and constant management of access risks to their SAP systems. A customized risk matrix was implemented, including:
- 20 client-specific risks addressing the particularities of their business.
- 30 risks from our IT risk matrix, developed based on best practices and adapted to the client’s environment.
- 220 standard SAP risks, reviewed and adjusted according to our recommendations to meet the client’s security requirements.
Additionally, we assisted the client in the definition of two compensating controls and uploaded other controls previously defined by the client into the system, providing comprehensive access risk management coverage, particularly in cases where Segregation of Duties (SoD) risks could not be eliminated due to operational requirements.
Thanks to ARA, the client can now monitor critical transactions and apply compensating controls proactively, significantly reducing potential security issues.
- Emergency Access Management (EAM): EAM provided secure, auditable control for managing emergency access, activating automatic logs in the audit log, and allowing temporary assignment of critical roles with a secure approval workflow. As a result:
- Users can obtain temporary access in critical situations, ensuring business continuity.
- All activities are logged for subsequent audit.
- Access Request Management (ARM): We implemented this module to automate and customize access request and approval workflows. The client now has an optimized process that allows for:
- More efficient access requests.
- Customized approval workflows adapted to internal policies.
- Password Self Service, enabling users to reset their passwords without intervention from the IT team.
- Business Role Management (BRM): To centralize role and permission management, we implemented BRM, facilitating efficient role administration. With this solution, the client achieved:
- Clear definition and cataloging of roles, aligning them with their business processes.
- Maintaining a solid internal control structure, enabling centralized role management, ensuring users have appropriate access for their responsibilities.
In addition, we worked with the client on the Integration with Active Directory, allowing seamless synchronization of users and groups, simplifying identity management.
Below are the key milestones of the project, providing a clear view of the progress and achievements:
Results
The implementation of SAP GRC AC brought multiple benefits to the client:
- Reduction of access risks: Thanks to the implementation of ARA and the definition of a customized risk matrix, the client can prevent unauthorized access to sensitive information and mitigate Segregation of Duties (SoD) conflicts.
- Optimization of access workflows: ARM allows automation of access request and approval processes, reducing manual effort and enabling employees to focus on higher-value activities.
- Secure emergency access control: The use of EAM enables the client to manage emergency access in a controlled manner, according to internal policies, ensuring security even in critical situations.
- Reduction in IT support burden: With the Password Self Service feature, users can manage their passwords autonomously, reducing dependence on the IT team and improving the end-user experience.
- Seamless integration with Active Directory: User synchronization with Active Directory simplifies identity and access management.
- Improved security and compliance: The client performs more secure access management aligned with regulations, reducing risks through detailed control and clear audit reports.
- More efficient audits: The traceability provided by the tool and the ability to log and audit all access activities simplifies the preparation time for internal and external audits, ensuring transparency and accountability.
- Greater control and visibility of access: The client now has comprehensive visibility over who has access to what information and systems, enabling proactive security risk management and improved data-driven decision-making.
- Flexibility and scalability: The implemented solution is flexible and scalable, allowing the client to adapt to future regulatory and business environment changes.
In sum, the project not only improved access governance and optimized processes but also allows the client to meet regulatory requirements and strengthen their ability to respond to operational and security risks.