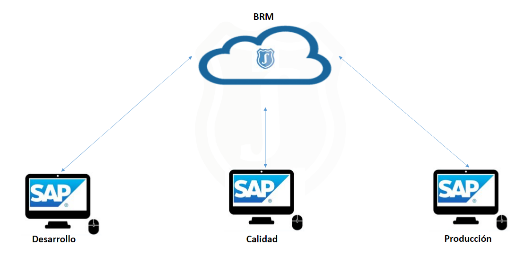
Throughout this article, the virtues and utility of the BRM module in SAP systems will be explored. Far from being just a role repository, BRM stands as the pivotal SAP tool for centralized management of user roles and profiles. This article will delve into the role mapping functionality within the module and its potential applications.
What can BRM contribute?
- Centralized maintenance of roles across all systems and environments, simplifying role nomenclature tracking.
- Adheres to company change management procedures for adjustment and approval processes, minimizing human error risks at various stages.
- Provides an easily auditable workflow, as all change logs and historical information are compiled and consolidated within the application.
- Offers role maintenance options for each environment within a system (Development, Quality, and Production).
Role Assignment in BRM: What Is It?
The BRM module is more than a role repository, boasting standard functionalities worth noting, such as the one we’ll discuss next.
This time, we’ll talk about “Role Mapping” or Role Assignment, a module utility that allows for automatic assignment of a pre-configured role to the same user in designated systems whenever a role is provisioned.
How Is It Done?
Diving into configuration details, the goal is to ensure that when a role is provisioned through GRC, another role in a different system is automatically assigned to the same user.
To achieve this, the first step involves adjusting master data settings in SAP GRC. This requires accessing BRM’s role configuration via the web portal, specifically under “Access Management → Role Management → Role Maintenance,” as depicted in Figure 2. Once inside, one should select a role for this configuration and open it in change administration mode. It’s crucial to select the correct stage, which will be “Definition.”
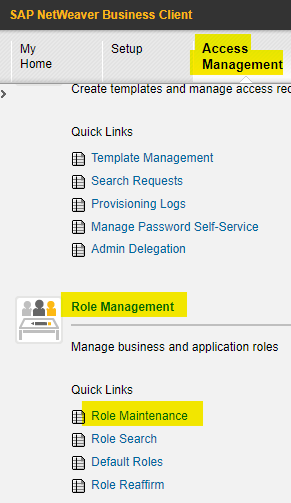
At this stage, the “Role Mapping” function will appear. Here is where the adjustment is made, allowing for the automatic provisioning of as many roles as desired each time this role is assigned to a user by GRC. The following details must be specified.
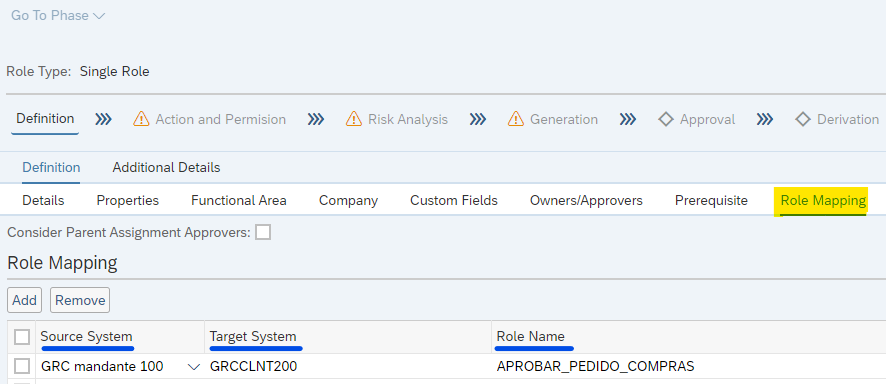
- Source System: The system for which a role will be assigned by GRC, triggering this automatic workflow.
- Destination System: The system for which the designated role will be provisioned once the workflow is initiated.
- Role Name: The technical name of the role to be auto-provisioned must be indicated here.
BRM Use Cases
This automation can result in significant recurring savings and efficiency boosts in certain scenarios. For example, consider a company with a centralized Gateway Fiori system. For this solution to work, users will need not only a role for authorizations in the SAP business system (ECC) but also specific authorizations in the Gateway system to use the Fiori web platform.
In this scenario, if a user requests the Fiori authorization role in the business system, and this role is preconfigured to automatically add the necessary Fiori role in the central Gateway system to the same user, it will save time and reduce incidents related to authorization issues, in addition to IT or SAP security team management time.
Besides the above example, there are other scenarios where this functionality can add value. One such scenario is when a company wants to keep the Quality system (QAS) assignments as close as possible to the Production system (PRD), without resorting to more frequent client copies. This can be achieved through mapping, ensuring that whenever an authorization role is assigned for the production system, the same role is automatically assigned in the quality system to the same user. This simple method can largely maintain homogeneity between the two environments, allowing employees to test business functions with the same permissions in both.
Key Points
- BRM is an SAP GRC module with functionalities extending beyond centralized role repository capabilities.
- The role mapping utility, through a simple and standard adjustment, can enhance the module’s ROI by reducing the recurring manual workload for IT teams.
- Multiple scenarios exist where this configuration can significantly benefit the system, adaptable to various company needs.